*****Updated – 20121019*****
Both Matt Mullenweg and Barry Abrahamson, System Wrangler with Automattic, have confirmed that there was not an environmental compromise and everything was isolated to individual user accounts.
Per their incident handling process they identified a brute force like attack which made use of a list of compromised email / password combinations derived from a third-party application[s].
People often use the same username and password on different sites, even though we all know we shouldn’t. If a password on a smaller site is compromised bad guys try it against the big ones like Twitter, Facebook, and WordPress.com. If anything bad happens to a WP.com user we get in touch with them as soon as possible to assist them. – Automatic.com
At this point it’s unclear of the severity, as WordPress.com has not released anything public, but I would say the odds are not in their favor.
The Hacker News (THN) put out an article this morning titled: 15000 WordPress Blogs Hacked For making Money From Survey.
Naturally my first reaction was, meh, it’s likely a fluke of some kind, but as I read it I became more suspicious. It all started with this email:
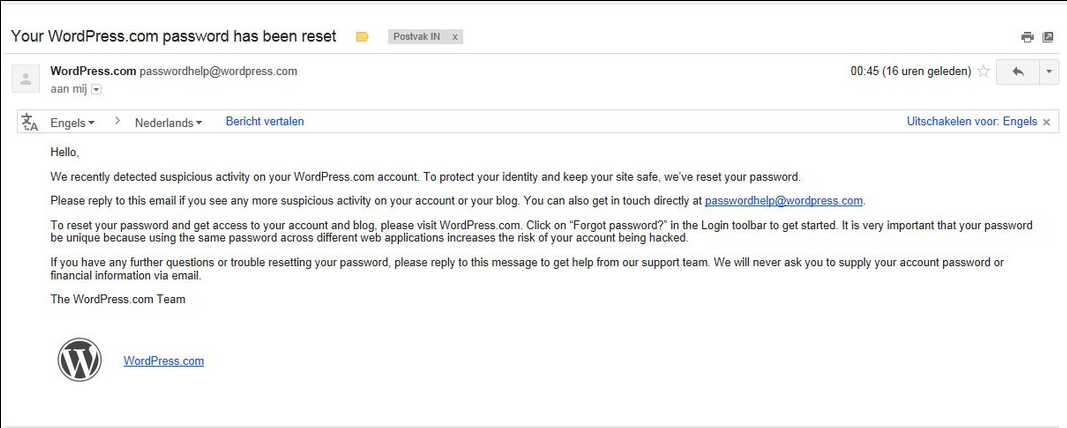
Because of the Phishing attempt on .ORG users about 6 months ago, I couldn’t help but think the same here, until you run this on Google Search:
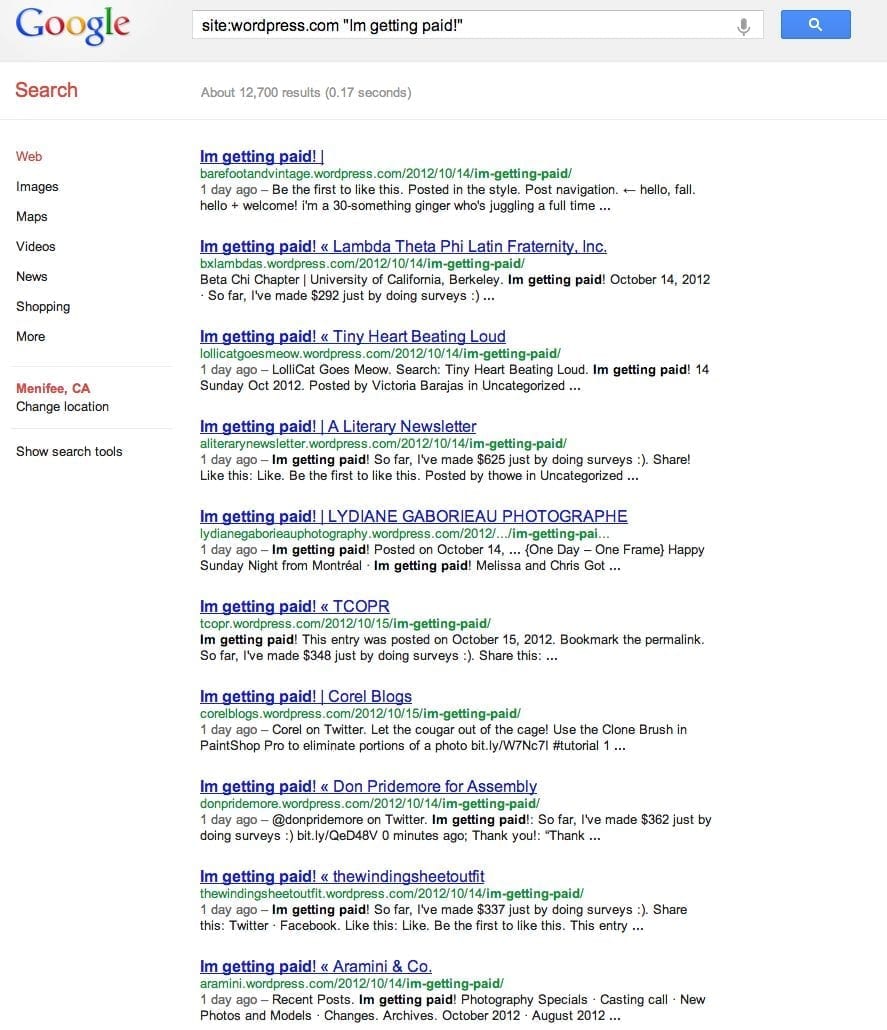
site:wordpress.com "Im getting paid!"
