Keeping websites and applications secure starts with knowing which vulnerabilities exist, how severe they are, and whether they affect your stack. That’s exactly where the CVE program shines. Below, we’ll cover some CVE fundamentals, including what they are, how to search and understand the data, and how to translate this information into actionable steps.
Introduction to the CVE database
So, what is CVE?
CVE stands for Common Vulnerabilities and Exposures, a community-driven program that assigns unique identifiers to publicly known vulnerabilities. Each identifier (or “CVE ID”) is a consistent, vendor‑neutral label that makes it easier for the entire ecosystem of vendors, researchers, and tools to talk about the same issue without confusion.
Learn more: the official CVE Program and its Program Organization.
CVE IDs themselves don’t include all the scoring or product details. For enriched data (scoring, affected products, etc.), most practitioners also consult the U.S. NIST’s National Vulnerability Database (NVD).
Importance of the CVE database in cybersecurity
Why CVE matters:
- Shared language: The same CVE ID appears across vendor advisories, scanners, and patch notes.
- Faster triage: Teams can quickly filter vulnerabilities by severity, product, or exploitability.
- Compliance-ready: Many frameworks (e.g., PCI DSS, ISO 27001) expect a repeatable vulnerability management process. CVE is the foundation.
- Better coordination: From CMS plugins and themes to libraries and OS packages, CVE IDs connect the dots across your software supply chain.
How to access and search the CVE database
Navigating the CVE website
Start with two primary destinations:
- CVE.org Search: Browse canonical CVE records, their status, and references.
- NVD: Dive deeper into enrichment like CVSS scores, CPE product identifiers, configurations, and impact metrics.
For WordPress site owners, add one ecosystem-focused resource:
- Patchstack Vulnerability Database: WordPress-focused advisories covering plugins, themes, and core, plus research and roundups.
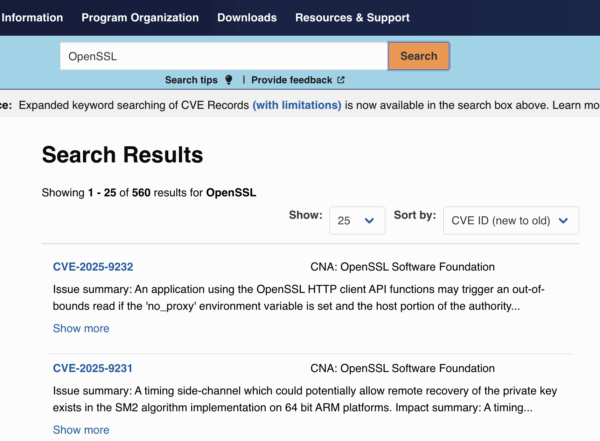
On CVE.org, use the top search bar for a product name (like “OpenSSL”) or a CVE ID. Each CVE page links out to references such as vendor advisories and sometimes to NVD.
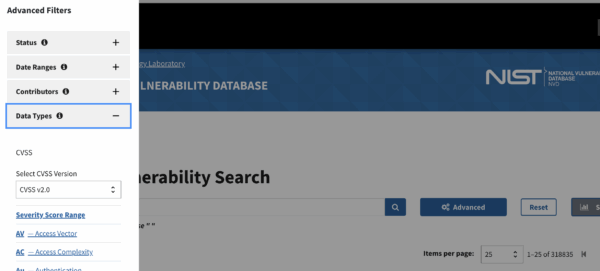
On NVD, the Vulnerabilities section provides an advanced search with filters for keywords, vendors, products, versions, CVSS ranges, and dates. You’ll also find product taxonomy under the CPE Directory.
Search techniques for finding CVEs
Here are some methods for tracking down CVEs:
- By product & vendor: Search “vendor product” (like “WordPress WooCommerce”) to find relevant results across versions.
- By CVE ID: If you already have an identifier from a vendor bulletin or scanner, paste it directly.
- Filter by severity: Use NVD’s CVSS filter to prioritize critical/high items.
