Exploitation Level: Easy/Remote
DREAD Score: 6/10
Vulnerability: Stored XSS
Patched Version: bbPress 2.5.9
During regular research audits of our Sucuri Firewall, we discovered a Stored XSS vulnerability affecting the bbPress plugin for WordPress which is currently installed on 300,000 live websites – one of them being the popular wordpress.org support forum.
Vulnerability Disclosure Timeline:
- April 12th, 2016 – Bug discovered, initial report to the bbPress team
- May 2nd, 2016 – bbPress team announces security release
- May 3rd, 2016 – Sucuri releases disclosure
Are You At Risk?
This bug is present on every default install of bbPress < 2.5.9, so yes, you’re probably at risk. The vulnerability allows any malicious users participating on the forum to insert malicious Javascript snippets into posts and replies. This is especially dangerous considering the social nature of forums.
As a Cross-Site Scripting (XSS) vulnerability, it could allow this user to hijack other user accounts, perform actions on their behalf (like administrators, moderators, etc.) to escalate its user’s privileges.
Technical Details
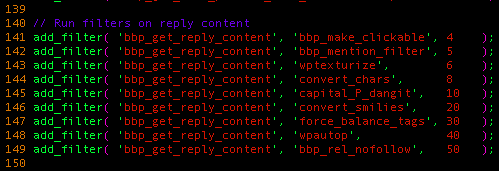
All posts and replies are sanitized by the WordPress function wp_kses(), which acts as a whitelist sanitization function. This means it only allows approved HTML tags and their associated whitelisted attributes (and URL protocol, for attributes like href and src) through the filtering engine. After this happens, the resulting string is passed down to the following list of filters, hooked by bbPress:
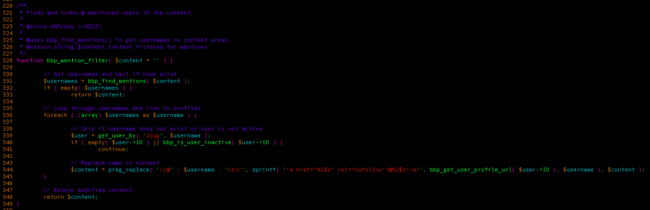
We found the bbp_mention_filter function interesting, as it is one of the few functions that doesn’t come from WordPress.
This code does the following:
- It searches for mentions in the post by calling the bbp_find_mentions, returning every match from the following regex: /[@]+([A-Za-z0-9-_\.@]+)\b/
- For each of these matches, check if it corresponds to a known user, and whether they are active or not.
- Once that is done, it will replace these mentions with a hyperlink HTML tag, linking to the user’s profile page.
It doesn’t check if the mentions found are already located inside an HTML tag’s attribute; therefore if a user with the name ‘test’ sends a reply containing a hyperlink tag whose href attribute is set to @test, it would break the hyperlink tag.
To better illustrate, this:
<a href="@test">link</a>
… would become:
<a href="<a href="http://targetsite/test/profile/" rel="nofollow">test</a>">link</a>
This breaks the hyperlink tag’s double-quote sequence, allowing an attacker to insert arbitrary event handlers in it (similar to the Akismet disclosure) in order to execute malicious Javascript code.
Update as Soon as Possible
If you’re using a vulnerable version of this plugin, yes, update as soon as possible! In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to get it patched virtually.







![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)



7 comments
So if I navigate to Plugins in the WP admin and bbPress is not on my list, I’m safe?
Yes. 🙂
Apparently no one bothered to let bbPress in on the update as they are still pushing out the infected 2.5.9
Hi @alpinevp:disqus
This is inaccurate, bbPress pushed a release yesterday: https://bbpress.org/blog/2016/05/bbpress-2-5-9/
The infected versions are < 2.5.9, not 2.5.9
Thanks
LOL 😀 guys, this issue is not xss. This is HTML attribute escaping bug whithout new attribute injection. Its not exploitable. Ashamed to make such stuff.
Just because you can’t make it trigger, doesn’t mean it is not there.
Yes, it is an XSS and yes, we sent a PoC to the bbpress team to confirm. And no, we won’t share with you, but the diff and details are there to make it work.
thanks,
someone will write poc by himself,someone just wait
Comments are closed.