In the first post of this series, we talked about the practices that will optimize your site and increase its resilience to DDoS attacks. In the second post, we focused on caching best practices that can reduce the chances of a DDoS attack taking down your site. Today, we are going to emphasize the importance of having a Web Application Firewall.
What is a Web Application Firewall?
A web application firewall (WAF) is a firewall that filters, monitors, and blocks HTTP/HTTPS traffic to and from a web application. A WAF is a layer of protection that sits between a website and the traffic it receives.
Why Do I Need a WAF?
Regardless of how you decide to deploy a WAF, it’s a must-have on your security list. A good WAF is able to protect your application against:
- SQL injections
- Cross-site scripting (XSS)
- Remote code execution (RCE)
- RFU
- other well-known attacks
When deployed within a powerful network and together with an IDS (Intrusion Detection System), the WAF is also able to mitigate DDoS attacks and speed your website.
How to Choose a WAF
The best way to define which WAF works the best for your application is to analyze the protection efficiency, the cost, and the team available to operate it.
The first thing you need to have on a checklist is to make sure the WAF has an effective virtual patching for your CMS or platforms.
If a security patch is released, but you’re unable to update, your website becomes an easy target for hackers. Virtual patching is a WAF feature designed to virtually patch your application and prevent new exploits from damaging it.
This year, our WAF blocked 100% of zero-day vulnerabilities. This means that even new breaches with no fixes can be prevented from damaging your website if it is behind the Sucuri WAF.
How to Deploy a WAF
How you deploy the WAF is also important. When choosing a hardware WAF to handle all requests to your application,, some solutions will come with a few hidden costs, such as
- computer power
- bandwidth usage
- storage
- ability to keep up with the new types of attacks
- ability to handle specific types of attacks
- experts to manage the WAF operation
Now, if you choose a cloud-based WAF, such as the Sucuri Firewall, the time to implement it and the financial costs will decrease immensely. The Sucuri WAF runs on top of a high-performance Anycast network infrastructure with multiple data centers ensuring physical redundancy to the WAF, giving you:
- a powerful intrusion detection system (IDS),
- a content delivery network (CDN),
- a free SSL certificate,
- HTTP/2, and
- 24/7 technical support.
To implement our WAF, all you need to do is change your DNS A records (that points your domain to your web server) so it points to our firewall IP address. Or you can change your DNS Name Server Records to ours. By doing this, all your site’s traffic will be redirected to Sucuri so we can filter malicious traffic while allowing legitimate traffic to proceed to your site.
Be aware that if you’re using a CDN, it’s not in front of your WAF. Usually, due to bandwidth exhaustion attacks, most cloud WAF providers have a built-in CDN within the network. This prevents the need of an external CDN that could decrease the protection efficiency. Nonetheless, the Sucuri WAF will work with any CDN you might already use on your website.
Don’t Get Exposed
Once you have a WAF protecting your application, the next step is to “seal” the hosting set up to allow only connections coming through the WAF. This can be easily accomplished by using “bypass prevention rules” such as the ones in our Knowledge Base article.
Block Non-WAF Connections
You can also instruct your web server software to block non-WAF connections. However, the web server software will use more resources to deny a connection than the operating system level firewall would.
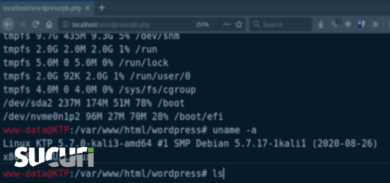
If you are on a dedicated server, use the OS firewall to block connections not coming from the WAF at the network level. On a Linux-based server, for example, this can be accomplished by using iptables.
Use a Virtual Private Network (VPN)
As you may already know, it’s advisable to use a virtual private network (VPN). This ensures your connection is encrypted, especially on public hotspots. It can also benefit preventing exposure of your web server traffic.
Instead of allowing anyone to connect to your server via FTP/SFTP/SSH, restrict these services to your VPN IP only by using your server software firewall.
Most VPN providers offer the option to have a static IP address. Therefore, as long as you’re connected to your VPN, regardless of where you are in the world, your connection will always be encrypted and have the same IP address.
Have a Static IP Address
Having a static IP address can also assist in decreasing your website’s attack surface. By using a WAF, you can blacklist specific areas of your website to non-whitelisted IP addresses, as well as narrow the number of countries allowed to interact (POST) on your website.
As you would have whitelisted your VPN IP address, if you’re traveling to a country you have blocked on the WAF or accessing a blacklisted area on your website, you would still be able to connect to your website normally.
Your VPN IP address would belong to another country and be whitelisted. As long as your VPN has a static IP address, you would have the same IP address regardless where you are in the world and you would be whitelisted already.
Update Your Code
Outdated applications are vulnerable to new exploits available to the public. When you use a WAF that has virtual patching, the chances of your website being attacked decreases. But taking precautionary measures is never too much.
A vulnerability on a specific part of your application can allow a single request to bring your server down. Hacked websites are also used to DDoS other websites. This not only damages DDoS targets but the compromised website’s ecosystem. The website attacking other websites now has fewer resources to process legit requests.
Make sure your website has all updates available installed and avoid being caught by surprise.
Conclusion
In this series, we have covered some of the best practices about how to improve website resilience for DDoS attacks.
If you are looking for a website security solution, our security platform has monitoring, response to attacks and hacks as well as a powerful Web Application Firewall.