You have heard me write in the past about understanding the true Vulnerability within WordPress. In that post I talk to the benefits of the platform and how those same benefits are also its weakness. This post is an example that brings that point home, specifically about staying diligent with your plugins.
It was recently released that a plugin for WordPress, Deans FCKEditor with PWWANGS Code Plugin for WordPress, was known to contain a very serious vulnerability that gives hackers full control to modify, upload and execute files within your WordPress install (source PacketStorm). This vulnerability is actually not new and was found for version 1.0.0. That’s not the point though, what is, is that this version is in fact vulnerable.
Understanding the Exploit
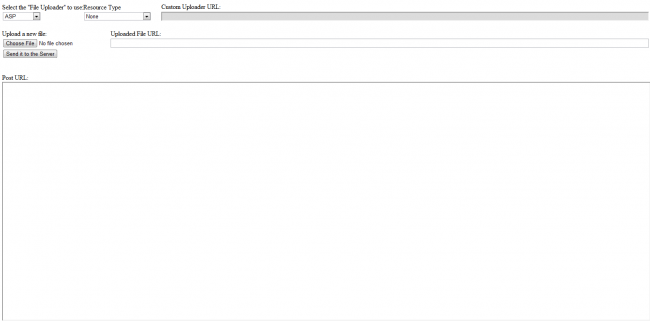
What it comes down to is that a user, working over HTTP, is able to gain access to your server by accessing a backdoor in the plugin’s directory. What makes it worse is how easy they make it look. Using a webshell they have created a nice little graphic user interface (GUI) in which they have the ability to give you all kinds of headaches.
e.g., http://somesite.com/wp-content/plugins/deans-fckeditor-with-pwwangs-code-plugin-for-wordpress/filemanager/connectors/test.html
Sample image of what the end-user sees when accessing the file over HTTP:
You can see that via this GUI the end-user is able to select their connector type, define a directory to work within, create folders, get folders and files and upload anything they want.
Unfortunately, if you’re running this plugin the probability that you received notification of this vulnerability is highly unlikely. But if you check the WordPress.org repository you’ll notice its no longer available. Its often good practice to let that be a warning, if running a free plugin and it gets removed from the repository be weary.
Take Away
Obviously if you’re running this plugin its in your interest to remove it and scan your site and server to ensure nothing has been injected.
Hopefully it also helps you understand the weakness associated with the extensibility of the WordPress platform and the due diligence required of all end-users.






2 comments
Comments are closed.