Exploitation Level: Very Easy / Remote
DREAD Score: 7.4
Vulnerability: Persistent Cross-site Scripting via option update
Patched Version: 8.0.27
During a routine research audits for our Sucuri Firewall, we discovered an Unauthenticated Persistent Cross-Site Scripting (XSS) affecting 60,000+ users of the WP Live Chat Support WordPress plugin.
Current State of the Vulnerability
Though this security bug has been fixed in the 8.0.27 release, it can be exploited by an attacker without any account in the vulnerable site.
We are not aware of any exploit attempts currently using this vulnerability.
Disclosure / Response Timeline:
- April 30, 2019: Initial contact attempt.
- May 15, 2019: Patch is live.
Technical Details
This vulnerability can be exploited due to a well-known attack vector in the WordPress plugin world, an unprotected admin_init hook:
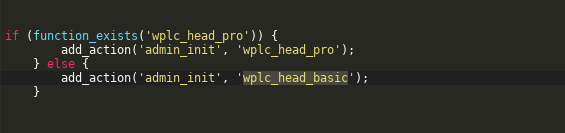
In this particular vulnerability, the function wplc_head_basic updates the plugin settings without using proper privilege checks:
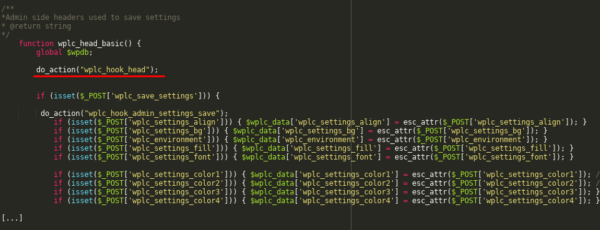
It then executes an action hook with even more critical settings:
Since “admin_init” hooks can be called visiting either /wp-admin/admin-post.php or /wp-admin/admin-ajax.php, an unauthenticated attacker could use these endpoints to arbitrarily update the option “wplc_custom_js”.
The content of this option is added as a complement anywhere the live chat support appears, allowing bad actors to inject malicious JavaScript payloads in multiple locations of a vulnerable website.
Update as Soon as Possible
Unauthenticated attacks are very serious because they can be automated, making it easy for hackers to mount successful, widespread attacks against vulnerable websites. The number of active installs, the ease of exploitation, and the effects of a successful attack are what makes this vulnerability particularly dangerous.
To protect against this vulnerability, we strongly encourage WP Live Chat Support users to update their plugin to version 8.0.27 as soon as possible. Users that are unable to update immediately can leverage the Sucuri Firewall or equivalent technology to virtually patch the vulnerability.










