As breach costs go up and attackers focus on common web features like dashboards, admin panels, customer portals, and APIs, weak access control quickly leads to lost data, broken trust, and costly incidents. The worst part is that many failures are not rare technical flaws but simple mistakes, such as missing permission checks, roles with too much power, or predictable IDs in URLs.
This post aims to help you control who can access different parts of your website and explain why it matters. By the end, you’ll have a clear plan to lower risk without making your site hard to use.
What is access control?
Access control is a set of rules and tools that decide who can use a system and what they can do once inside. In web security, access control usually combines authentication, which checks a user’s identity, with authorization, which gives permission to view data or take actions. It also includes the checks that make sure these permissions are followed across pages, APIs, and backend services.
Authentication vs. authorization
These two terms are separate steps in the security process. For strong protection, treat them as distinct parts.
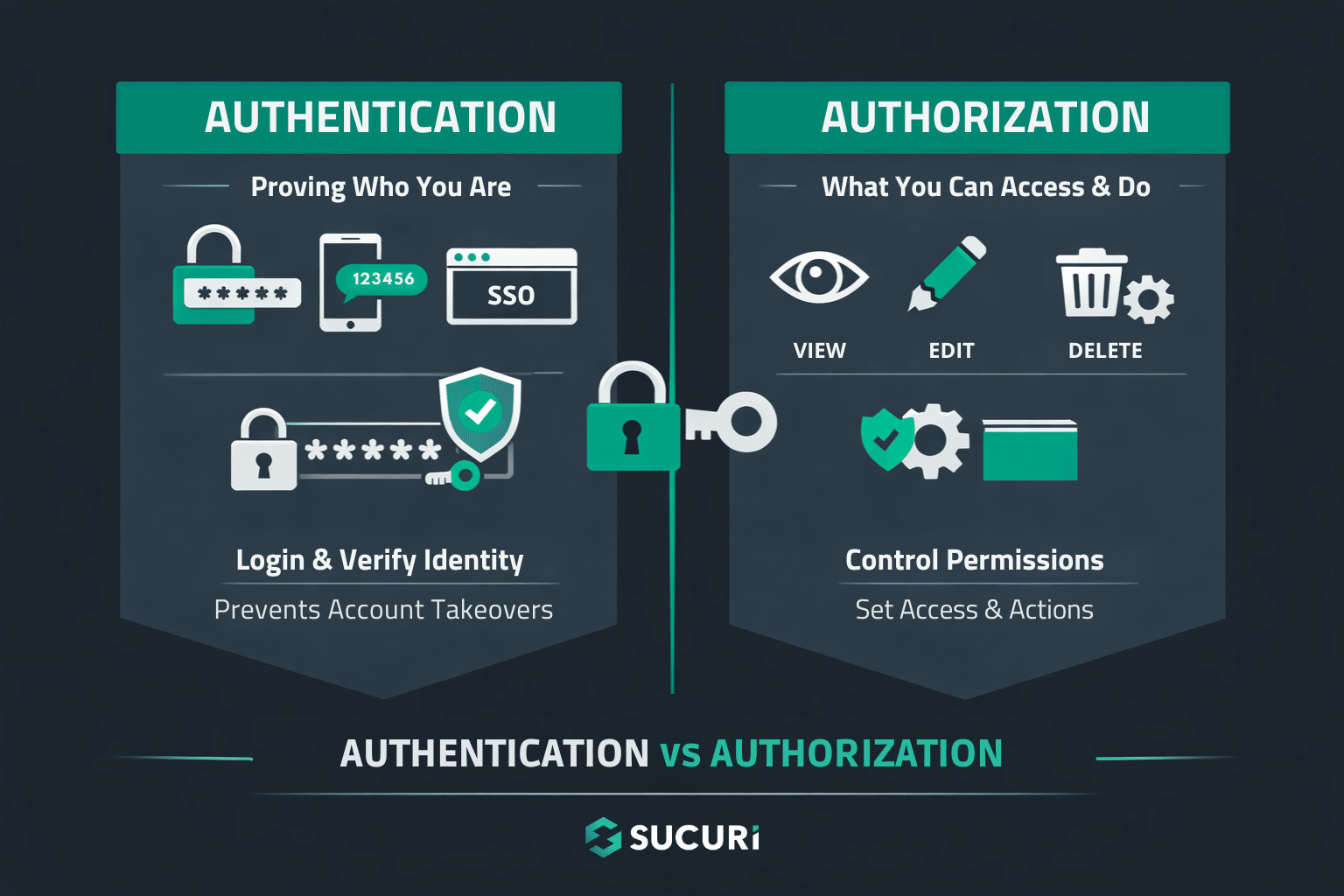
Authentication is about proving who you are. It’s the login step, using passwords, passkeys, one-time codes, SSO, or multi-factor authentication. Strong authentication helps prevent account takeovers, but it doesn’t automatically protect everything after you log in.
Authorization determines what you can do. Once you’re authenticated, authorization decides what you’re allowed to view, create, edit, delete, or manage. This covers permissions like “view invoices,” “edit product listings,” or “manage users.”
