In today’s world, we are all browsing websites online and sharing content on a multitude of social media platforms every day. Worldwide social media users exceeded 2 billion back in August 2014, with an adoption rate unlike anything we have seen in history. Social media continues to grow around the world, with active user accounts now equating to roughly 29% of the world’s population. Monthly active user (MAU) figures for the most active social network in each country add up to almost 2.08 billion – a 12% increase since January 2014.
What is Social Media Blacklisting?
Legitimate links on social media platforms are sometimes hijacked by criminals to direct visitors to a website where malware will be automatically downloaded. The more that people share and use social media, the more often these situations will occur. This is why social media platforms have specific security measures to protect their users from being victims of malicious shared content.
In the same way that websites can be blacklisted by Google for having malware hosted on their pages, social media blacklisting occurs when security triggers detect malicious activity, thus placing the infected links on their internal blacklist. Sometimes they can match the URL with the help of an external blacklist authority, such as McAfee, Google, Web of Trust, or Websense.
Other Types of Blacklists
The initial reaction to hearing the term “blacklist” is to think that whoever is on the list is restricted from visiting a certain area or performing certain activities. In the case of websites and social media links, this means that that the content is labeled as dangerous to visitors. This could be due to spam or malware being served from its pages. Our team deals with this kind of thing every day, providing blacklist removal for website owners along with the complete malware cleanup and protection.
You may have encountered the term “blacklisting” in conjunction with email marketing. As a mass-email sender, your reputation and content choices can get your IP blacklisted by major email service providers. If they believe you are sending spam, or violating CAN-SPAM and similar legislation, it can be very difficult to recover from being blacklisted for email abuse.
Social media blacklisting is still a recent phenomenon. As criminals find new ways to use social media, we’ll see an evolution in the protection measures taken against them.
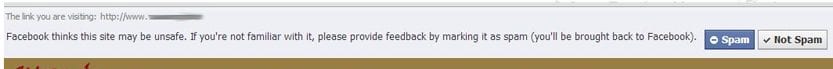
In 2008, Facebook launched a security system called “the link shim” that checks the URL whenever a link is clicked to check the destination. If it is on a blacklist, then a warning pops up notifying the user he could be headed to a malicious website:
Since the link shim checks URLs at click time as opposed to display time, Facebook can prevent users from accessing malicious content. In addition to its internal and external blacklists, Facebook uses advanced machine learning classifiers to check the authenticity of the sender as well as other inputs. Malicious URLs that have been sent over e-mail are also blocked since all links to non-facebook.com URLs in e-mail are rewritten to first go through the link shim.
The Facebook Security page provides constant updates. You can get the latest information about how to safely use your Facebook profile and pages, as well as a few techniques Facebook employs to protect users from being targets of malware sharing activities.
Although it is good to know that you’re protected by the social platform, offer your help by always reporting any suspicious links you may find on your timeline. This crowd-sourcing effort helps protect other users as well.
The microblogging platform is often the target of malicious activity for a few reasons:
- Tweets can be easily scheduled automatically by malicious or hacked user accounts.
- With the rise of URL shortening, users are used to not seeing the full landing URL
- Its explosion in global popularity.
Many users are tempted with a cleverly worded message, a photo, and a link. They click it without thinking.
Back in 2009, Twitter started using Google’s list of suspected phishing and malware pages to filter URLs. Along with Twitter’s own internal security mechanisms, the Google Safe Browsing API allows client applications to check URLs against an updated Google blacklist.
Once a website is blacklisted on Google, this is reported to Twitter’s platform and users are prevented from reaching the infected websites via Twitter.
If the URL of the site you manage is being blocked, and you are completely sure that your site is not being used for abuse on Twitter, you can contact the Twitter Support team. In the Problematic link field, insert the extended URL of the link you are having issues with, rather than a shortened version. You can find extensive information on Twitter’s Security measures on unsafe links here.
Malware on LinkedIn often takes the form of phishing or spam campaigns. Malicious software, or “malware” refers to a variety of software created for the purpose of harming your computer. This harm can include disrupting your computer’s normal operations, like making it run slower, causing abrupt pop-ups, or stealing your personal information. Viruses are a particular form of malware that aim to spread from computer to computer with the intention of exploiting your computer’s data or deleting it.
LinkedIn is taking specific steps in protecting their users, as well as teaching them important aspects of online security. Here’s what they say:
- We scan uploaded files for malware and viruses. If we identify an infected file or image, we will prevent the download from occurring and keep it from infecting your computer.
- We include your full first and last name in the footer of all our messages, as well as your current professional headline so you can better identify legitimate LinkedIn communications. Any messages claiming to be from LinkedIn without our security footer should be discarded.
- We will never ask you to download software from any of our messages, nor will we ask you to provide sensitive information such as a password or social security number via email.
Is Social Media Safe?
Any online membership website has its fair share of security risks and there’s always a potential of being infected with malware while browsing both websites and social media venues. We cannot say that any social platform is safer than a website or vice-versa.
But we can never stress enough the importance of having an informed and educated security posture online! Being informed means protecting yourself before allowing any attacker to start their attack.
Some Takeaways
- Make sure you are aware of the risks before connecting to any major social media venue and creating a post. Each platform has security measures in place, and information for you to stay up-to-date with privacy and security issues. Read those pages, they are put together with the help of dedicated security analysts, using thousands of man hours, just to protect you.
- Social media blacklisting is not something to be afraid of if you’re security conscious. That list is not meant to harm you or your business; it is there to protect you, so make sure you report any suspicious links or content using the specified methods for each social venue. Giving a helping hand is also helping yourself.
- Want to check a suspicious bit.ly shortened link? Before you share it further, copy and paste the bit.ly link into your browser address bar, add a “+” after it and hit enter. The real target URL will reveal itself together with additional information about the link: when it was generated, who shared it, and where it was shared. So in the example of http://bit.ly/1PlZm6L, we would add “+”, thus creating http://bit.ly/1PlZm6L+. The real target URL in this case is https://blog.sucuri.net/2015/04/how-to-create-a-website-backup-strategy.html
- Social media platforms leverage security experts that know a lot about security, and work with partners to expand their knowledge. If there is a warning that some content may be malicious, you should take the warning seriously.
Have you experienced any social media blacklisting on your website? Please do leave a comment detailing your experience. Let others learn from what you went through, in an effort to educate future users into being more careful and trust the systems put in place to protect them. Then go out there and share safely!