These days, the majority of store owners opt-in for the easiest closed-source ecommerce platform options.
For the most part, these platforms typically allow users to customize a template, as well as add images, videos, and some external content via apps in order to enhance their store and automate some tasks. However, they don’t allow users to upload any files, view, or edit any of the code used to run the store — other than the template they are using.
Closed Source E-commerce Platforms
Closed source ecommerce platforms are generally more secure, but it’s still possible for vulnerabilities to exist and be exploited by hackers. In the particular case of a recent remediation investigation, a third-party app was responsible for the website compromise.
Website Redirection
The initial symptoms of the website infection included random redirection of mobile users. Since it happened randomly (only once per IP and mobile users exclusively) it was difficult to replicate. After further investigation, we found snippets of JavaScript initiating the redirect:
![hxxps://emailcollector[.]supernovaapps[.]pw/shopify/resources/smartpopup.js?project_id=29&shop=skeleton-optics.myshopify.com](https://blog.sucuri.net/wp-content/uploads/2019/05/Screen-Shot-2019-05-28-at-15.59.15-600x492.png)
We checked the domain emailcollector[.]supernovaapps[.]pw and discovered that at some point it redirected to 141.8.226.58. This is a shared server that also hosts Zeus C&C and Ransomware C&C (Command and Control) account servers.
![UrlQuery report for emailcollector[.]supernovaapps[.]pw](https://blog.sucuri.net/wp-content/uploads/2019/05/Screen-Shot-2019-05-28-at-17.13.54-600x233.png)
The SuperNova Email Collector App
The app responsible for this redirect is called “SuperNova Email Collector”. It had already been removed from the ecommerce platforms app store, but not from the stores that had previously downloaded it.
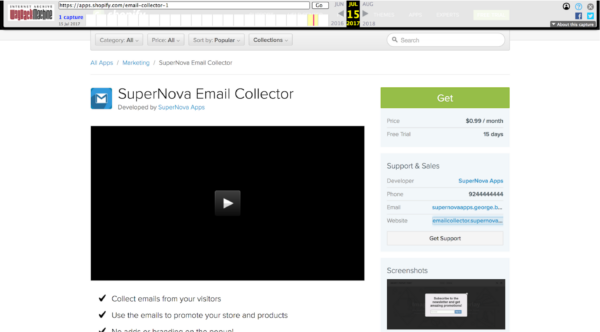
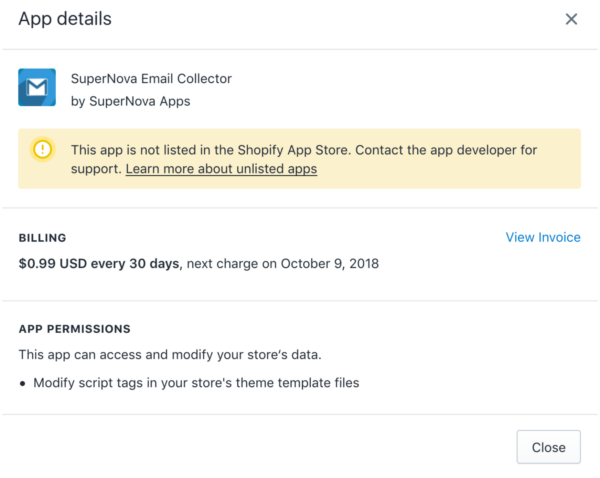
Description of the SuperNova Email Collector in Shopify App Store
The user likely never suspected that an app from the official ecommerce app store would go rogue and redirect users on their website. While the app has since been removed from the app store, we suspect users were never notified to remove it from their CMS.
As you can see, functional applications can be deprecated and become the source of malware. It was probably abandoned by the developers and the domain expired. We’ve seen this happen before with other plugins and apps. It could have also been sold to a third party after enough users had the app on their stores.
Conclusion
We highly recommend checking if any apps associated with your ecommerce site might have been removed from the app store. If so, we encourage you to remove them from your site. Additionally, you should check for emails from your ecommerce provider in the event that they have notified you of apps that may have been removed due to malware or have otherwise broken the terms of service.
In some cases, apps are compromised — but stolen login credentials can also lead to malware being added to the site. Even malware that exists on the PC used to edit the website can lead to an infection. Read the following Shopify threads if you are interested in knowing more:
If you are looking for a website security solution, Sucuri has a complete platform with monitoring, incident response, and website protection.