Security Risk: Very High
Exploitation Level: Easy/Remote
DREAD Score: 9/10
Vulnerability: Privilege Escalation / Remote Code Execution
Patched Version: Pagelines: WP Repo 1.4.6, Pagelines Server 2.4.6 PlatformPro: 1.6.2
Users of both the Pagelines and Platform themes should update as soon as possible. During a routine audit for our WAF, we found two dangerous issues: A Privilege Escalation vulnerability affecting both themes and a Remote Code Execution issue for Platform.
What Are the Risks?
Any website using a vulnerable version of the Platform theme (<1.4.4) is at risk of a total site takeover.
An attacker can execute PHP code to infect your website with malware, SEO spam and other nefarious acts. For those using a vulnerable version of the Pagelines theme (<1.4.6), an attacker needs to be able to register an account on the victim’s website in order to successfully exploit the Privilege Escalation vulnerability. As for the first vulnerability, a successful exploitation could allow an attacker to do pretty much anything he wants with his victim’s website (by using, for example, WordPress theme file editor).
Technical Details
1 – Privilege escalation on Pagelines and Platform
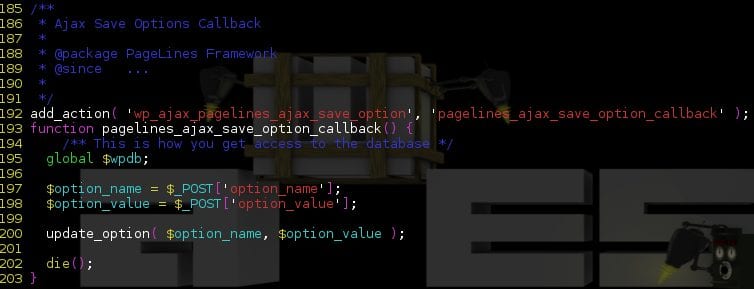
Both themes used a WordPress ajax hook to modify a few set of options.
Because all wp_ajax_ hooks are usable by any logged-in users (no matter what privileges they have on the target site), a subscribed user could use this hook to overwrite any options located on WordPress options database table. For instance, this would allow them to overwrite the ‘default_role’ option with a value like ‘administrator’, which would grant every new users on the site with an administrator account!
2 – Remote Code Execution on Platform
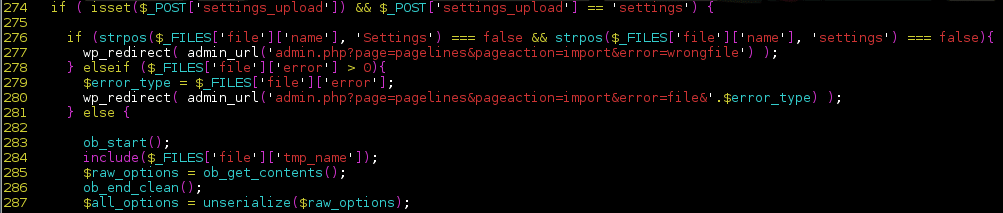
The theme used a somewhat unconventional way to import theme settings backups.
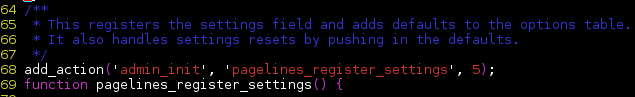
As you can see from the above snippet, the theme inserts the backup file into the theme’s execution context using a call to the include() PHP function. As this may not necessarily be a vulnerabiltity by itself (we don’t know yet if we can actually trigger this piece of code as an unauthenticated user), we decided to backtrace the issue, finding that the function using this code was called from another function called pagelines_register_settings().
This additional function was also hooked to the admin_init hook, which is known to be executed when a guest visitor visits either /wp-admin/admin-post.php or /wp-admin/admin-ajax.php, thus allowing anybody to used the aforementioned snippet of code to gain full privilege on the website.
Update as Soon as Possible!
Again, if you’re using a vulnerable version of any of these two themes, update as soon as possible! In the event where you could not do this, we strongly recommend you having a look at our Website Firewall to get it patched virtually.










20 comments
Do you mean version <2.4.6 of Pagelines? Pagelines had no version numbers of 1.X. Current version of Pagelines (as of the day this was written) is 2.4.5.
PageLines theme 1.4.6:
https://wordpress.org/themes/pagelines
He was referring to the versions on WordPress Themes Repo. The versions on PageLines will be updates too.
Thank you, Simon — appreciate you weighing in here!
Just to make things clear, people using the free versions of these themes will already have an update pending in WordPress admin area, the theme review team were good enough to fast-track the two fixed versions.
Users of the pro versions available from pagelines.com will also see an update pending and can either update via wordpress updates or download the latest version from their account area.
Marc didnt mention in the post above but this simple plugin patches the exploits, if you cant update the themes for any reason, works will all versions of the themes mentioned.
https://gist.github.com/Pross/769de6e9219705041c67
To clarify, this is ONLY in legacy version of these two PageLines products (Framework and Platform). Since this was first reported to us 3 days ago we’ve immediately patched those files and updated them on WordPress.org, GitHub and anywhere on PageLines servers.
*Note: This does not apply to more recent software, such as DMS.
** Note 2: To our knowledge, this issue has never been exploited and was discovered via a Securi script. It is a risk only if you allow open registration for the backend of your PageLines site.
If you have any questions, please email us at hello@pagelines.com
Do you have a directory name for each of these themes? (i.e. themes/XXX/). Also easy way to identify the version from command line (for servers with many WP blogs on them)? This will help us pinpoint who’s vulnerable quickly across diverse network. Thanks.
Folders could be platform platformpro and pagelines. Assuming the user is using the correct folder names.
This plugin will stop the exploit for all versions: https://gist.github.com/Pross/769de6e9219705041c67
Plugin is great idea, Simon — quick fix to buy us time to update!
ups here we go, guess thats the patch. where do I includr this Simon? I run 2 old platform pro installs 😀
Its a wordpress plugin
Hey Simon: Any instructions on installing the plugin? PS Thanks for this.
You can either copy/paste the file into your plugin dir, or if you want to use the wp plugin uploader then you can get the zip from pagelines.com: http://www.pagelines.com/themes-requiring-updates/
Thanks man! All set!
Does anyone know how to patch the issues? I have 2 older pageline sites.. and i dont feel like upgrading them.
Thanks guys, you are life savers!
Can someone answer my question, I have created a child theme of Pagelines theme and using that as my current theme. There is no update available for the theme I am using. What to do?
Either download the parent theme and upload the files via FTP, or install the plugin, easy.
How exactly a visitor can access wp-admin/admin-post,php without authentication, which means it requires authentication, hence its not as serious as it seems, a person who gain authentication can upload their shell directly.
if( ! current_user_can( ‘edit_theme_options’ ) )
die( ‘Cheatin huh?’ );
Comments are closed.