This has been an interesting couple of weeks in the Anti-Virus world, specifically in the malware business for notebooks and desktops running the MAC OS.
Securelist put out a very interesting post yesterday talking to the anatomy of the Flashfake / Flashback outbreak. While we can’t objectively quantify their claims, we wanted to take a look to see if we saw anything that might present itself as a possible correlation.
Low and behold, I think it is safe to say that “yes” a correlation does appear to exist.
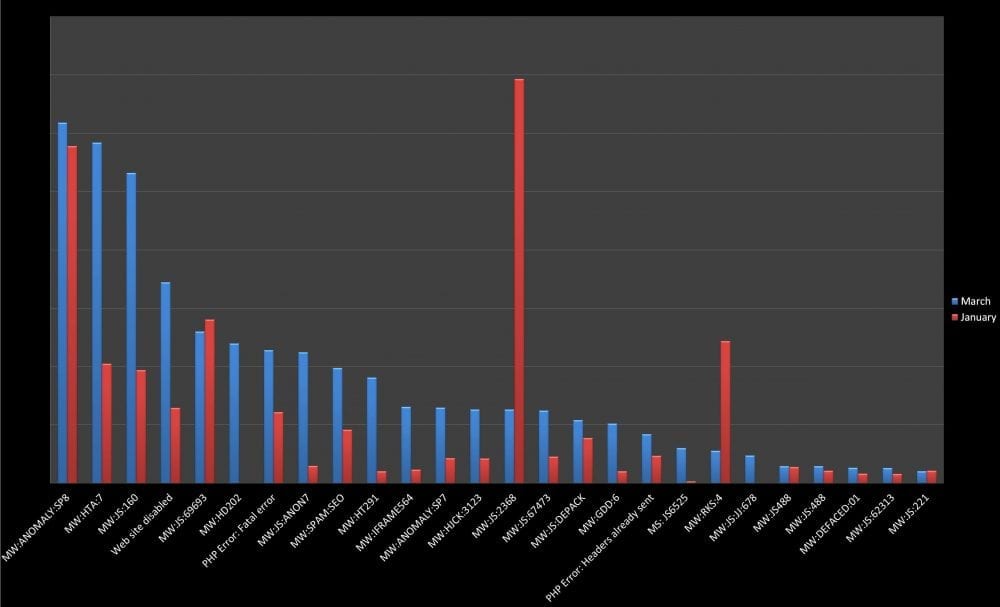
Shifting Trends
At second glance we start seeing some very interesting trends between January – March of 2012:
- Noticeable increase in the number of redirects is evident at first glance (2nd from the left).
The statistics alone are very interesting, but we wanted more. We then turned our attention at some of the trends in the form of posts that we were putting out.
Everyday we discuss what we should and shouldn’t write about and it so happens, that unbeknownst to us, we were painting a very interesting picture that shows an additional layer of correlation between the events.
Timeline:
February 14, 2012 – New WordPress ToolsPack
February 27, 2012 – Malware Campaign from .rr.nu
March 8, 2012 – Latest Mass Compromise of WordPress sites
March 15, 2012 – New Malware – Eval + GetMama + Encoded JavaScript
April 10, 2012 – GetMama – Conditional Malware Affecting Thousands of Sites
In Making Sense Of It
We felt compelled to share this information because of the obvious association between the events. February and March brought about huge spikes across the board. We saw close to 300% change in the number of clients, and the number of those suffering from redirect, social engineering, IP cloaking and drive-by-download infections.
While an obvious sign that things were in the works, until now, connecting the dots and understanding the bigger picture remained elusive.







4 comments
Nice post…i like ^^
Thanks, pass it on..:)
Interesting post, i learned more important things from it.
Comments are closed.