In 2016, I shared some thoughts about firewalls in general; their history and purpose in the information security domain. The point of the article was to help website owners differentiate between the types of firewalls they might encounter. Today, I will shift my focus specifically to website application firewalls (WAF).
WAFs are not new, but have been traditionally deployed by large organizations. The SMB space has found renewed focus on WAFs over the past three years. This can be traced back to 2014-2015, a period when website security issues were front and center with most media outlets. There were critical software vulnerabilities in core platforms like Drupal, and in extensible components, like the RevSlider plugin for WordPress. These issues led to mass compromises. In 2014, security issues were compounded by the growth of brute force attacks.
These two issues have become the leading causes of today’s website hacks – abusing access control and exploiting software vulnerabilities, which brought about a very important question –
What are website owners supposed to do to stay ahead of evolving threats?
The most logical answer is to leverage a solution that would take responsibility from the website owner and place it in the hands of professional security providers. This is where WAF solutions come into play.
Deployment and Configuration of WAFs
At their core, all WAF solutions function in a similar way. They act as an intermediary service between your website application and the visitor browsing your site, intercepting and stripping malicious requests before they can cause damage. The real difference comes in how they are deployed within the web architecture. WAF technologies are not meant to replace existing controls, but complement them.
The following illustration provides a basic representation of how the different firewall types work together.
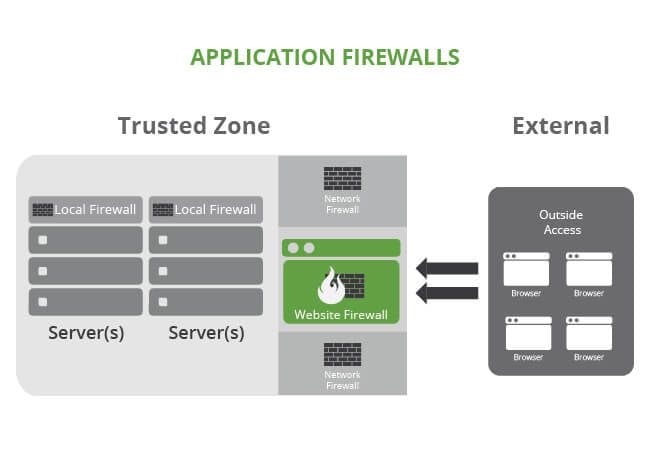
There are three deployment options for WAFs:
- In-line Appliance Firewalls – Deployed in your organization’s network, traditionally within the DMZ. Has installation and configuration requirements and is platform agnostic.
- End-point Firewalls – Deployed within the hosting server. Can be deployed at different levels: the operating system (i.e. IDS/IPS), the web server (i.e. Apache), and the application (i.e. WordPress, Drupal). Has installation and configuration requirements and is platform specific.
- Cloud-based Firewalls – Deployed in the cloud, outside your hosting environment. Has no installation requirements, is configured via DNS or BGP, and is platform agnostic.
This post focuses predominantly on end-point and cloud-based firewall deployment options, assuming that if you’re deploying in-line appliances the web architecture is fundamentally different than most website owners.
End-Point vs Cloud-Based WAF Architecture
The most common question we get about website firewalls is: Which firewall deployment should we use?
The answer depends on your organization; its capabilities, and the level of investment it wishes to make in security. If done correctly, an organization can deploy both end-point and cloud-based solutions, but the real answer is – deploy the security solution that fits your organization best.
Choosing the Best WAF Solution
If you like to tinker and be actively involved with the configuration, tuning, and maintenance of the WAF, then an end-point solution is likely the best option for you. Cloud-based WAFs are the opposite – they are easy to deploy and require little oversight or interaction with the website owner.
The illustration below helps visualize the difference between end-point and cloud-based WAFs, and outlines the various end-point options.
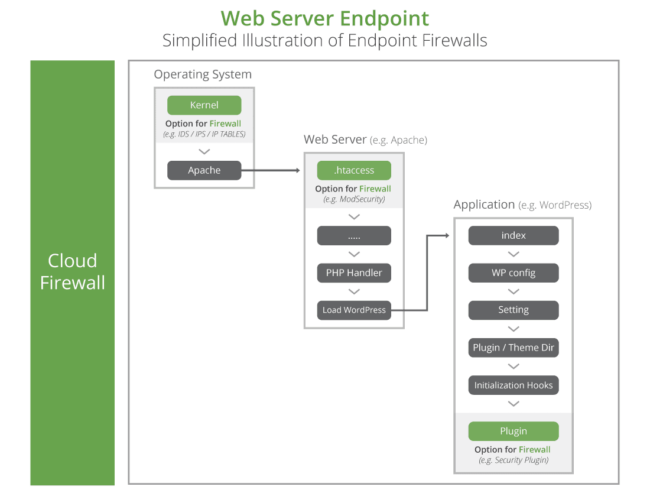
Available options will be dictated by the host (i.e. shared, virtual private server, or dedicated server). If an organization leverages a shared hosting account there will be limits to the types of end-point solutions available. In many instances, the host itself will offer solutions already at the operating system and web server, leaving the website owner responsible for the application. If you’re leveraging a dedicated or virtual server however, this will be different, as you will be responsible for security across the entire endpoint. Hosts will limit which application endpoint WAF’s you can use because of their negative effects on web server resources, often referring customers to cloud-based solutions.
Effectively Improve Website Security Posture
Regardless of platform, security needs to be something considered early and often. The number one consideration should be: How will your organization be able to keep up with the security threats?
A perfect example of the value of a WAF can be seen in the recent, critical content injection vulnerability in WordPress. Through cloud-based technology, all Sucuri customers were patched before updates were made available – and before organizations had to think through their respective upgrade and change control processes.
The realization that most make, sometimes begrudgingly, is that it’s extremely difficult and they find themselves asking for a solution that can help.
Additionally, when we consider the scale we’re working with – 1 billion + websites currently on the internet – and that 99.99% of the attacks are targets of opportunity and automated. We realize that technologies like a WAF make a lot of sense for a very large percentage of websites.
We are partial to cloud-based solutions, but honestly a WAF deployment (regardless of what deployment type you choose) will be the best investment you can make as it pertains to security. It’s positive affects are such that it is the most practical security control every website owner should consider.