We leverage OSSEC extensively to help monitor and protect our servers. If you are not familiar with OSSEC, it is an open source Intrusion Detection System (HIDS); it has a powerful correlation and analysis engine that integrates log analysis, file integrity monitoring, centralized policy enforcement, rootkit detection, real-time alerting, and active response.
It provides complete coverage if you are looking for an endpoint (server) security solution. If you have not used OSSEC before, I recommend reading my guide to get started: http://dcid.me/texts/my-ossec-setup-manual.html
OSSEC requires root access to your servers and is meant for network / server administrators with Linux skills.
Getting WordPress Visibility
WordPress is becoming very popular in the enterprise world, but a common issue that security administrators have is with visibility into platform events. System administrators want to know what is happening inside WordPress and how those events can be incorporated into their log management and log-based intrusion detection plan.
WordPress Security Audit Log Trail
A great way to help address this issue can be found in our Free WordPress Security plugin, which is available in the WordPress repository and is also open-source. Our plugin focuses on providing the desired visibility within the WordPress platform. The plugin will hook into multiple WordPress actions and log sensitive actions, such as:
- Successful logins
- Failed logins
- Post or Pages being published
- Plugins or themes being installed or removed
- Files being modified
- Categories being created
These and many other CMS-specific activities would just be lost without the audit trail.
Install the WordPress Plugin
Installing the plugin is easy. We’ve put together a quick guide here that will that help in the process of using it.
- Log into your WordPress dashboard (or wp-admin).
- Navigate to Plugins and click Add New.
- Search for “sucuri-scanner” in the search box.
- Find the plugin and click Install Now on Sucuri Security – Auditing, Malware Scanner and Security Hardening.
The name of the plugin is a bit unrelated, as it used to be a front-end for our free malware scanner, SiteCheck. The audit trail is what provides us the visibility we’ll be focusing on in this article.
Once installed, the audit logs will populate within the Sucuri dashboard in your WordPress installation.
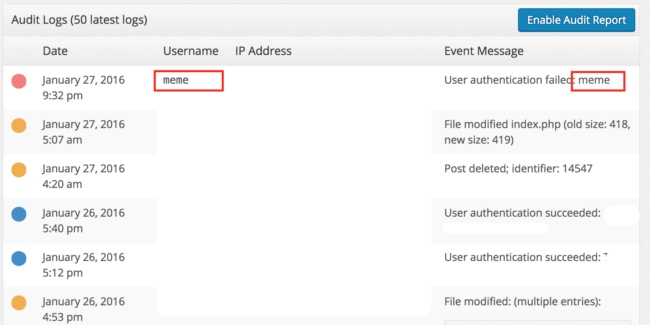
Integrating OSSEC with WordPress
Having basic visibility is not enough though. Most system administrators have existing log management tools and systems in place that are designed to aggregate information. Until now, this capability has been limited.
In our latest release however, we have introduced a new way to export all those event activities so that you transfer that visibility from within your WordPress dashboard into your OSSEC installation (or other log management tool). For once, you can get visibility into WordPress itself, and you can export data to a log file that can be read by OSSEC or any other log management tool.
How to Export WordPress Logs to OSSEC
Navigate to the plugin Settings -> Log Exporter page and provide a path to export the audit trails as they happen.
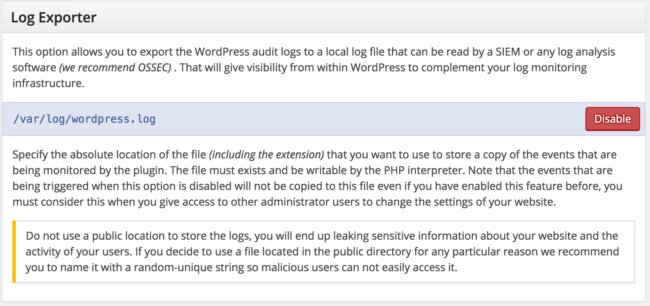
In the example above, the location /var/log/wordpress.log was set, which means all events will be captured at that location on the server.
From there, add the log file to OSSEC to be monitored in real time and restart OSSEC:
# /var/ossec/bin/util.sh addfile /var/log/wordpress.log
# /var/ossec/bin/ossec-control restart
That’s it. Now all WordPress-related activity will start populating the log file and consumed by OSSEC. For example, on the Sucuri blog, I can see when I am logging in:
** Alert 1453833644.78336: – syslog,wordpress,authentication_success,
2016 Jan 26 13:40:41 (blog.sucuri.net) HIDDEN->/var/log/wordpress.log
Rule: 9502 (level 3) -> ‘WordPress authentication succeeded.’
Src IP: HIDDEN / USA
2016-01-26 13:40:41 WordPressAudit blog.sucuri.net HIDDEN : Notice: 1.2.3.4; User authentication succeeded: danielcid
I can also see when someone is failing at entering their password or editing anything inside WordPress.
If you leverage Slack or PagerDuty, be sure to update your OSSEC install with the latest integrator daemon, it pushes all alerts to either medium per your configuration:
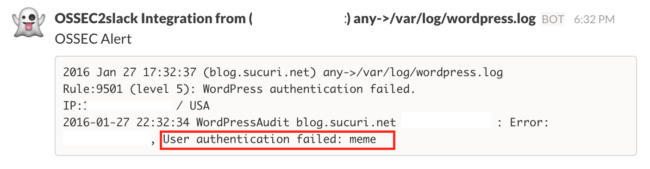
Try it and let us know how it goes. Note that for this feature to work, you have to use our fork of OSSEC from here:
http://dcid.me/ossec
You can download the latest version there directly, or get it from our repository.









5 comments
Interesting stuff Daniel. Will definitely give it a try. Thanks for sharing
Let us know how it goes. thanks,
Hi Daniel, Besides cudo’s on the plugin, very informative article! Noticed some new info in there 🙂 …. I am already parsing all WP logs straight on the server, as well as using AR on malicious behaviour and FS integrity (all with OSSEC). Are there specific difference the plugin can catch that I can not on the OS level? … I would think you can ‘see’ more when hooking into the WP internals .. Greetings. Keep up the good work!!
It is mostly the hooking inside WordPress so you can track internal activities that do not happen at the OS/FS level and get stored in the database only. Things like new posts, new pages, content being published, logins, etc.
Hello everyone, I have tried hackingenius8@gmail.com and i have confirmed his good work among all of this hackers out there ,he helped me back my cheating partner whatsapp, facebook and cell phone number. I listened to all his calls and I was able to get good evidence for my attorney for divorce. It was really a big surprise to me but glad I gave a try. Contact him for similar issues on hackingenius8@gmail.com and consider your big problem solved.
Comments are closed.