If you are doing website development and have a local repository, or store website backups on your computer, you should strongly consider encrypting these sensitive files.
In the event that your computer is compromised, the encrypted container prevents an attacker from gaining access to your website (via database configuration files) and other private data.
This guide shows you how to install and use VeraCrypt – a free, open-source encryption tool that works on all operating systems, previously known as TrueCrypt. The program has been audited by security professionals and is trusted as a leading solution in the infosec community.
Download VeraCrypt
The first step is to visit the VeraCrypt website to download and install the program for the operating system you are using.
As with any executable program downloaded from the internet, you can verify that the file you downloaded from the website matches the official digital signature of the application. This ensures the integrity of the application in case hackers interfered with the download in some way.
VeraCrypt Setup Process
Once you download VeraCrypt and open the installer:
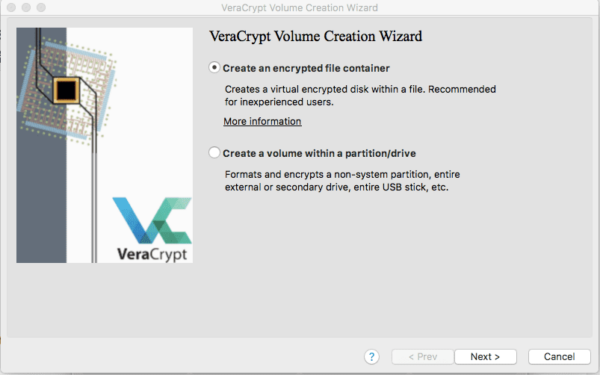
- Click on Create Volume
- Select the Create an encrypted file container option and click Next.
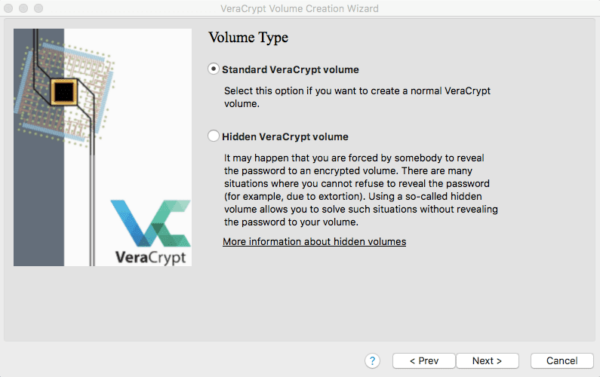
- Select the Standard VeraCrypt volume and click Next.
It’s worth noting that the second option here allows you to create a fake, hidden volume. This is useful for scenarios where an attacker may force you to reveal your password. If this option interests you, there is more information in the dialog box.
Naming the VeraCrypt Container
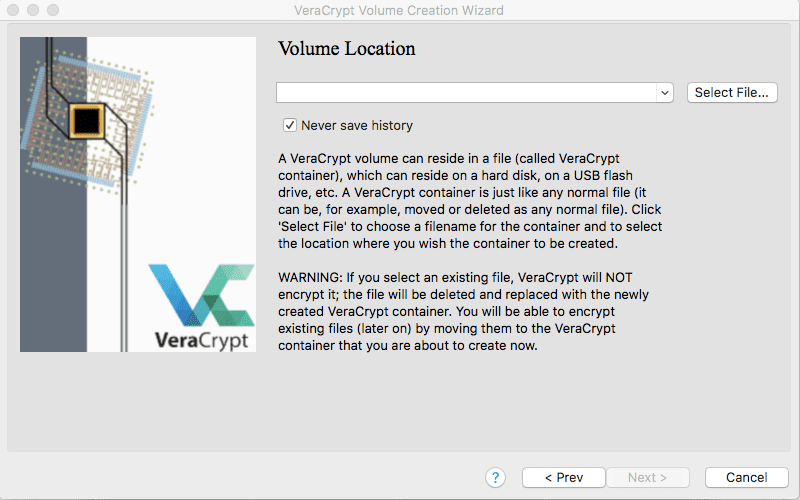
On the next screen, you select the file name for the encrypted file container and the location where you want that encrypted file container to be saved.
For security purposes, I recommend using a file name that doesn’t indicate that the contents are sensitive and valuable to attackers. A generic file name – for example, To do list – may slip past the attention of a potential attacker.
For the storage location, keep in mind you don’t have to store this on your hard drive. You could use a flash drive or external hard drive instead.
To pick the file name and storage location:
- Click on Select File, enter the desired file name in the Save As section.
- Select the location you want to save the file under the Where option.
- Click on Save, and then click Next.
