Education is crucial in defending your website against emerging threats. That’s why we are thrilled to share our 2022 Website Threat Research Report. Disseminating this information to the community helps educate website owners about the latest trends and threats.
This year, we’ve included new insights to highlight the most prevalent tactics and techniques observed in compromised web environments and remote scanners.
Key takeaways
Some of the key findings from our 2022 Website Threat Research Report include:
- 50.58% of all CMS applications were outdated at the point of infection.
A more detailed look at the data shows that WordPress’ automatic updates are helping users maintain updated CMS’. 49.8% of WordPress installations were outdated at the point of infection, lower than other CMS applications in our environment.
- 36% of all compromised websites had at least 1 vulnerable plugin or theme present in the environment at the point of remediation.
This data point stresses the importance of patching and maintaining website software and third-party components to mitigate risk. Easily exploited vulnerabilities are a top choice for attackers. If they don’t require authentication, attackers are able to easily automate their attacks and monetize affected environments. By patching software to the latest version, website owners can minimize risks from bugs, known vulnerabilities, and other security threats.
- 69.63% of compromised websites were found to have at least one backdoor at the point of remediation.
Backdoors can be difficult to detect and found in a wide range of formats — it’s common to find several different types of backdoors responsible for specific tasks on a compromised server environment. In total, our team removed 1,188,864 backdoors from infected websites last year.
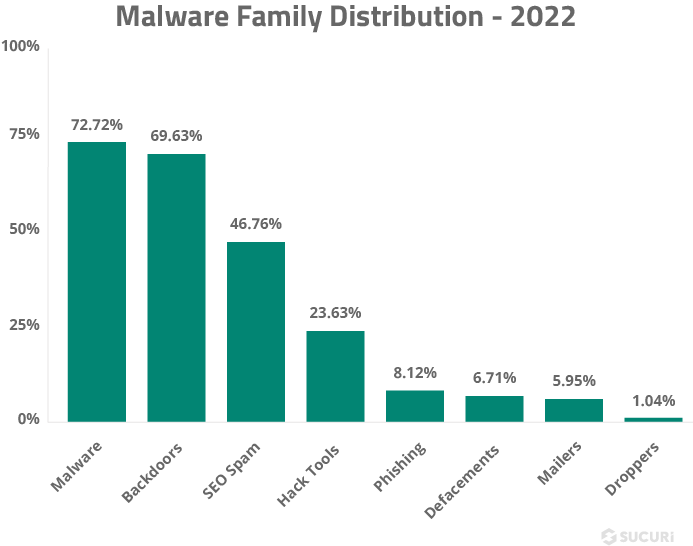
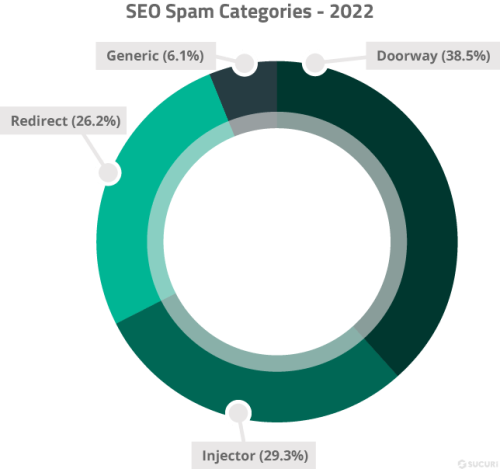
- SEO spam was detected on 46.76% of all infected websites in 2022.
SEO spam was a prevalent issue, with over 584,000 websites found to contain SEO spam during a remote SiteCheck scan in 2022. It was also the third most common malware family detected on hacked websites; 46.76% of all remediated websites were found to be infected with some form of spam, and our teams removed 4,695,695 instances of spam from files and 670,721 from compromised databases.
- 23.63% of compromised websites contained at least one hack tool.
This category is used to identify automated tool kits like AnonymousFox along with configuration stealers, DDoS attack tools, botnet scripts, mass defacement tools, and spam mailers.
- Malicious WordPress admin users were found in 32.69% of infected databases.
Our data revealed the top ten most common user names and email addresses associated with these malicious admins.
| Top 10 malicious admin usernames | Top 10 malicious admin emails |
| administratoir | wadminw@wordpress.com |
| Sendsdesr | 123@abc.com |
| AdminZaxHH34 | wp-security@hotmail.com |
| adminlin | coderbruh@protonmail.com |
| wwwadmin | gd_support@wordpress.org.com |
| superuser | support@wordpress.com |
| rxrhack1337 | email@email.em |
| controllers | mail@maill5.xyz |
| siteseomanager461 | test@test.test |
| wp-system | support@wordpress.org |
- 90% of credit card skimmers were found in the form of malicious PHP code.
This makes the skimmers impossible to detect with external scanners and highlights the importance of server-level monitoring.
- The most common infection found during remediation was malicious allow/deny rules in .htaccess files associated with Japanese SEO spam (13.48%).
These infections are renowned for infecting or creating thousands of files within a website’s environment.
Closing thoughts
The data from our 2022 report highlights the importance of keeping CMS applications, plugins, and themes up-to-date to reduce the risk of infection. The high percentage of outdated CMS applications and vulnerable plugins or themes present in compromised websites suggests that there is still work to be done in terms of patching and essential security practices to prevent infection.
To combat these threats, website owners and developers must prioritize website security, leverage 2FA on admin panels among other website security best practices, and stay informed about emerging trends and attack vectors.