Recently a client was experiencing a massive layer 7 DDOS attack, generating tens of thousands of random HTTP requests per second to the server. The architecture of the website included a cluster of three web servers responsible for handling all incoming traffic, which did little to alleviate the pressures brought about the attack.
An interesting point about layer 7 DDOS attacks, aka HTTP flood attacks, is that they have little dependency on bandwidth allowing them to easily take down a server by overloading its resources. Depending on the web server and application stack, even a low number of requests per second can choke the application and backend databases. On average, attacks greater than 100 requests per second have the potential to bring down most mid-sized websites.
Anatomy of a Layer 7 DDOS Attack
This is exactly what the client was experiencing. The attacker was hitting non-existent URLs on his site and generating requests like this:
GET /music - 404 (not found) GET /italian-wedding - 404 (not found) GET /love/you - 404 (not found) GET /bluechevy - 404 (not found) .. and thousands more random words ..
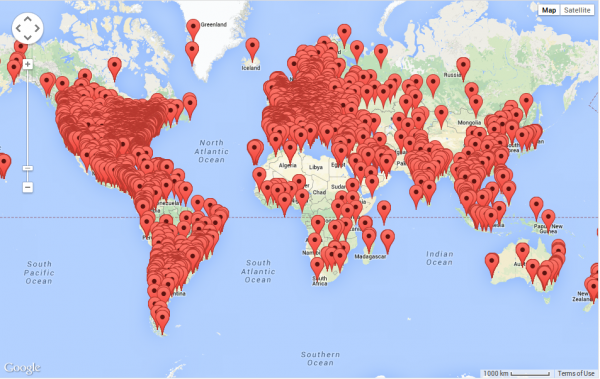
The attacks were at very high speeds and coming from various sources around the world. Here is a map of the various connections. This occurred over a short time period (few hours):
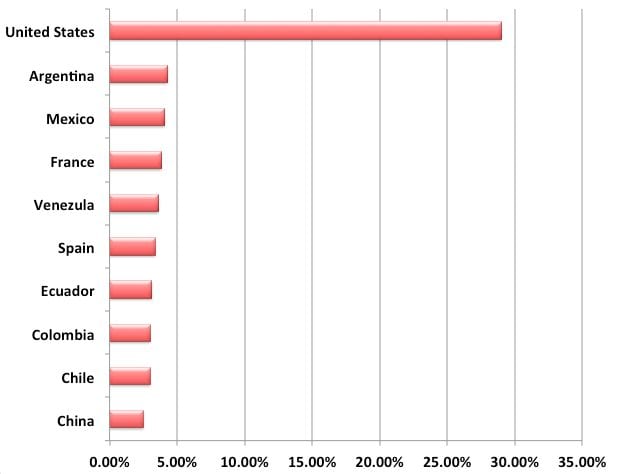
In total, we recorded a little over 29,000 unique IP addresses around the world. The US was the number one source, and below you’ll find a graph of the top ten countries associated with the attack:
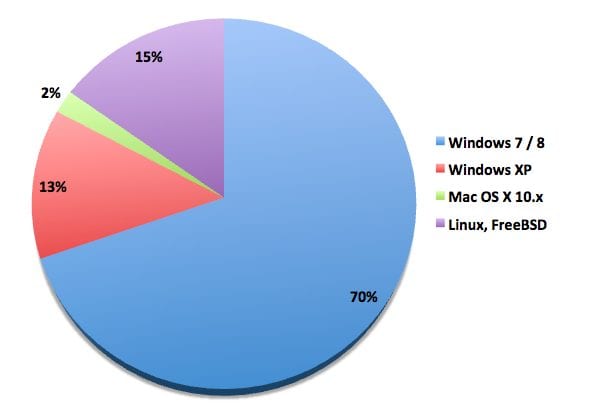
We were curious about the makeup of the attack, specifically where it was coming from. To account for this, we leveraged the p0f tool (a tool to identify the operating system of the IP addresses attacking the site). This brought about a very interesting revelation:
What we found was that 85% of the incoming IP addresses were originating from desktops and not from web servers. Approximately 15% were using Linux, FreeBSD or were not identified. This, coupled with the fact that the IPs originating from cable / ADSL providers, allows us to deduce that the client was being attacked by a large desktop botnet.
Mitigating Layer 7 DDOS Attacks
The issue with this type of attack is that server-level caching is unable to stop it. The incoming URLs are dynamic and the application forces a reload of the content from the database for every new request that is not in cache, which creates a new page. Attackers know this, making it the preferred method of attack for today’s Layer 7 DDoS attacks.
Botnet-based DDoS attacks on the application layer can limit resources, curtail revenue, and yield customer dissatisfaction, among other problems. DDoS attacks are among the most difficult problems to resolve online, especially when the target is the web server. – International Journal of Computer Appplications
To protect the client, we used our emergency DDOS protection feature, which uses JavaScript tricks to prevent malicious bots from hitting the site, while allowing access to valid users using real browsers. We combined that with our intelligent log correlation system, which allowed us to pinpoint the IP addresses and traffic pattern, blocking the incoming attack at the edge via the Sucuri Website Firewall before it was able to overload the web server.
Are You Experiencing a Layer 7 Attack?
Have you been experiencing issues like what was described above? Do you have logs you can’t make sense of? If so, we’d love to see them. If you have logs to share please send them to us at soc@sucuri.net.
If you need help protecting against DDOS attacks, please don’t hesitate to let us know.









6 comments
This is hard stuff to understand, but am I on the right track when I infer from this that botnets are made by poor security of the Windows operating systems and “regular people” with those systems falling for (clicking on) malicious links in emails? From the numbers I see in this article, it would seem Mac has superior protection against malware getting in; and so why can’t Microsoft do whatever it is Apple is doing? Is this generally correct?
The volume of Windows users are greater than the volume of Apple users. It is not about the system itself..it’s all about people awareness.
The type of botnet used in this case is simply a collection of computers used to attack this site using a DDOS attack. The reason for the high percentage of Windows computers is due to the market share of operating systems as well as the number of vulnerabilities that Windows operating systems have. Since Windows has a much larger market share in regards to operating systems, hackers are going to spend more time on exploiting it, the software compatible with it, etc. since they have “hack” more people, make more money, etc. The large percentage of Windows computers isn’t due to Windows operating systems being “insecure” per say.
With security of Windows systems I would recommend using a free antivirus such as Microsoft Security Essentials or Avast, Malwarebytes AntiMalware Pro, Windows Firewall, and Malwarebytes Anti-Exploit. Keep your programs up to date with Filehippo Update Checker, have a basic sense of security/scams/etc., and use common sense. If you don’t need Java, QuickTime Player, or any other programs you don’t need uninstall them. Use Firefox or Google Chrome as your browser as well. If you do those things, you should protect yourself from most threats.
DDoS tools run JavaScript these days…
> JavaScript tricks to prevent malicious bots from hitting the site
you mean like roboo.pm, or do you roll your own?
I have just finished reading the article you wrote on Ddos attacks, Ddos attack & Botnet-based DDoS attacks. I want to tell you how much I appreciated your clearly written and thought-provoking article.
Comments are closed.