Encryption Container Options
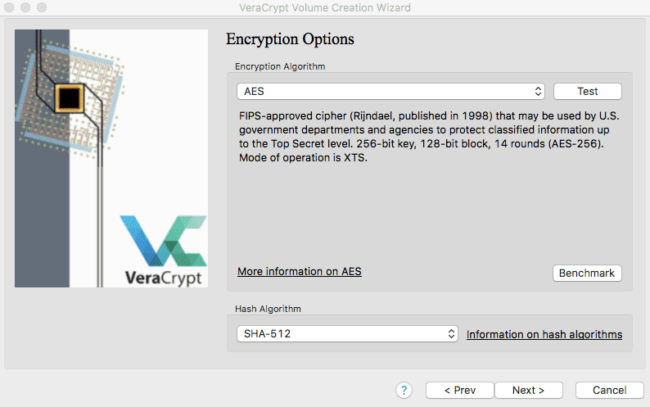
The next section involves selecting the encryption options. These are the methods used to scramble your data and make it impossible for an attacker to break in without knowing the password to your container.
You can select another algorithm and hash if you want to, but I would recommend sticking with the default options of AES for the algorithm and SHA-512 for the hash.
After choosing your algorithm and hash, you can click on Next.
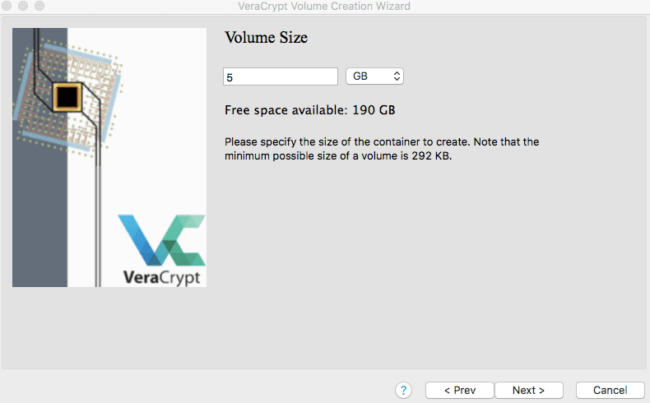
You now will select the size (in MB or GB) to allocate for the encrypted file container. Unless you have a very large site or database, a few gigabytes should be plenty of space.
You may want to check the size of your existing files before making this decision. You should also consider adding more space based on how many files you plan to add over time – otherwise, you will have to create a new, larger container and start over.
Locking Up the VeraCrypt Container
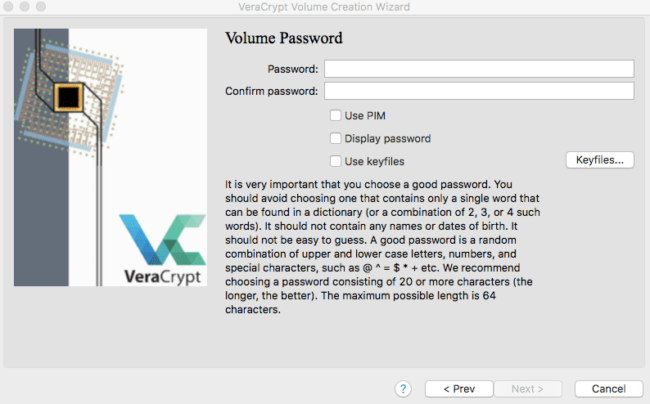
In this section, you will create a password that you will use to unlock the encrypted file container.
I recommend creating a password that is at least thirty-two characters, contains lowercase letters, uppercase letters, numbers, and special characters that is randomly generated and not used anywhere else.
Based on your personal threat model, you will need to decide whether to store this password in a password manager, or your own memory.
You also have the option to use a keyfile or multiple keyfiles. For most cases, a secure randomly generated password should be secure enough.
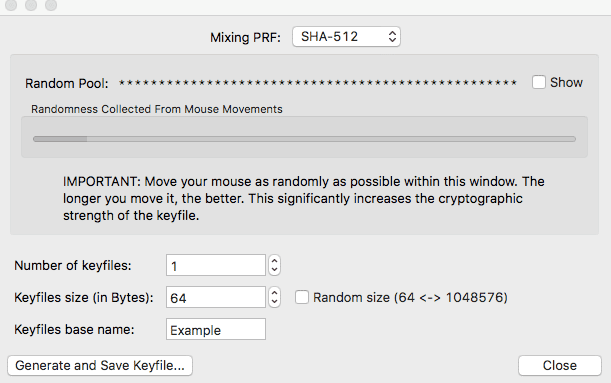
Using a Keyfile
However, if your risk tolerance is lower, you may use a keyfile for additional security.
