Security Risk: Dangerous
Exploitation Level: Easy/Remote
DREAD Score: 7/10
Vulnerability: Stored XSS
Patched Version: Magento CE: 1.9,2.3, Magento EE: 1.14.2.3
During our regular research audits for our Cloud-based WAF, we discovered a Stored XSS vulnerability affecting the Magento platform that can be easily exploited remotely. We notified the Magento team and worked with them to get it fixed.
Vulnerability Disclosure Timeline:
- November 10th, 2015 – Bug discovered, initial report to Magento’s security team
- December 1st, 2015 – No response from Magento. Requested confirmation of our previous email.
- December 1st, 2015 – Magento acknowledge receipt of the report.
- January 7th, 2016 – Request an ETA, been 2 months since original report.
- January 11th, 2016 – Magento answers that the patch is ready, but no ETA available.
- January 20th, 2016 – Magento releases patch bundle SUPEE-7405, which fixes the issue
- January 22th, 2016 – Sucuri Public Disclosure of Vulnerability.
Am I At Risk?
This vulnerability affects almost every install of Magento CE <1.9.2.3 and Magento EE <1.14.2.3. The buggy snippet is located inside Magento core libraries, more specifically within the administrator’s backend. Unless you’re behind a WAF or you have a very heavily modified administration panel, you’re at risk.
As this is a Stored XSS vulnerability, this issue could be used by attackers to take over your site, create new administrator accounts, steal client informations, anything a legitimate administrator account is allowed to do.
Technical Details
The issue exists within: app/design/adminhtml/default/default/template/sales/order/view/info.phtml:
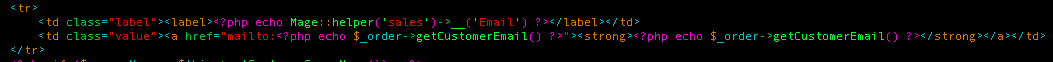
As you can see from the above snippet, the template appends the getCustomerEmail method’s return value to the administration panel. This snippet looked similar to what we found in a bug within the WordPress Jetpack plugin a couple months ago. With that in mind, we investigated the type of validation mechanisms Magento used to check whether a given string is an email or not.
This is what we found:
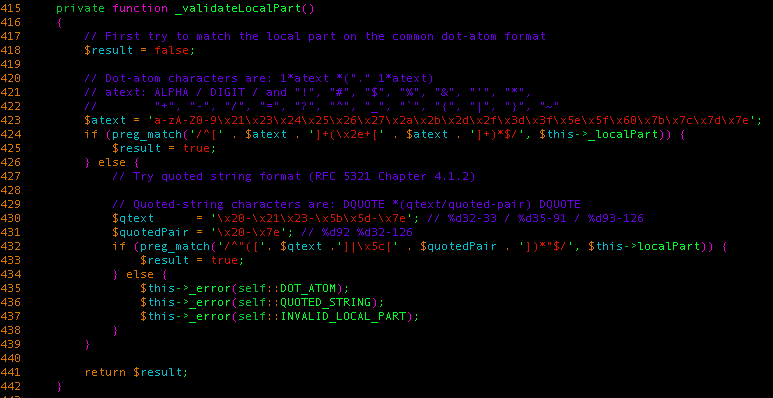
It accepts two different forms of emails:
- Regular ones, similar to what we had found in WordPress (no double quotes, no ‘<‘ sign, etc.)
- Quoted string format, which accepts pretty much any printable characters (except for space characters, where it only allows regular spaces to be used) as long as it’s surrounded by two double-quotes
This meant that, in theory, we could use an email like “><script>alert(1);</script>”@sucuri.net as our client account’s email, submit an order and see what happens when an administrator checks our order in the administration panel .
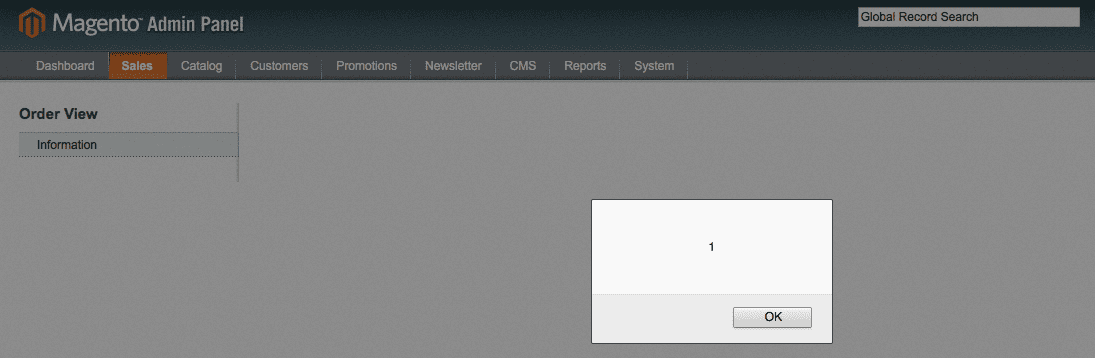
We were right! We just triggered an XSS in Magento Core.
Patch As Soon As Possible
If you’re using a vulnerable version of Magento, update/patch as soon as possible! In the event where you can not, we strongly recommend leveraging our Website Firewall or equivalent technology to get it patched virtually.











15 comments
I tried using “>alert(1);”@sucuri.net when creating a new account to test my site and I get this message “Please enter a valid email address. For example johndoe@domain.com.”
My site is not yet patched either, or does this only work when creating an order?
I tried also, it showed the same error message, I believe the issue is the backend validation.
im getting an error
the part follow by ‘@’ sould not cointain a symbol “”
using the mentioned example during registration
“>alert(1);”@email.com
i never update my site
what am i doing wrong ? any idles ?
This is what I did to replicate.
1. Copy paste the email script on notepad. Then delete the double quote and type it manually. Now go to register page on frontend and register with the edited email Id. Before clicking submit remove the javascript validatation for email field.
2. You can do this just by removing the all the class names from the input tag and change the input type to text and submit.
3 .Now go to admin panel and create an order for the created customer. Repeat step 2 before submitting order.
4. After saving the you can see alert box on the screen.
type the quotes manually and not by copy&paste, cause the format is broken. And yes it is the backend validiation. We implemented our own security logic to filter script tags customer input data, so we hadn’t the problem like other shops. very simple 😉
This ist working for me too. Can anyone post working XSS Vector?
This is what I did to replicate.
1. Copy paste the email script on
notepad. Then delete the double quote and type it manually. Now go to
register page on frontend and register with the edited email Id. Before
clicking submit remove the javascript validatation for email field.
2. You can do this just by removing the all the class names from the input tag and change the input type to text and submit.
3 .Now go to admin panel and create an order for the created customer. Repeat step 2 before submitting order.
4. After saving the you can see alert box on the screen
Try modify the “value=” in the input. I think this input have a “type=”email”” or another javacript. Change the type to “text” and try disable the javascript.
Very cool!
Magento is pretty much irresponsible when it comes to security. No matter where you report/email – support dept, security team, brand evangelist – you never get any response until you publicly disclose the bug and get immediate emails from their legal dept 😀
You would hope that being an ecommerce platform they would understand they are a prime target and act responsibly :/
If you ever have ANY problems communicating, please let me know at ben@magento.com
So, it was you guys! Great job finding this 🙂
Please Someone Post working XSS Vector.
Nice job
Comments are closed.