Apache has a very useful functionality called server-status that allows administrators to easily find how well their servers are performing.
It is basically an HTML page that displays the number of process working, status of each request, IP addresses that are visiting the site, pages that are being queried and things like that. All good.
However, this feature can also have security implications if you leave it wide open to the world. Anyone would be able to see who is visiting the site, the URLs, and some times even find hidden (obscure) admin panels or files that should not be visible to the outside.
Talk about an awkward moment.
URL mapping and server status
We started a small crawling project in our Labs that queried over 10m different web sites (some of the crawl data is at URLfind.org). And we noticed something very interesting: Lots of web sites (some big ones) keep their server-status page open the whole world.
Here are just a few popular brands showing their status:
http://php.net/server-status/
http://metacafe.com/server-status/
http://cloudflare.com/server-status/ (FIXED)
http://disney.go.com/server-status/ (FIXED)
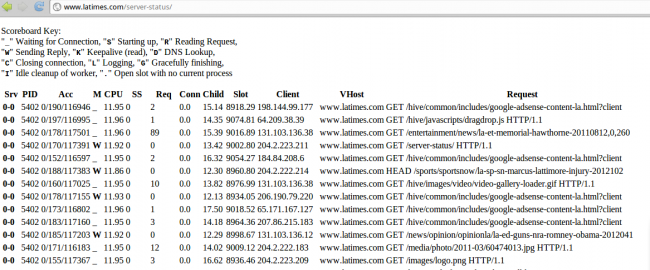
http://www.latimes.com/server-status/
http://www.staples.com/server-status/
http://tweetdeck.com/server-status/ (FIXED)
http://www.nba.com/server-status/
http://www.ford.com/server-status/
http://www.cisco.com/server-status/
http://www.chicagotribune.com/server-status/
http://www.yellow.com/server-status/
http://apache.org/server-status/
And many many more here: http://urlfind.org/?server-status.
Is that a big deal that I can go to staples.com/server-status/ and see all those orders/connections being made and their IPs? Or go to one of them and search for “admin-p” and find a mostly unprotected admin panel (I won’t disclose the site). Or find all the internal URLs and vhost mapping for nba.com or ford.com?
Probably not a big deal by itself (well, if you don’t have an unprotected admin panel), but that can help attackers easily find more information about these environments and use them for more complex attacks.
Simple fix
For server admins, please disable server-status or restrict it to only a set of IP addresses that really need to use it. This link explains how to do so: http://httpd.apache.org/docs/2.2/mod/mod_status.html.










44 comments
Daniel, you can remove cloudflare.com from that list. We (re)closed that hole after seeing your post. Good nudge. ;-p
John
CloudFlare
Removed now. thanks!
It’s still in the blog post above.
Hi Sasha
Yes, we’ve removed the link and assigned it as fixed. Are you seeing the fixed? Could be cached.
Thanks
Looks like CloudFlare fixed theirs. It redirects to their homepage now.
this is really very useful tip..going to close for my site as well… great project from securi lab
No worries, glad it helps.
The folks with the unprotected admin console probably think they are safe because it’s in robots.txt as globally disallowed. 😉
😉
Looks like nba.com is fixed as well, now returns a 403…
Still shows up here. There’s is one of the worst ones, you can see modules installed etc..
Yep still there, I had left out the trailing slash…
Heh worse than that you can see that they get almost no traffic 🙂 3 connections and 1021 idle workers, ouch!
fwiw, getting 404s for http://www.nba.com/server-status/ now…
Do you know if Nikto detects this?
Have no idea.. haven’t tried running nikto on them to see.
http://apache.org/server-status/
Oh Brad, that’s classic. Thanks, added to the post.
looks like mod_security takes care of it. My servers return 403s.
I mentioned this in the hacker news thread on the subject, but beware when running Squid (or similar) in reverse proxy mode (which is pretty common, and may be what happened to at least some of the sites here).
Many default apache configurations already limit requests to localhost, but if you run a reverse proxy then unless you take additional measures you can risk exposing this sort of restricted info, since apache will see all requests appear to originate from the proxy, which typically is running on localhost.
1. hiding server-status will make no difference *if* your system is secure to begin with
2. the real fix is [Deny from all] for everything, [Allow from all] for specific resources, and [Allow from localhost] for admin stuff, accessed by ssh if required at all – And it fixes much much more than just server-status.
nba.com is fixed.
PHP.net is fixed as well
Reveals pushdo infectees 🙂 1-048496840/18/18_10.5812300.00.460.46 118.101.101.30 defaultPOST /?ptrxcz_llmmmmmmmooooooopppppppqqqqqqq HTTP/1.1
for instance.. (118.101.101.30 is infected) – a public service, in a way.
In the case of apache.org we do have a public server-status page intentionally.
Heres a google dork that will find the page in question intext:”Apache Server Status for”
To be fair to these server admins, this might not be their fault. I tracked down the problem on two sites I control to a LimitExcept directive. Is this actually an Apache problem? At the very least, the documentation does not warn about this.
(I blogged about it in more detail at http://lightyearsoftware.com/2012/11/popular-sites-with-apache-mod_status-enable/.)
So google’s “Cached Page” option still lists everything from ‘fixed’ sites. dunno if notifying them would help or not…
no its still working
Ummm…duh that’s called demonstrating your features for apache…they have nothing to hide and as an open source project its in the spirit of openness 🙂
Comments are closed.