If you have poked around a server before you have probably encountered file permissions. In fact, all computer file systems offer permissions based on the same core ideas. The file permissions in Linux, Mac, and Windows computers are very similar to the file and folder permissions in Apache, Nginx, and IIS servers. You can right-click any file on your computer and choose Properties (Windows) or Get Info (Mac) to see an example. You can also log into your server (using an FTP client like FileZilla) to do the same thing to your server files and directories.
For the purposes of this article, we’ll be discussing website files and folders on your server.
You may have heard references to things like chmod, 775, read/write, or user groups. This post is going to explain the bare bones of permissions, giving you clarity into these terms. This is important for those of us who are just starting to interact with servers, and for those who have always been curious to know more about file permissions. Ultimately, knowing how permissions work on your server will strengthen your security posture. In other words, knowledge about security concepts helps you develop a keen sense that stops you from doing things like granting full 777 permissions on a file (even if your theme documentation tells you to), or noticing when you have strange file permissions that could be the warning signs of an intruder.
Who Can Do What
No matter which file system you use, it has its own set of permissible actions for specific user categories.
User Categories
There are three categories of users who can have access to files on your server.
- Owner: The first user category is a single user, often the one who created the file.
- Group The second category includes groups of other FTP users on your server.
- Public: The last category includes external visitors without FTP accounts.
These groups are each assigned a single digit which signifies their permission levels. If you put all three numbers together, this gives us the permission code.
User Category Combination Example
Permission Code is 123:
- 1 = Owner
- 2 = Group
- 3 = Public
So we have a code of three digits, but what do the individual numbers mean? Contrary to what you might think, the levels do not simply go from 0-9 – oh no, there is some math to do. Sorry.
Permission Actions
There are three actions that require permission, each is represented by a number.
- 4 – Read: To simply view a file.
- 2 – Write: To make changes to a file.
- 1 – Execute: To run a program file.
- 0 – No Permissions: No one can do anything, only the owner can change permissions.
These permissions can be added together to grant multiple permissible actions to the same user category.
Permission Action Combinations Examples
- 7 = (4 + 2 + 1) = Full Access (read + write + execute)
- 6 = (4 + 2) = No Execute (read + write)
- 5 = (4 + 1) = No Write (read + execute)
- 3 = (2 + 1) = No Read (write + execute)
Changing File Permissions
To change file permissions, right-click any file or folder on your server in FileZilla (or your FTP client of choice). Open the File Permissions… and you should see this:
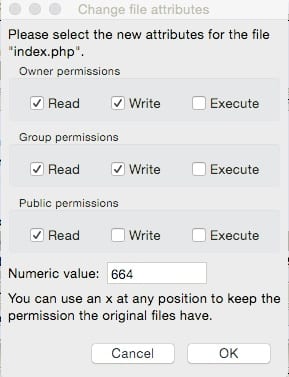
You can check the boxes, or type the three-digit code to set the owner/group/public permissions.
If you want to use SSH to access your website, you can use the chmod command, followed by the permission code, and the name of the file you want to change.
File Permission Tips
- Before changing permissions, note the current 3-digit permission code. You can easily change the code back if the new permissions cause any problems.
- Most files should have permissions of 644 (owner can write, no one can execute).
- Some files contains your secret database configuration information (eg. wp-config.php) and may benefit from additional restrictions like 660 if your server allows.
- Most folders should have permissions of 755 (execute allows you to open the folder).
- Change permissions only when you need more access, then change them back after.
- If your CMS needs write access to a file, this likely means that the Group user needs Write permissions.
- Avoid folders with 777 and no files with 666. Some plugins, themes, and forums offer this “advice” to solve permission errors, but it gives everyone access to write or erase your files. This is like leaving your door unlocked.
This is just scratching the surface of file permissions. There can be several user groups on your server and you can change which groups have access to certain files. This is where being a sysadmin starts to get intricate, and you can find a lot of opinions online as well as established methods for using file permissions.
Do you have any burning questions or best tips for your server file permissions?
Leave a comment below!








1 comment
I try to not have root own any web files. No. Another user under the apache group will own the file, and permissions are set so that the file is executed or read or whatever by that user/group. I’m not sure if this helps, but I figure if apache cannot run the files without root, I gotta fix the way the files run, and it’s not a safe thing to have root run things if it can be avoided.
Comments are closed.