- Filter by date: Limit results to the last 7/30/90 days to focus on fresh issues.
- Use CPE for precision: If your scanner or inventory uses CPE, search that exact string to narrow to specific products/versions.
- Check known exploited: Compare findings with CISA’s Known Exploited Vulnerabilities (KEV) Catalog to spot vulnerabilities actively exploited in the wild.
- Prioritize likely exploitation: Consider FIRST’s EPSS (Exploit Prediction Scoring System) to weigh how likely a vulnerability is to be exploited soon.
Understanding CVE identifiers
Structure and format of CVE identifiers
A CVE ID follows this pattern:
CVE-YYYY-NNNNN- YYYY is the year the ID was reserved or assigned (not necessarily the discovery or patch year).
- NNNNN is a unique number. Since 2014, the number of digits is variable to accommodate growth (e.g., CVE-2019-1234, CVE-2024-1234567 are both valid).
How CVE identifiers are assigned
CVE IDs are assigned by CVE Numbering Authorities (CNAs) – vendors, research orgs, coordinators, and other partners authorized under the CVE Program. A CNA can reserve an ID early (you’ll see the status RESERVED) and later publish details. Sometimes entries are REJECTED if they don’t meet criteria, or DISPUTED when there’s disagreement about validity or impact. You can learn more about CNAs here.
Analyzing CVE entries
Components of a CVE entry
On CVE.org you’ll typically find:
- CVE ID & state (PUBLISHED, RESERVED, REJECTED).
- Description of the vulnerability.
- References (links to vendor advisories, issue trackers, or research posts).
On NVD, entries often include additional fields for triage:
- CVSS metrics (usually v3.1 base score and vector; some ecosystems are piloting v4.0).
- CWE (Common Weakness Enumeration) to classify the underlying weakness.
- CPE configurations (which vendors/products/versions are affected).
- Last modified date (important for re-reviews and scoring updates).
Reading a CVSS vector:
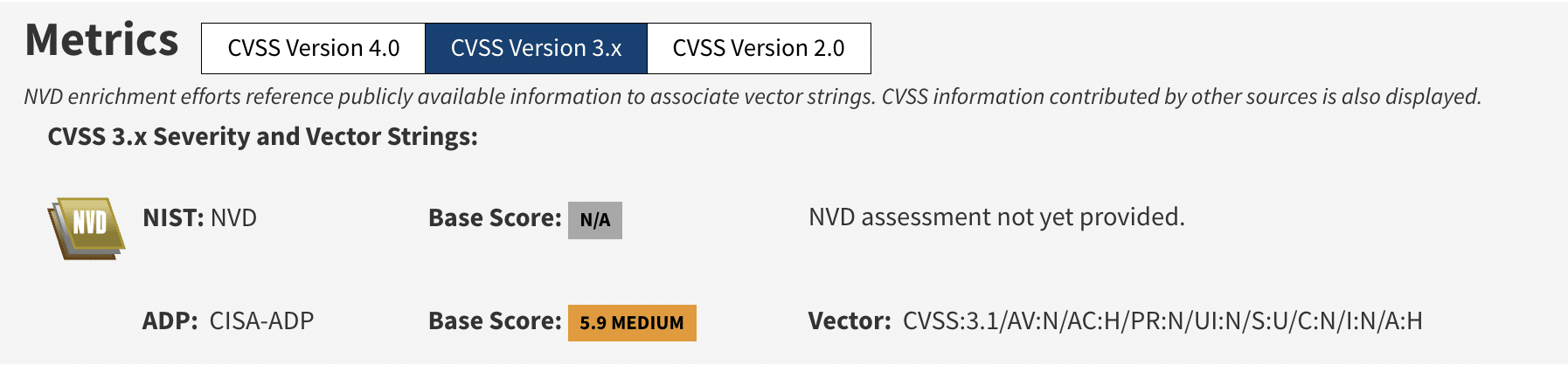
A vector like AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H (often a 9.8–10.0) encodes the attack conditions:
Attack Vector, Attack Complexity, Privileges Required, User Interaction, Scope, and impact on Confidentiality/Integrity/Availability.