Think of authentication as showing an ID at the door, and authorization as the bouncer deciding if you can enter the VIP area, go behind the bar, or access the cash register. A secure website needs both, and they must be applied consistently. If even one endpoint skips the authorization check, attackers can often bypass your UI controls and reach sensitive data by calling URLs or APIs they shouldn’t access.
A common mistake is thinking that “logged in” means “trusted.” Many attacks come from real accounts, such as compromised users, staff with too many permissions, or customers testing what they can access. The safer approach is to require every request to prove it has permission, not just a valid session.
For modern identity systems, it’s also helpful to match authentication strength to the level of risk. For example, require MFA for admin actions, as recommended in digital identity guidance like NIST SP 800-63-4.
The 3 main models of access control explained
Most real-world web systems use one main model as a base and mix in ideas from others. Here’s an overview:
1. Discretionary Access Control (DAC)
DAC means the owner of a resource decides who can access it. If you’ve ever shared a document with certain people, you’ve used DAC. In web apps, DAC appears when users can set visibility (like “private,” “team,” or “public”) or share items with others. It’s flexible, but risky if sharing defaults are too open or if “ownership” can be faked, which can lead to IDOR-style issues.
2. Mandatory Access Control (MAC)
MAC enforces access rules based on centrally managed policies, and users cannot change them. This is common in high-security environments where resources are labeled by sensitivity and access is tightly controlled. On the web, you’ll see MAC-like behavior in systems that enforce strict boundaries, such as regulated data zones or tenant isolation. MAC can be very secure, but it is more complex to set up and maintain because it requires careful policy management.
3. Role-Based Access Control (RBAC)
RBAC assigns permissions to roles, such as Admin, Support, Editor, or Billing, and then assigns users to those roles. It’s the most common model for websites and SaaS products because it scales well: you add a user to a role, and they get the right capabilities. RBAC works best when roles match real job functions, are kept small and clear, and follow the principle of least privilege by giving only the access needed and nothing extra.
If you’re building a customer portal, a CMS workflow, or an API for multiple clients, RBAC is usually your starting point. You can then add context, such as attributes, where needed.
Why is access control critical for modern web security?
Access control is the difference between “a user is logged in” and “a user is allowed to do this specific thing with this specific data.” When it’s weak or inconsistent, attackers don’t need to break encryption or deploy malware, they simply take advantage of missing permission checks, predictable IDs, or overpowered roles. That’s why Broken Access Control continues to rank as a top web application risk.
On modern sites, the attack surface is bigger than the admin panel. Customer portals, SaaS dashboards, headless CMS endpoints, mobile apps, and public APIs all become targets, especially when business logic moves fast and authorization checks get duplicated (or forgotten) across services. Even well-meaning users can trigger damage if permissions are too broad: accidental deletes, unintended data exposure, or changes that quietly weaken security settings.
Strong access control also improves day-to-day resilience. It reduces blast radius when accounts are compromised, makes incident response cleaner (because permissions and actions are traceable), and helps teams operate with confidence as staff, contractors, and integrations change over time.
In short, access control protects more than data. By granting, managing, and revoking access as routine discipline, not a one-time setup, you protect boundaries, accountablility, and the trust users place in your site every time they click “Sign in.”
How to implement effective access control mechanisms
Good access control is not about using the latest buzzword, but about building a system that is consistent, testable, and hard to bypass. Your UI is not the security boundary; your server-side authorization checks are. Every request, whether it’s a page load, API call, or background job, should be checked against a clear policy: Is this user allowed to do this action on this resource in this context?
Start with a simple model you can explain to a new engineer in five minutes, and expand it as needed. Most teams do best with RBAC for basic permissions, plus extra rules for sensitive actions, such as requiring MFA for account changes or limiting exports to certain roles. Document your rules, centralize authorization logic so it’s not spread across controllers, and build automated tests to check both “allowed” and “denied” cases.
Below are two approaches that cover most modern web environments.
Role-Based Access Control (RBAC)
RBAC is popular because it fits how organizations operate. The key is to avoid too many roles and overly powerful default settings.
A practical RBAC setup might look like this:
- Admin: manage users, billing, security settings, integrations
- Editor: create and update content (but can’t change security settings)
- Viewer: read-only access to approved pages and reports
RBAC can fail if, for example, an “Editor” role quietly gets access to user management, or a “Viewer” can still reach hidden endpoints that export data. To prevent this:
- Design roles around job functions, not ego (“Power User”).
- Apply least privilege from day one: start small, grant access intentionally.
- Make sensitive actions (exports, permission changes, API key creation) require higher privilege—and ideally stronger authentication.
- Treat roles as a contract: when a role changes, log it, review it, and regression test it.
If you use WordPress or similar CMS platforms, roles are built in but still need oversight, especially if plugins add new features. Control who has admin access and review roles regularly.
Attribute-Based Access Control (ABAC)
ABAC makes authorization decisions using attributes, such as properties about the user, resource, and environment, instead of just roles. This is useful when a single role does not fit every situation.