A keyfile is a piece of data that will be needed in addition to the password. I use a keyfile for some containers personally, and when I do, I click on Keyfiles and select Generate Random Keyfile and use the default options.
After moving my mouse within the window to generate a significant amount of entropy, I save the keyfile to a flash drive. I only use this USB stick to store my keyfiles, and I only insert it into the USB slot on my computer when unlocking a VeraCrypt file container – then immediately remove it to reduce the risk of its contents being compromised.
Final Settings
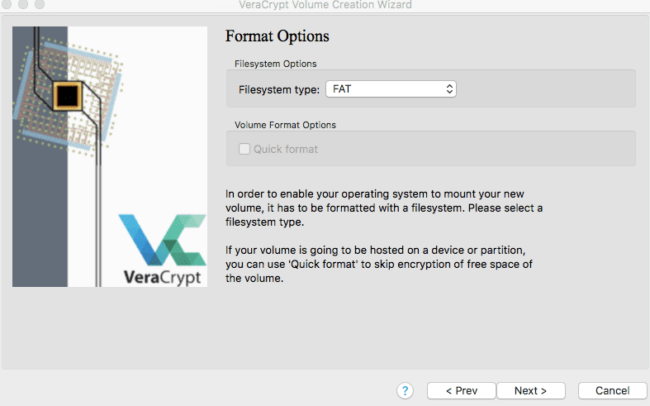
For the next section, you will most likely not need to change the defaults unless you have any website files that are larger than 4 gigabytes. If you are storing large files in this container, you will want to select the second option.

Next, you will select the file system type. The default option should be fine unless you are adding the container to an external device that you plan to use with another operating system.
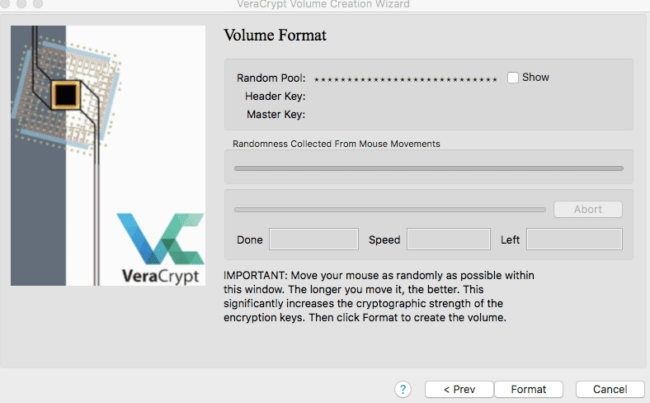
For the last section, you will want to move your mouse around randomly within the window until the section is completely filled with blue underneath the Randomness Collected From Mouse Movements section. Once complete, you can then click on Format.
As with the keyfile option, this action adds strength to the encryption, making it harder to break into without access to your password.
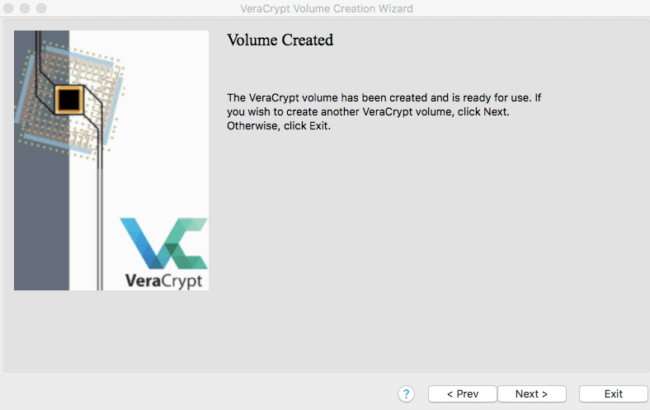
Once the process completes for creating the encrypted file container volume you should see a screen like this letting you know it is complete.
Now that you have this encrypted container, you can find it where you saved it in the first few steps, unlock it with your password (and optional keyfile), and use it to securely store sensitive data, such as your website files and database.
Conclusion
VeraCrypt and other disk encryption software allow you to protect sensitive information from being stolen when your environment is compromised. In security, we suggest that you always behave as if your system is already hacked.
Though everyone must choose their tolerance for risk, taking the time to properly isolate and protect your data will effectively reduce the potential damage a hacker can do when your computer is compromised.
In my recent series on personal security, I suggest using VeraCrypt for a number of different purposes. Encryption is an important element of cybersecurity and I hope this guide encourages more users to adopt a better security posture when it comes to storing sensitive information.