Learn more at the CVSS spec: first.org/cvss.
Risk assessment based on CVE information
Use CVE data as inputs rather than the final word. Consider:
- Exploitability & activity
- Is it on CISA KEV? Prioritize immediately if yes.
- Is public exploit code likely or confirmed? EPSS can inform likelihood.
- Exposure & applicability
- Does the vulnerability affect software you actually run (check versions/CPE)?
- Is the vulnerable service internet-exposed?
- Can a WAF or configuration change mitigate while you patch?
- Impact severity
- CVSS base score and vector indicate how damaging exploitation would be.
- Vendor advisories sometimes provide context that differs from NVD scoring, so read both.
- Patch & workaround availability
- Is a fixed version available? Are there temporary mitigations?
- Will mitigating controls (e.g., WAF rules, feature flags) meaningfully reduce risk?
- Business context
- Consider data sensitivity, regulatory obligations, and uptime requirements.
- Prioritize vulnerabilities on critical customer-facing assets.
Best practices for using the CVE database
Regular monitoring of CVE updates
- Subscribe to feeds:
- CVE.org and NVD both offer RSS/JSON feeds (see NVD’s Developers).
- Track CISA KEV updates for exploited-in-the-wild issues.
- Watch your stack:
- Maintain a living inventory (CMS, plugins/themes, web server, PHP, database, OS packages, third‑party libraries).
- Map products to CPEs where possible to automate matching.
- Set review cadence:
- Daily/weekly triage for internet-facing systems.
- Emergency process for critical RCEs or KEV entries.
- WordPress-focused signal:
- Follow Patchstack’s database and weekly roundups for plugin/theme advisories and remediation guidance.
Integrating CVE data into security policies
Turn CVE insights into consistent actions:
- Severity SLAs: For example, patch CVSS ≥ 9.0 within 24–72 hours; KEV items “asap”; 7.0–8.9 within one or two patch cycles.
- Exploitability signal: Escalate based on EPSS probability or confirmed exploitation.
- Change management: Use staging, backups, and rollback plans (especially for CMS/plugin updates).
- Documented exceptions: If you must defer a patch, record risk acceptance with compensating controls (e.g., WAF rules, access restrictions).
- SBOMs & SCA: Use a Software Bill of Materials and software composition analysis to catch library-level CVEs across builds.
- Training & playbooks: Ensure operations knows how to read CVE/NVD records, validate applicability, and implement mitigations quickly.
- OWASP alignment: See OWASP resources on vulnerability management and patching process: OWASP Top 10 and the Vulnerability Management project.
Conclusion and further resources
CVE is the industry’s common dictionary for vulnerabilities. Pair CVE.org for canonical records with NVD for scoring and product mappings, and add CISA KEV and EPSS to judge urgency. If you manage WordPress sites, integrate Patchstack to stay up to date on plugin and theme advisories. Build automation around your asset inventory, feeds, and SLAs so you can detect, triage, and mitigate faster.
Useful links to keep handy:
- CVE Program
- National Vulnerability Database
- CPE Product Dictionary
- CVSS Specification
- EPSS (Exploit Prediction Scoring System)
- CISA Known Exploited Vulnerabilities
- CWE
How Sucuri can help
If you manage a website or CMS, you don’t have to navigate CVEs alone:
- Website Firewall (WAF) with virtual patching to mitigate many vulnerability classes while you update.
- Continuous monitoring & alerting for file integrity changes, blacklisting, and anomalies.
- Free SiteCheck scanner to identify outdated CMS components and common indicators of compromise.
- Incident response & malware removal to help contain and recover quickly if an issue is exploited.
Security is a journey. Use CVE data to know what matters, and pair it with layered defenses and disciplined patching to keep your sites resilient.