For example, an “Agent” role might be allowed to view customer tickets, but only if:
- The ticket belongs to the agent’s assigned region
- The customer is in an active contract status
- The request occurs during business hours (or from a corporate network)
In ABAC, this means user attributes, resource attributes, and environmental attributes. You can also use ABAC to increase security, for example, by allowing someone to view a record but requiring MFA to download it, or by blocking access if the request comes from a risky location.
ABAC is powerful, but it can become confusing if not managed carefully. Keep policies easy to read, store them in one place, and use logging that explains why access was granted or denied. This audit trail is very valuable during incident response and compliance reviews.
Top 5 common access control vulnerabilities
Access control fails so often that OWASP lists Broken Access Control as a top risk. Here are five patterns that often appear in real incidents:
- Broken Access Control (BAC): This is the umbrella category: users can access data or functions they shouldn’t. It often happens when teams rely on front-end restrictions (“the button is hidden”) instead of enforcing checks on the server for every request.
- Insecure Direct Object References (IDOR): IDOR occurs when an app uses a predictable identifier (like invoiceId=1042) and fails to verify the user is authorized to access that specific object. Attackers simply change the ID and pull someone else’s data. For deeper prevention guidance, OWASP maintains an IDOR Prevention Cheat Sheet, and PortSwigger has practical examples in their Web Security Academy IDOR
- Privilege Escalation: A user starts with limited access and finds a way to get higher privileges, such as by exploiting a missing admin check, abusing a misconfigured token, or using an internal endpoint that assumes only admins can reach it. This often happens when “admin-only” routes exist but are not always protected.
- Missing Function-Level Authorization: Even if data access is protected, actions might not be. For example, a user can’t view the admin panel but can still call /api/users/delete because the endpoint assumes the UI is enough. Always enforce authorization at the function or action level, not just at the page level.
- Over-Permissive Defaults and Long-Lived Access: Default roles that are too powerful, shared admin accounts, API keys that never expire, and old accounts that stay active after role changes all increase your risk. Attackers look for places where one compromised account gives them too much access.
The key is consistency: if any route, API method, or background action skips the authorization check, the whole system becomes vulnerable.
Access control best practices
A good access control strategy is measurable. You should be able to answer quickly: Who has access to what, why do they have it, and when was it last reviewed?
Use this guidance during releases, plugin installs, staffing changes, and infrastructure updates. Strong access control is not a one-time project; it’s an ongoing habit. Teams that do this well set up guardrails like central policy checks, consistent logging, and automated tests, so security does not rely on someone remembering to add the right check at every endpoint.
Two areas deserve special emphasis:
- Audits and access reviews, because permissions drift over time.
- The human factor is important, since compromised credentials are still one of the easiest ways for attackers to get in.
Conducting regular security audits and access reviews
Access reviews turn “we think it’s secure” into “we can prove it’s secure.”
At a minimum, review access on a schedule that matches your risk. Monthly reviews are common for admin roles and sensitive systems, quarterly for broader roles, and immediately after major changes like new integrations, new customer data types, mergers, or big feature launches. Your audit should include:
- User and role inventory: Who exists, what roles they have, and whether they still need them.
- Permission mapping: What each role can do, including API scopes and plugin-added capabilities.
- Log review: Failed access attempts, unusual export activity, and repeated “access denied” patterns that might indicate probing.
- Negative testing: Automated tests that confirm unauthorized users cannot access restricted routes.
If you use WordPress, combine access reviews with regular security practices like strong passwords, MFA for administrators, and reducing the number of admin accounts.
The human firewall: user training and principle of least privilege
Even the best access control model won’t help if attackers can log in as a real user. That’s why your “human firewall” is important. Training, good habits, and guardrails reduce the chance of credential compromise and limit the damage if it happens.
Focus training on what actually breaks accounts:
- Spotting phishing and fake login pages
- Recognizing MFA push fatigue attacks
- Avoiding credential reuse
- Reporting suspicious access quickly
Then, support this with least privilege so a compromised account cannot cause much harm. In practice, this means:
- Keep admin access rare and time-bounded when possible
- Require MFA for privileged roles and sensitive actions
- Remove or disable unused accounts fast
- Avoid shared logins, as they remove accountability and make audits difficult.
Least privilege is about resilience. People change roles, contractors leave, and permissions can drift. Strong access control helps your system stay safe, even when people make mistakes.
Future-proofing your access control strategy
Access control connects users, access, and security. Authentication confirms identity, authorization sets permissions, and enforcement makes sure every request follows the rules. There should be no exceptions, no backdoors, and no relying on the UI to hide buttons.
To future-proof your approach, use clear roles and limit their power. Add context-aware controls where needed, such as ABAC-style checks for sensitive actions. Test authorization as carefully as you test business logic, and review access regularly so permissions do not drift into risky territory.
When you’re ready to add more layers of defense, such as monitoring, hardening, and faster detection and response, Sucuri’s tools can help you put that security posture into practice.











