When the world shut their doors and began spending more time online, hackers saw a clear opportunity. The costs of data breaches continue to rise, and attacks are becoming harder to detect. Attackers are becoming more sophisticated and creative. According to a 2020 report by IBM, it took an average of 228 days to identify a breach. Businesses are taking a closer look at their firewall’s capabilities and considering mixing and matching technologies to cover new security gaps.
If you’re wondering what the differences are between your traditional network firewall (the most common firewall) and the newer Web Application Firewall (WAF), this article is for you.

Media Source: Giphy
A Network Firewall acts as a boundary providing protection between internal and external network traffic.
It has preset rules that define the traffic allowed on the network. It then looks at source and destination IP addresses and the ports to determine if the incoming and outgoing data packets are authorized or not.
A Web Application Firewall (WAF) specializes in protecting website applications and APIs. A WAF protects HTTP(s) traffic and applications in the network’s internet-facing zones.
The WAF and Network Firewall serve different purposes and protect different network layers.
Physical Differences
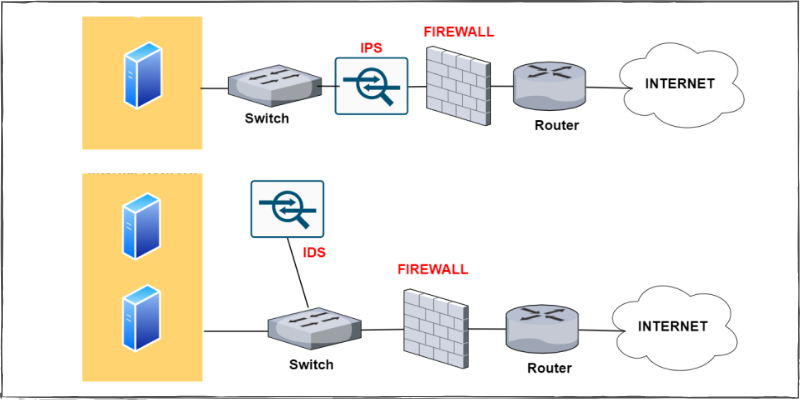
Media Source: networkstraining.com
The WAF and Network Firewall sit in different places on the network. The Network Firewall is located at the edge of the network while the WAF is located directly between the user and the web server.
Source: networkstraining.com
Functional Differences
How It Works
The WAF protects websites and APIs. It is configured as a reverse proxy and examines all HTTP(s) requests before they reach the web server. It blocks or tests irregular traffic with CAPTCHA tests to make sure the traffic is coming from a human and not a bot.
The Network Firewall protects the network perimeter and filters traffic using protocol information. You can set rules to permit traffic based on things like IP ranges, ports, ICMP (Internet Control Message Protocol) types etc. It monitors the activity from the opening of a connection, until it is closed.
| WAF | Firewall | |
| Strengths | Customizable rules, conditional filtering, limit upload sizes, can decrypt and inspect SSL traffic, IDS and IPS can be integrated, visibility into packet data | Blocks unauthorized protocols, ports and IP addresses, Provides VPN support |
| Weaknesses | False positives and false negatives, not great at stopping zero-day exploits, not enough protection for publicly accessed websites. Shared servers can cause reinfections. | Only has Accept / Reject Rules, cannot decrypt traffic, slows down when inspecting SSL, IDS and IPS are deployed separately, not great at stopping “client-side” attacks, only has visibility into packet headers creating vulnerability for SQL injection attack |
Their functional differences are also illustrated in the OSI Model, a universal set of 7 abstract layers that describe how networking systems communicate and operate. The WAF and Network Firewall address different network layers.
The WAF focus on Layer 7 (application)
The Network Firewall focuses on Layer 3 & 4 (network and transport),
| Layer 7 | Application | Human-computer interaction layer, where apps access network services |
| Layer 6 | Presentation | Where data formatting and encryption occur |
| Layer 5 | Session | Controls ports and sessions and maintains connections |
| Layer 4 | Transport | Transmits data using TCP and UDP and other protocols |
| Layer 3 | Network | Determines the path the data takes |
| Level 2 | Data Link | Defines how the data is formatted on the network |
| Level 1 | Physical | Transmission of raw bit stream over a physical medium |
Operational Differences
They Fend Off Different Attacks
WAFs and Network Firewalls address different threats.
Network Firewalls defend against
- Unauthorized network access
- Man in the Middle Attacks
- Privilege Escalations
- DDoS attacks at the network level
WAFs defend against
- SQL Injection
- Cross-site-scripting (XSS)
- Cross-site forgery
- DDoS attacks at the website level
- Directory traversal
They Run Different Algorithms
Firewalls run Stateless/Stateful Inspection algorithms, Packet-Filtering algorithms, and Proxy algorithms.
WAF runs Signature-Based algorithms, Heuristics algorithms, and Anomaly Detection algorithms.
Deployment Options
The WAF and firewall are set with rules that block or allow traffic accordingly. Depending on the type of deployment you have, it may come preloaded with these rules, or you may create the rules yourself.
Network- based
A hardware-based deployment gets installed locally on the local area network (LAN). This allows for optimal latency, and creation of custom protocols and rules. It is the most expensive because of hardware installation, physical storage requirements, and maintenance.
Host-based
This software-based deployment iis very similar to a Network-based deployment but the Firewall is directly integrated into the application code. These deployments allow for customizable security rules, but require several hours in implementation.
There is zero latency because the firewall is installed directly into the application. However, it uses significant resources from the local server which can slow down the web app if there is not enough capacity or space.
Cloud-based
A cloud-based deployment is installed entirely in the cloud and is usually managed by a third party as a SaaS product. This option is the most affordable of the 3 types. The setup is easy and only requires a DNS change.
Ask Your Vendor
Make sure to ask questions of the vendor before agreeing to your firewall or WAF. There may even be a comprehensive package that includes the functionality of both. You’ll want to know:
- What does it protect against?
- What features are included?
- If it is a Network Firewall look for:
- VPN (encrypts all traffic) or Proxy Server (changes IP address to mask the traffic’s origin)
- Stateful Inspection or Deep Packet Inspection (DPI) which can look inside the packet at its content and at its headers
- If it is a WAF, look for:
- Content Delivery Network (CDN) – caches website and boosts speeds
- API endpoint security
- Out-of-the-box PCI DDS compliance , HIPAA, or ISO 27001
- An included Intrusion Detection System (IDS) or Intrusion Prevention System (IPS)
- If it is a Network Firewall look for:
Sucuri WAF
The Sucuri firewall is a cloud-based WAF that checks all the boxes. It integrates an intrusion prevention system (IPS), protects against DDOS attacks and functions as a reverse proxy. The Sucuri WAF uses virtual patching and hardening to address evolving security threats and is built on a CDN that enhances website speeds by an average of 60%. Talk to us about your requirements to find out if the Sucuri WAF meets your needs. Learn more.
Conclusion
Mixing and matching hardware and software firewalls is a good idea, but firewalls cannot protect you against everything – especially the human factor. Spoofing and phishing rely on human trust as a way to gain legitimate entry or trick you into clicking a malicious link. Dot your I’s and cross your T’s to stay ahead of malicious intent. Try our 30-day Free Trial and see how a Firewall can improve your website security.
The only way to stay completely protected from opportunistic attackers is to make sure you and your employees have a baseline education of cybersecurity. The National Institute of Standards and Technology (NIST) has compiled a list of free training classes, and Sucuri offers free email courses to buff up your cyber IQ.