Go ahead and open Google Search and run that search, you’re likely to get something like this:
If you compare to what THN provided, it’s a few thousand less than originally reported, but still an impressive result. Why impressive? Well, for 12,000 – 15,000 blogs to all of a sudden share a similar post in a shared environment is highly unlikely. It quickly fails the sniff test.
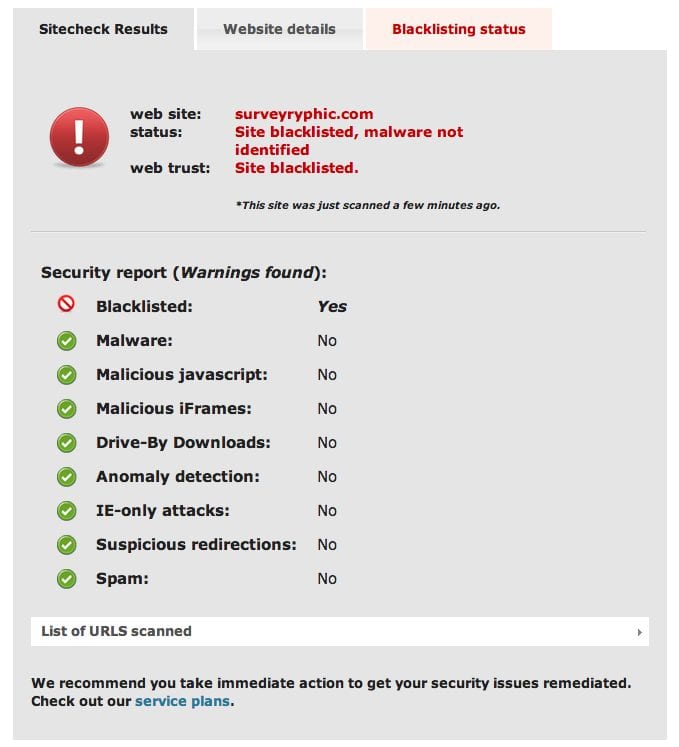
If you click on most of the links they’re all quickly being shut down, but there are still a few live ones. They all seem to have been posted on the 14th/15th of this month, and most seem to refer back to the following site that we have long since blacklisted:
Something Doesn’t Smell Right
Obviously we don’t work at Automattic, the company behind WordPress.com, but we sure do look forward to learning more of this incident.
For those on WordPress.com, I would offer the advise of going in and updating your credentials, but here is the fact of the matter – The odds that your account was compromised via one of your user accounts is highly unlikely.
Own one, own them all!
If I were doing the attack, I would find a way into the environment and figure out a way to touch every server. The feature is obviously already there, it’s how they’re all managed; if I’m not mistaken, it’s just one big Multisite configuration. You find the mechanism that touches each site, compromise that, embed a shell that allows you to own it, and cover your tracks. Whatever that replication and communication process is, I assure you it exists and yes we’ve seen it before.
That being said, the email is then a bit misleading and this is why:
It implies that the users credentials were compromised.
OK, that’s fair, but the question is how? It’s highly unlikely it was a brute-force against the login page. Just not realistic if I know the .COM configuration. Surely they have mechanisms in place to avoid BruteForce on the login page, right?
Assuming they do, then that means if the credentials were compromised, it happenened in an internal component, and likely from a database dump of some kind. Running a few tools like CAIN or JohnTheRipper could easily crack the default DB storage hash implemented for passwords. Then again, that’s if it were credentials, right?
There are a lot of identical posts across various websites coming up in Google, is it safe to assume a common user was used with enough privileges to post across all sites? Interesting, don’t you think?
If any of you hosts with WordPress.com, and can share more details, that’d be pretty awesome.








6 comments
Barry from Automattic here. Wanted to confirm that there was no
WordPress.com server or administrative compromise involved in this
situation. From our data, we know that these were individual user-level
compromises, most likely the unfortunate result of people sharing the
same password across multiple services. We noticed the problem pretty
early on and have worked to notify all of the affected users, reset
their passwords, and clean up the spam from their sites. In the future,
feel free to contact us at security AT automattic.com with any security-related questions. We’re always happy to clear up any details to ensure
that you have the most accurate information possible.
Comments are closed.